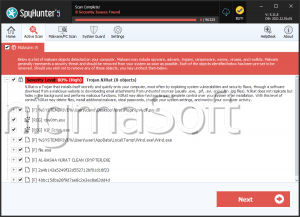
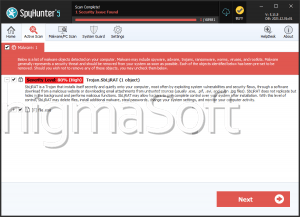
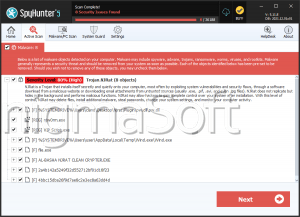
jRAT
jRAT is a RAT (Remote Access Trojan) that is written in the JAVA language, which would make it compatible with nearly all operating systems, provided that the infiltrated computer has JRE (Java Runtime Environment) installed. Despite its capability to work with several operating systems, the main target of the jRAT remains machines running Windows.
Malware experts first discovered this threat about two years ago – back in 2017. The creators of the jRAT have not been idle, though, and have introduced a few updates of their creation over the years. These updates included VM-evasion methods alongside several new features. The infection vector utilized by the authors of the jRAT appears to be spam email campaigns containing a '.jar' file, which carries the threat.
If the victims attempt to open the infected file, they will give the green light to the jRAT, and the threat would scan their systems to check if there is a firewall configuration or the user has installed an anti-malware tool. Then, to gain persistence, the jRAT will drop another '.jar' file in the Windows %TEMP% folder, which is meant to run the jRAT every time that the system is rebooted. When this is done, the jRAT collects data about the system it has landed on and siphons it to the servers operated by the attackers.
The jRAT is capable of operating as a keylogger, taking screenshots of the desktop, modifying the files existing on the compromised system, downloading and executing new files, manipulating the Windows voice feature, and using the Web camera to spy on its victim.
This may not be the most advanced or complex RAT out there, but it can do a lot of harm with the features it boasts certainly. It is absolutely crucial that users online take their cybersecurity seriously and make sure to download and install a reputable anti-spyware application and keep in mind that it needs to be updated regularly to ensure maximum safety.