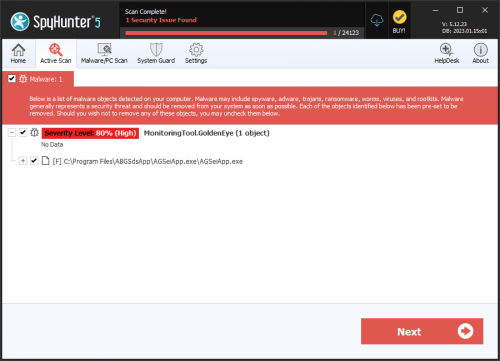
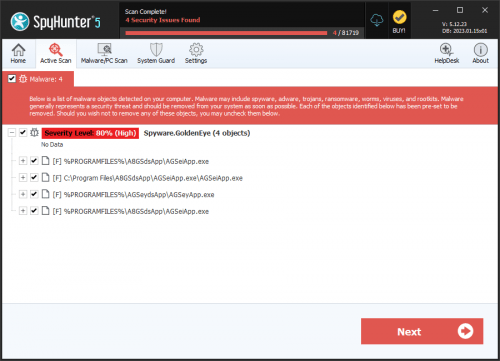
GoldenEye Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 224 |
| First Seen: | December 7, 2016 |
| Last Seen: | July 15, 2023 |
| OS(es) Affected: | Windows |
The GoldenEye Ransomware is an encryption Trojan that is pushed as an improved version of the Petya Ransomware, which surfaced in March 2016. The GoldenEye Ransomware was brought to the attention of security researchers in December 2016. Spam emails aimed at human resource departments were found to carry a corrupted spreadsheet that featured a macro. As you well know by now, the macro is widely abused by threat actors to deliver threats like the Al-Namrood Ransomware and the Osiris Ransomware. PC users that work with CVs on a daily basis appear to be among the primary targets of the GoldenEye Ransomware since they are likely to open a document from an unknown sender.
Table of Contents
Fake CVs and Spreadsheets Deliver the GoldenEye Ransomware to Computers
The macro script used to deliver the GoldenEye Ransomware is designed to write base64 encoded strings into an executable file that is stored in the Temp directory. Additionally, a VBA script is created that loads the executable into the system memory and the encryption process is initiated. The GoldenEye Ransomware works a bit different than the Mischa Ransomware which is another variant of the Petya Ransomware. The GoldenEye Ransomware is programmed to encrypt all files on the local drives using an AES-256 cipher. The GoldenEye Ransomware Trojan avoids directories that contain system data such as:
- Windows
- Program Data
- Program Files
- Program Files (x86)
- Volume Information
A Random 8-Characters Extension is Appended to Encoded Files
For example, 'Cobalt blue.docx' is enciphered to 'Cobalt blue.docx.84YpQ8z0' while 'Ultramarine violet.docx' is converted to 'Ultramarine violet.docx.2b8r6K2g'. If the GoldenEye Ransomware manages to elevate its system privileges, it attempts to install a rootkit. The rootkit is designed to lock the access to the computer entirely by encrypting the drive's MFT (Master File Table - a kind of address book for your data). Then a custom boot loader is introduced, and YOUR_FILES_ARE_ENCRYPTED.TXT is loaded on the screen, which reads:
'You became victim of the GOLDENEYE RANSOMWARE!
The files on your computer have been encrypted with an military grade encryption algorithm. There is no way to restore your data without a special key. You can purchase this key on the darknet page shown in step 2.
To purchase your key and restore your data, please follow these three easy steps:
1. Download the Tor Browser at "https://www.torproject.org/". If you need help, please google for "access onion page".
2. visit one of the following pages with the Tor Browser: http://golden5a4eqranh7.onion/ http://goldeny4vs3nyoht.onion/
3. Enter your personal decryption code there:
[instruction what field to use on the portal]'
The Best Protection against the GoldenEye Ransomware is an Asynchronous Backup Management
The GoldenEye Ransomware can lock all your data and sync your files with a cloud-based drive may backfire. A smarter solution is to backup your data manually and on a schedule as you can make sure you are not uploading corrupted files. Unfortunately, security researchers are unable to break the encryption employed by the GoldenEye Ransomware, and you will need to rely on your backups. Paying the ransom is a gamble that you might want to avoid since you are not guaranteed to receive a proper decryptor. The GoldenEye Ransomware Trojan can be purged with the help of a trusted anti-malware utility.
