Lockbit 2.0 Ransomware
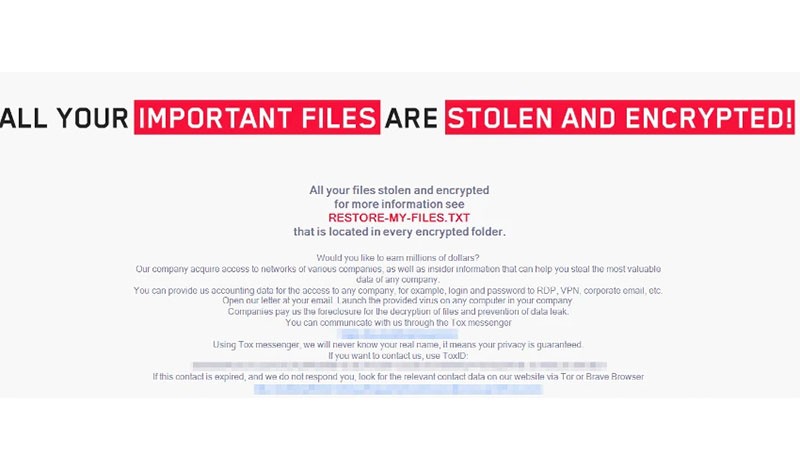
The LockBit Ransomware emerged on the malware landscape back in September 2019, when it was offered in a RaaS (Ransomware-as-a-Service) scheme. The operators of the threat were looking for affiliates who would carry out the actual ransomware attacks and then split the profits - the affiliates would bag around 70-80% of the funds while the rest would be given to the LockBit creators.
The operation has remained quite active since its launch, with the representatives of the group behind the threat maintaining a presence on the hacker forums. When several prominent forums decided to distance themselves from ransomware schemes and banned the discussions of such topics, LockBit moved on to a newly created data leak site. There, the cybercriminals unveiled the next version of their threatening creation - LockBit 2.0, which also would be offered as RaaS. The 2.0 version boasts massively expanded harmful capabilities with the hackers incorporating multiple features that have emerged in other ransomware families previously. On top of that, the threat is equipped with a never before see technique that allows it to abuse group policies to encrypt Windows domains automatically.
LockBit 2.0's Exhibits Novel Techniques
LockBit 2.0 is still ransomware, and as such, its aim is to infect as many devices connected to the breached network as possible, before encrypting the data stored there and demanding a ransom. However, instead of relying on third-party open-source tools, which is the standard practice in these operations, LockBit 2.0 automated its distribution and anti-security measures. Upon its execution, the threat will create several new group policies on the domain controller, which are delivered to all machines connected to the compromised network subsequently. Through these policies, the malware is able to disable the real-protection feature of Microsoft Defender, as well as the alerts, default actions, and the samples usually sent to Microsoft upon detecting an unwelcomed intruder. It also establishes a scheduled task to launch its executable.
The next step of the operation sees the executable file of LockBit 2.0 being copied to the Desktop of each detected device. The previously created scheduled task will initiate it by implementing a UAC (User Account Control) bypass. This method allows LockBit 2.0 to move through its programming stealthily, without triggering any alerts that might attract the attention of the user.
When the encryption process is completed, LockBit 2.0 activates a feature that was previously observed as part of the Egregor Ransomware threats. It involves forcing all printers connected to the network to spew out the ransom note of the threat endlessly.

