njRAT Lime Edition
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 6,478 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 7,241 |
| First Seen: | August 12, 2016 |
| Last Seen: | January 22, 2026 |
| OS(es) Affected: | Windows |
The njRAT Lime Edition is a Remote Access Trojan that has ransomware capabilities apart from allowing cybercrooks to gain remote access to the infected computers. The njRAT Lime Edition was first observed on December 6, 2017. The njRAT Lime Edition includes an encryption engine that makes the victim's files useless, allowing its perpetrators to demand ransom payments from their victims, as well as backdoor capabilities that allow the cybercrooks to gain access to the infected PC.
Table of Contents
The Sour Taste of a njRAT Lime Edition Infection
The njRAT Lime Edition is being advertised on the Dark Web, as well as on various hacking websites and videos on the open Internet. Developed by someone going by the handle 'Mr3x3,' the njRAT Lime Edition is being advertised as having the following features in its attack (this text is part of the njRAT Lime Edition's advertising material):
[+]Added Ransomware
[+]Added Stress Test \\ slowloris and ARME
[+]Added PC specification \\ Get info CPU GPU RAM
[+]Added BTC wallet finder
[+]Added Changing Wallpaper
[+]Smarter USB Spread
[+]Smarter [Logs]
[+]Updated anti-process \\ Now if you click ON this make it always on even after restart until you press OFF
[+]Updated bitcoin \\ Also ON will make it run after restart until OFF is pressed
[+]Fixed MessageBox not being showed on top
[+]Fixed Copy To startup
[+]Fixed Active Window weird symbols
[+]And more bugs were Fixed
[+]Updated Support Folder \\ Now it's cleaner and easy to read
It seems that the main attraction of the njRAT Lime Edition is the addition of a ransomware feature, which allows the cybercrooks to make money from having infected the victim's computer immediately. The njRAT Lime Edition displays the following ransom note on victims' computers:
'All your files have been locked
You can get them back, Just pay us 200$ as Bitcoin
Our bitcoin address is
BTC TEST 12345678990000120233
Watch this video to learn how to pay us https://www.youtube.com/watch?v=Ji9IwPId5Uk
This is not e joke. This is a ransomware'
How the njRAT Lime Edition Attack Works
The njRAT Lime Edition is associated with a threat building kit that the cybercrooks can use to create personalized versions of the njRAT Lime Edition. The njRAT Lime Edition marks the files encrypted in its attack by adding the file extension '.Lime' to the end of each affected file's name in its default version. The njRAT Lime Edition has all of the features of a backdoor Trojan coupled with the features of an encryption ransomware Trojan. Like most backdoor Trojans, the njRAT Lime Edition is designed to allow the cybercrooks to gain remote access to infected computers. The njRAT Lime Edition also allows third parties to monitor the victim's activities, gather data, and collect information, as well as control the infected computer from a remote location. Additionally, the njRAT Lime Edition's ransomware module allows the cybercrooks to carry out ransomware attacks. The njRAT Lime Edition will use a strong encryption algorithm to make the victim's files out of reach, and then demand that the victim pays a ransom of 200 USD in exchange for the decryption key, which is needed to restore the affected files. This combination allows these people to carry out devastating attacks on their victims.
Protecting Your Computer from Threats Like the njRAT Lime Edition
The best protection against backdoor Trojans like the njRAT Lime Edition is to have a strong security program that is fully up-to-date and take precautions when handling any suspicious material, such as unsolicited email attachments or online links. To protect yourself and your machine against ransomware Trojans, you must have file backups. If a Trojan like the njRAT Lime Edition encrypts your files, having the ability to restore your files from a backup copy means that there is no need to contact the cybercrooks or pay the ransom to recover from a njRAT Lime Edition attack. A combination of strong security software and reliable backup methods is proven to be the best method to protect your data from the njRAT Lime Edition.