SpyHunter Detects & Remove GoldenEye Ransomware
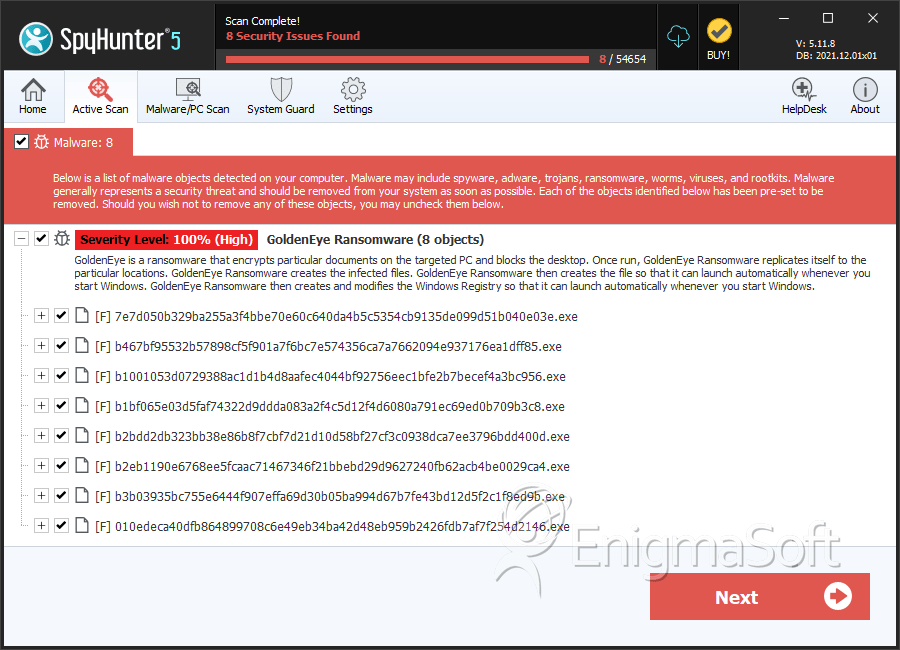
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 7e7d050b329ba255a3f4bbe70e60c640da4b5c5354cb9135de099d51b040e03e.exe | 01287ad927c6906afc39c383dde522c7 | 1 |
| 2. | b467bf95532b57898cf5f901a7f6bc7e574356ca7a7662094e937176ea1dff85.exe | 55c5eabc1160345919abe5349ada9134 | 1 |
| 3. | b1001053d0729388ac1d1b4d8aafec4044bf92756eec1bfe2b7becef4a3bc956.exe | ca2a850bef517532ab81a68997c7f34b | 0 |
| 4. | b1bf065e03d5faf74322d9ddda083a2f4c5d12f4d6080a791ec69ed0b709b3c8.exe | e1641c297d8c5d60f0f699f10f7a3b49 | 0 |
| 5. | b2bdd2db323bb38e86b8f7cbf7d21d10d58bf27cf3c0938dca7ee3796bdd400d.exe | 5c2acd28b59994e8aca162fee2ff19fb | 0 |
| 6. | b2eb1190e6768ee5fcaac71467346f21bbebd29d9627240fb62acb4be0029ca4.exe | 080e38fee28ae0cb2b8dea40f32d58cd | 0 |
| 7. | b3b03935bc755e6444f907effa69d30b05ba994d67b7fe43bd12d5f2c1f8ed9b.exe | 83322160d48b16602ae93c3cf161521a | 0 |
| 8. | 010edeca40dfb864899708c6e49eb34ba42d48eb959b2426fdb7af7f254d2146.exe | 9e6f4b572b4bf00cb0f10f984b552e07 | 0 |
| 9. | 01d8e1d4663905edf72176eee2bc470cd7e76779a45fbe0fdeca98afc693b11c.exe | cbed326a9bf439e96dbad479bb9bafa3 | 0 |
| 10. | 2863c8e24d6e000efedd6e08205724b46ceaab6883220b491e0b677153b97375.exe | 2484d6b75accf237e13d6051effe70ce | 0 |
| 11. | 2df63482dcbf94e7524b60248f7db8162409dabcdcd279ae0ef16e16e02daf30.exe | f3d2e795187a135e00038674fca034eb | 0 |
| 12. | 43e1e6383332f246a4154305ea47f0912d8082d19f69279437a3443eea8f644e.exe | 88a38f1caa6b4154372f8b86ac50c80e | 0 |
| 13. | 479081acafa64409b54f019569d0123f4d6e4b727edc3235935dea3f571e43ca.exe | 2c3e7d6247f5c8a35c8806fe40ef838f | 0 |
