LockBit Ransomware
LockBit Ransomware Image
Ransomware threats are running rampant on the Web. Countless users have reported that their data has been encrypted by a data-locking Trojan. Unfortunately, it is not likely that we will see the end of the epidemic any time soon. One of the newest threats of this type has been dubbed the LockBit Ransomware. This nasty Trojan is capable of locking all the data present on a compromised system very quickly.
Propagation and Encryption
It does not seem that the LockBit Ransomware is a copy of any of the popular ransomware threats active currently. The infection methods used in the propagation of the LockBit Ransomware have not yet been determined. However, authors of ransomware tend to rely on spam email campaigns to spread their creations mainly. The emails tend to consist of a fraudulent message that aims at convincing the target to launch the attached file. However, the attachment is usually a macro-laced file that will infect the target’s system upon launching. There are other propagation methods that are often used in the distribution of file-encrypting Trojans – pirated software, torrent trackers, fake application downloads and updates, etc. Regardless of how the ransomware threat has been delivered to the compromised machine, the Trojan will make sure to scan all the data that is present on the system. Usually, data-locking Trojans target a very long list of file types that are normally found on the system of any regular user. This will increase the chances of the victim paying up the ransom fee. When the LockBit Ransomware encrypts a file, it also alters its name by appending a ‘.abcd’ extension at the end of their names. For example, an image you had named ‘sunset-hills.jpeg’ will be renamed to ‘sunset-hills.jpeg.abcd’ after the encryption process of the LockBit Ransomware is completed.
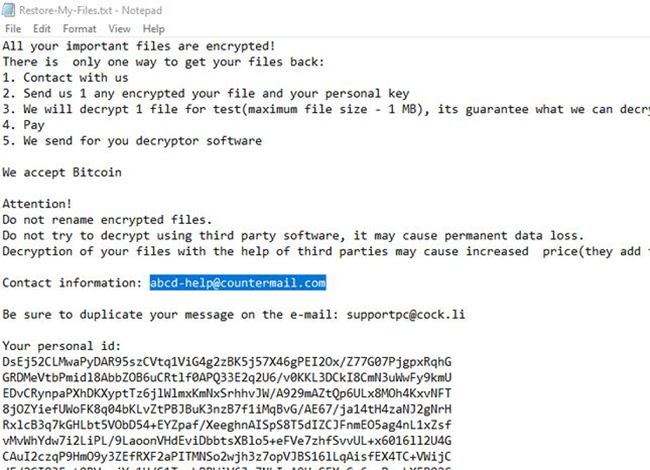
The Ransom Note
The LockBit Ransomware’s ransom message is contained in a file named ‘Restore-My-Files.txt.’ This file is dropped on the user’s desktop. The ransom note is rather concise and to the point. In it, the attackers state that they would like to be paid in Bitcoin but do not mention a specific ransom fee. The authors of the LockBit Ransomware demand to be contacted via email and have provided two email addresses – ‘supportpc@cock.li’ and ‘help@countermail.com.’ As proof that they are in possession of a fully-functioning decryption key, the authors of the LockBit Ransomware claim that they are willing to unlock one file for free.
We would advise you to stay away from the creators of the LockBit Ransomware. These people are not to be trusted, and even if you pay the ransom fee, there is a high chance you will never receive the decryption key promised. This is why you should consider obtaining a reputable anti-virus software solution that will remove the LockBit Ransomware from your computer and ensure your safety in the future.