SpyHunter Detects & Remove njRAT Lime Edition
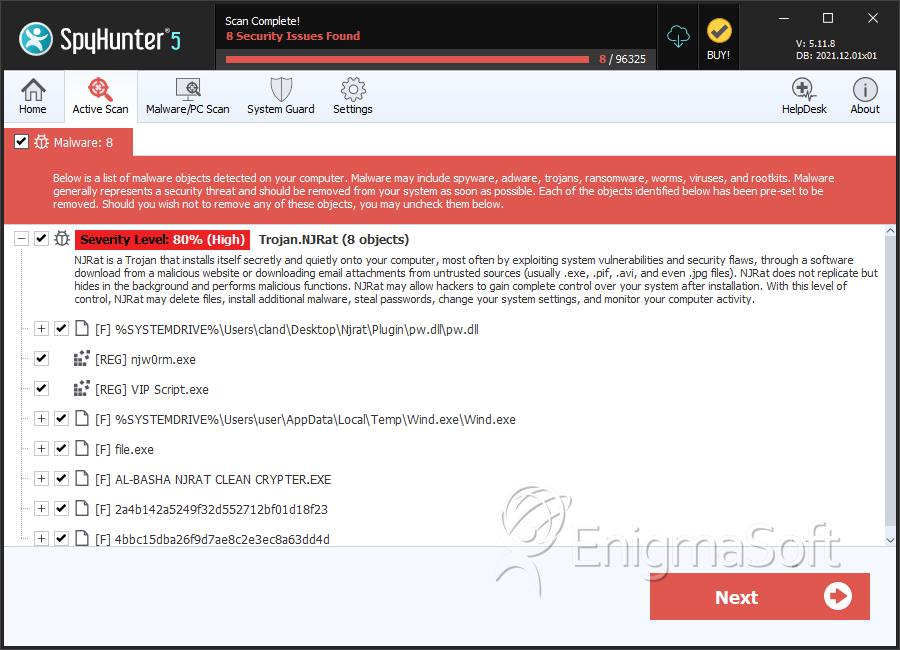
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | pw.dll | db87daf76c15f3808cec149f639aa64f | 869 |
| 2. | Mono.Cecil.dll | 851ec9d84343fbd089520d420348a902 | 259 |
| 3. | Wind.exe | 53a9de48e432d5587bb93bc5a8c7bb8b | 1 |
| 4. | AL-BASHA NJRAT CLEAN CRYPTER.EXE | 98ff2a318c13d486f34f81459f9d5fc8 | 0 |
| 5. | 2a4b142a5249f32d552712bf01d18f23 | 2a4b142a5249f32d552712bf01d18f23 | 0 |
| 6. | 4bbc15dba26f9d7ae8c2e3ec8a63dd4d | 4bbc15dba26f9d7ae8c2e3ec8a63dd4d | 0 |
| 7. | file.exe | a9f81658b17624154c7936935b3bb6b1 | 0 |
Registry Details
Analysis Report
General information
| Family Name: | Trojan.NJRat |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
c2e98fefd702a795df473cd5c4fa1a06
SHA1:
a3d4b5acd49595323a70669f2d95bdf7c00d6e7f
File Size:
44.03 KB, 44032 bytes
|
|
MD5:
aacb4ea51663d606f4ab72a35c42c9a4
SHA1:
7fbfca8d150f7ff1a98e7e6fbe46250a0302549b
File Size:
44.03 KB, 44032 bytes
|
|
MD5:
8fedbd58c4408647d660a1a68643e354
SHA1:
0731fd0d5df5afc9d20181d4cc55fa9c0c255813
SHA256:
0B6DD4586D6355828F0EBADAD74D464AFBF9BB8F87FBCB9FA3B0C69384B49087
File Size:
176.13 KB, 176128 bytes
|
|
MD5:
05e352ab24f8dbb161a24b5e97392c3b
SHA1:
ae9352b505a59b961c89e266828dd3269e3cdfe4
SHA256:
955C87FC402849E6CF97B46819EA624A2CEEB99BE6D1661E3F4F90A9F5B254AB
File Size:
44.03 KB, 44032 bytes
|
|
MD5:
100e1cdb67a53f333b5416363b7fc28f
SHA1:
94abcd9094b4ef36b117871198b385497b686456
SHA256:
D57A9DC8277FF5CEDAED8CB9B6D6E2A056577CF360A278CB92C9B73E145B4DD5
File Size:
86.02 KB, 86016 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have security information
- File is .NET application
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
Show More
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Traits
- .NET
- NewLateBinding
- No Version Info
- ntdll
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 122 |
|---|---|
| Potentially Malicious Blocks: | 11 |
| Whitelisted Blocks: | 38 |
| Unknown Blocks: | 73 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Registry Modifications
Registry Modifications
This section lists registry keys and values that were created, modified and/or deleted by samples in this family. Windows Registry activity can provide valuable insight into malware functionality. Additionally, malware often creates registry values to allow itself to automatically start and indefinitely persist after an initial infection has compromised the system.| Key::Value | Data | API Name |
|---|---|---|
| HKCU::di | ! | RegNtPreCreateKey |
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| User Data Access |
|
| Keyboard Access |
|
| Syscall Use |
Show More
|
| Anti Debug |
|
