Trojan.NJRat
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 6,439 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 7,245 |
| First Seen: | August 12, 2016 |
| Last Seen: | January 31, 2026 |
| OS(es) Affected: | Windows |
NJRat is a Trojan horse application that falls under the category of a Remote Access Trojan/Remote Administration Tool (RAT), which are threats known to load on a system without any indication to the computer user where it may allow remote attackers to gain access to the infected system.
The actions of NJRat are similar to that of popular Trojan horses where it could collect data from the infected computer, which may include usernames, passwords, system details, and other information that may be personal to the computer user. Such data that is collected by NJRat may be accessed by remote hackers, which could then lead to cases of identity theft.
One of the more discerning aspects of NJRat is that it could download other malicious programs on the infected computer, which include ransomware-type threats or other unknown malware that perform malevolent activates over the Internet.
Fundamentally, malicious actions of Trojan.NJRat vary and are all in an attempt to wreak havoc on a computer and potentially steal personal information.
Table of Contents
How does NJRat end up on your computer?
The installation of NJRat may take place through spam campaigns that spread spam messages that contain malicious file attachments. Many of the file attachments may be in the form of MS office documents, PDF files, ZIP files, and even executables that appear to be harmless to most computer users. Avoiding the installation of NJRat may be as simple as paying special attention to attachment files or avoid potentially malicious sites that may offer downloaded third-party apps.
The removal of NJRat is a difficult task in most cases for even the savvy computer user. Due to NJRat having stealth-like advantages over other malware threats, it may not be easy to identify the threat and delete it from a Windows PC. Using an antimalware resource will suffice to safely detect and eliminate NJRat along with any of its associated malware files on an infected system.
SpyHunter Detects & Remove Trojan.NJRat
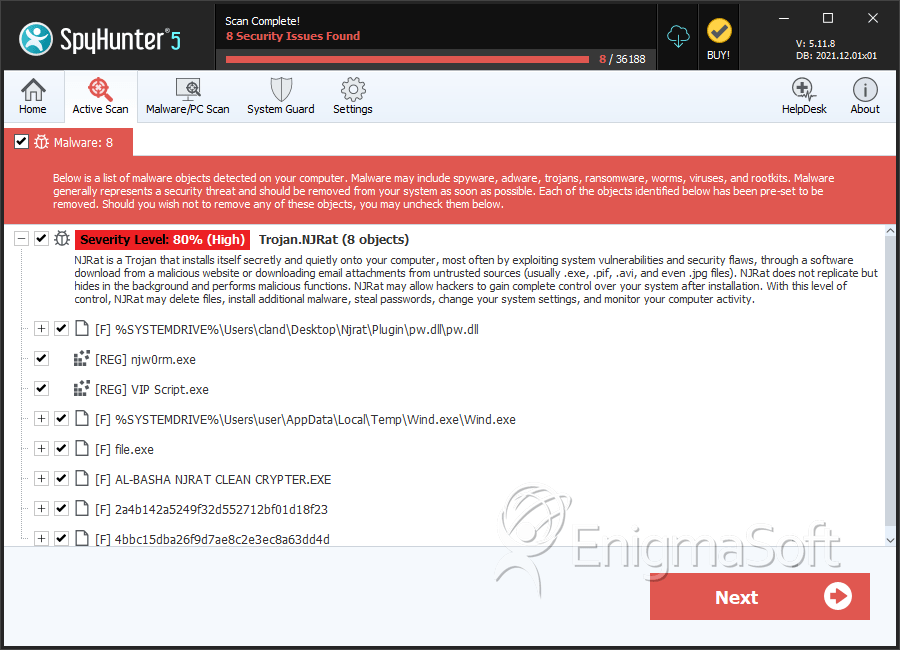
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | pw.dll | db87daf76c15f3808cec149f639aa64f | 869 |
| 2. | Mono.Cecil.dll | 851ec9d84343fbd089520d420348a902 | 260 |
| 3. | Wind.exe | 53a9de48e432d5587bb93bc5a8c7bb8b | 1 |
| 4. | AL-BASHA NJRAT CLEAN CRYPTER.EXE | 98ff2a318c13d486f34f81459f9d5fc8 | 0 |
| 5. | 2a4b142a5249f32d552712bf01d18f23 | 2a4b142a5249f32d552712bf01d18f23 | 0 |
| 6. | 4bbc15dba26f9d7ae8c2e3ec8a63dd4d | 4bbc15dba26f9d7ae8c2e3ec8a63dd4d | 0 |
| 7. | file.exe | a9f81658b17624154c7936935b3bb6b1 | 0 |
Registry Details
Analysis Report
General information
| Family Name: | Trojan.NJRat |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
c2e98fefd702a795df473cd5c4fa1a06
SHA1:
a3d4b5acd49595323a70669f2d95bdf7c00d6e7f
File Size:
44.03 KB, 44032 bytes
|
|
MD5:
aacb4ea51663d606f4ab72a35c42c9a4
SHA1:
7fbfca8d150f7ff1a98e7e6fbe46250a0302549b
File Size:
44.03 KB, 44032 bytes
|
|
MD5:
8fedbd58c4408647d660a1a68643e354
SHA1:
0731fd0d5df5afc9d20181d4cc55fa9c0c255813
SHA256:
0B6DD4586D6355828F0EBADAD74D464AFBF9BB8F87FBCB9FA3B0C69384B49087
File Size:
176.13 KB, 176128 bytes
|
|
MD5:
05e352ab24f8dbb161a24b5e97392c3b
SHA1:
ae9352b505a59b961c89e266828dd3269e3cdfe4
SHA256:
955C87FC402849E6CF97B46819EA624A2CEEB99BE6D1661E3F4F90A9F5B254AB
File Size:
44.03 KB, 44032 bytes
|
|
MD5:
100e1cdb67a53f333b5416363b7fc28f
SHA1:
94abcd9094b4ef36b117871198b385497b686456
SHA256:
D57A9DC8277FF5CEDAED8CB9B6D6E2A056577CF360A278CB92C9B73E145B4DD5
File Size:
86.02 KB, 86016 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have security information
- File is .NET application
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
Show More
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Traits
- .NET
- NewLateBinding
- No Version Info
- ntdll
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 122 |
|---|---|
| Potentially Malicious Blocks: | 11 |
| Whitelisted Blocks: | 38 |
| Unknown Blocks: | 73 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Registry Modifications
Registry Modifications
This section lists registry keys and values that were created, modified and/or deleted by samples in this family. Windows Registry activity can provide valuable insight into malware functionality. Additionally, malware often creates registry values to allow itself to automatically start and indefinitely persist after an initial infection has compromised the system.| Key::Value | Data | API Name |
|---|---|---|
| HKCU::di | ! | RegNtPreCreateKey |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| User Data Access |
|
| Keyboard Access |
|
| Syscall Use |
Show More
|
| Anti Debug |
|
