J3ster Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 4 |
| First Seen: | October 19, 2021 |
| OS(es) Affected: | Windows |
Infosec researchers have identified a new malware threat tracked as J3ster Ransomware. Being classified as ransomware means that the threat is designed to scan victims' computers and then lock the files stored there with an uncrackable encryption algorithm specifically. Affected users will find themselves no longer able to access their photos, images, documents, as well as all archives, databases, PDFs and more. The goal of the hackers is to then extort the victims for money by promising to help them restore the locked data after making the demanded payment.
As part of its threatening activities, the J3ster Ransomware also will mark the locked files by changing their original names. The threat will append '.j3ster' as a new file extension. When all targeted file types have been encrypted, the malware will proceed to change the current desktop background with an image of a jester. It also will generate a file named 'J3ster ReadMe.txt' on the infected system's desktop. This file carries the ransom note with instructions for the victims.
Table of Contents
Demands Overview
The ransom-demanding message delivered by J3ster Ransomware is relatively brief. However, it does contain the most important information that these ransom notes carry. It reveals that the hackers want to receive exactly $1000 if they are to offer assistance with the decryption of the locked data. The money must be transferred to the provided crypto-wallet address and the transaction must be done using the Bitcoin cryptocurrency. Victims are then expected to provide evidence of the payment in the form of a screenshot. The attackers will wait to receive the proof attached to a message sent to their email address at 'j3stertools@gmail.com.'
The full text of the ransom note is:
'--- J3ster Ransomware ---
Youre Pc Has been Infected By J3ster Ransomeware Pay 1000$ To the Following Bitcoin Adress And Send An ScreenShot From youre payment To the Email
E-Mail : j3stertools@gmail.com
Bitcoin Adress : 17CqMQFeuB3NTzJ2X28tfRmWaPyPQgvoHV
Good Luck!'
SpyHunter Detects & Remove J3ster Ransomware
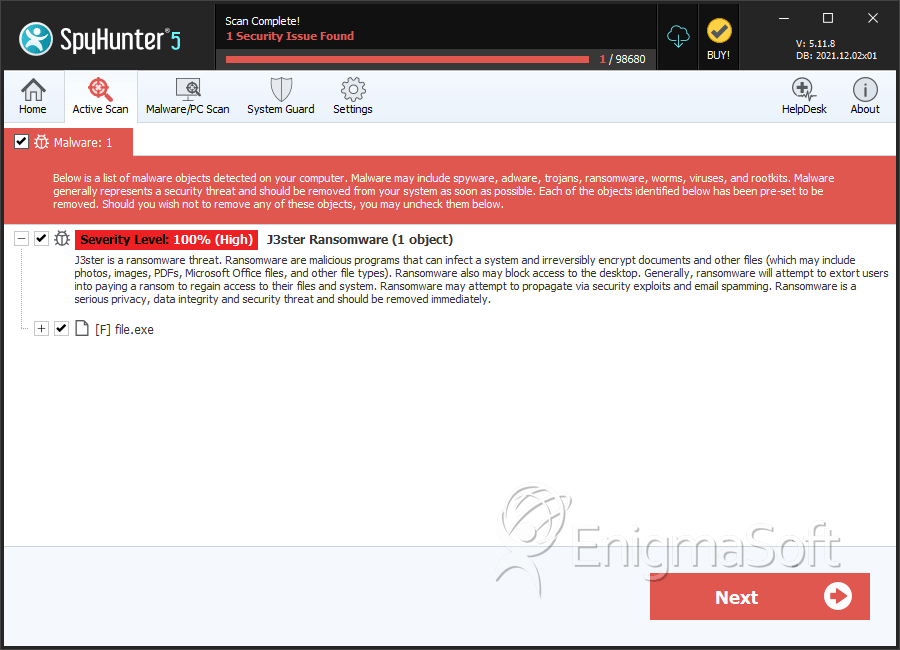
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | aa07d3711d0504e3fb769340d25d3aca | 4 |