| 14. | 53be0977f579c209df24d8d128ed5a69f58822beddcbac0c39f5af5490b0d705.exe | c27e74c6a5d37a079d185fbbd9c3ce46 | 0 |
| 15. | 54a4d7f770fb20d538b49edff42cd6fb1014158338993e3bf30231f8cd4d977c.exe | e56c4f483bacc9c0e8a17d9f775ca44b | 0 |
| 16. | 66fa85b64b8b3039b4eb66be1467c441d292f73b31fa48fd488e13861f4440fb.exe | 07ee2abe737371d6cc7a3f327bddad52 | 0 |
| 17. | 677dac10932a44aead63cbba338113b2e8826768741c5567479487a105c6275e.exe | 17d02f5d8f34a874516f7cca588b103a | 0 |
| 18. | 6896f5f4bd7c2e769aa36a02b320103771deae241bc64110e32465e726e2ca03.exe | a97bf621240f6abf5559b60b45b0c35c | 0 |
| 19. | 6a7a73df77859a9c68b026e7c425a9a2448ef23a970ddc7223600e79a7835029.exe | 5fc5709455208d435a5077542217a85d | 0 |
| 20. | 741bb7ba53fffbbcf337f4a9665586913c4ccbb9c57f579e18cf90c446f4c997.exe | f2d76f3f0d76076d1ac98ed2d3691ffa | 0 |
| 21. | 747bbe34e297074ec78cc9cb86cda2b35bbc9925244a0ba01680b7ba857f9c06.exe | 2b0a2eb531d4f6212c5602ae3cb07902 | 0 |
| 22. | 9a848f6a408460fdc3475c740d7a20d2c11c8547c9ce2d183589fc358f086fdf.exe | 8e126c1808f4c7f245906cd1109e25ee | 0 |
| 23. | a6752f9a9a134b4cfd27cba109b793c75ae3615e7ac5796fa336255b366fab0c.exe | 4f3172d3d552b2fc8efe83909b91f45d | 0 |
| 24. | c7b13a995ac1e7d861084679309fb459199578ec10f440447bcc5e546b62c1dd.exe | 864db706d7098d0a123913ecf14c4f31 | 0 |
| 25. | d95df50fab57f4a370cb48eae5d9145dee71bea02f448848d202f158f5de4daf.exe | 9d1f6aa6e2b657aadb58c220855cf6b8 | 0 |
| 26. | f249f03389a370d2637db36b75511c285fdb1b0ae9e720521ffbbeb64c44517b.exe | b7e36d14e84772f2bbbfd881f4e15c81 | 0 |
| 27. | f5d7da76ebcac596156b94ad94495002980fcedf983a0f418622faf23c88b60a.exe | 7e928f47de95eaecb937bba3d9ec81e8 | 0 |