Eight Ransomware
Eight Ransomware Image
Ransomware threats have been a very popular malware type for quite a few years now. What makes them so popular is that they are easy to build (provided that the authors use a ransomware building kit) and rather quick to spread. This data-locking Trojan is a variant of a popular ransomware threat known as the Phobos Ransomware.
Table of Contents
Propagation and Encryption
The Eight Ransomware may be distributed via phishing emails. Authors of ransomware often tailor a bogus message that aims at tricking users into downloading and opening the file attached to the email. Often, the attachment would seem like a document that contains important information and should thus be reviewed as soon as possible. However, not all authors of ransomware use spam emails as a preferred infection vector. Some cyber crooks prefer using bogus application updates, torrent trackers, and even malvertising campaigns to propagate ransomware threats. The Eight Ransomware is likely capable of encrypting a long list of filetypes, which are likely to be present on the system of any regular user. This means that your .doc, .docx, .xls, .xlsx, .ppt, .pptx, .pdf, .jpg, .jpeg, .gif, .png, .rar, .mp3, .mp4, .mov and countless other filetypes will be encrypted securely after the Eight Ransomware compromises your computer. The Eight Ransomware alters the names of the locked files because it appends an '.id[].[use_harrd@protonmail.com].eight' extension to the affected files. For example, a file you had called 'sunny-spring.jpeg' will be renamed to 'sunny-spring.jpeg.id[].[use_harrd@protonmail.com].eight' where the victim ID is uniquely generated for each affected user.
As you’d expect, the virus is programmed to lock files away and demand a ransom for their safe return. Hackers promise to deliver decryption tools to victims that pay them off. While paying off the hacker is the only way to get the unique tools needed to decrypt files, you must never pay the ransom. There’s no guarantee that they’ll live up to their promise and deliver the tool. Your information is still lost even if you pay off the ransom. Many people who pay off the ransom become scam victims instead of hacking victims, and it’s easier to restore lost files than lost money.
No matter what, though, you want to remove the virus from your computer as soon as possible. If you don’t, then you could just get re-infected as soon as you restore the files, and you’ll be back to square one.
How Did I Get Infected?
Hackers have a lot of different tools to trick people into launching Eight ransomware. It could be that you received an email from the hackers. They send emails where they pretend to represent a legitimate company. The message appears to be legitimate and contains an attachment you are tricked into downloading. Once you download and run the file, though, it installs the ransomware on to your computer. Never interact with attachments from suspicious and unsolicited emails. That’s the first step to staying safe online.
Another way that Eight ransomware gets on computers is that users unknowingly download it. Ransomware is spread through file-sharing sites and hidden in malicious ads or notifications. Stay clear of suspicious downloads and don’t interact with untrusted ads. You should also run some kind of antivirus or antimalware program to protect your computer better. It also helps to make sure your operating system and applications are updated to the latest version. Updates commonly include patches for vulnerabilities exploited by hackers and viruses.
The Ransom Note
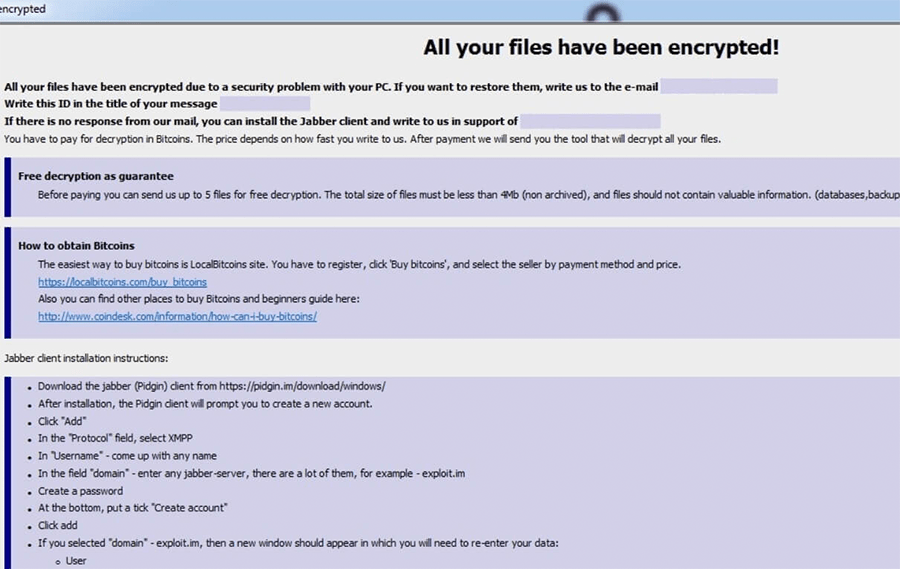
After completing the encryption process, the Eight Ransomware will drop the attackers' ransom message on the user's system. The message in question is contained in two files, namely 'info.txt' and 'info.hta.' In the ransom message, the attackers state that the ransom fee depends on how quickly the victim contacts the authors of the Eight Ransomware. However, they make it clear that the fee should be paid via Bitcoin. They also come up with instructions on how to obtain Bitcoin for the users who do not know how to deal with cryptocurrency. To prove to the victim that they have a working decryption tool, the creators of this Trojan offer to decrypt up to five files free of charge, provided that the files do not exceed 4MB in total. There are two email addresses supplied for the victims who want to get in touch with the creators of the Eight Ransomware – ‘use_harrd@protonmail.com' and ‘usehhard@cock.li.'
Eight ransomware encrypts the data on a computer. It focuses on data deemed necessary to users. It will encrypt documents, photos, videos, archives, and similar data. The virus changes the file extension of files it locks to .eight. The new extension also includes an email address, as listed in the ransom note. This email address is where victims can contact the attacker to restore their data.
The ransom note reads:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail use_harrd@protonmail.com
Write this ID in the title of your message 1E857D00-2776
In case of no answer in 24 hours write us to this e-mail:useHHard@cock.li
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 4Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price.
https://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
hxxp://www.coindesk.com/information/how-can-i-buy-bitcoins/
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
As you can see, the ransom note details where people can pay off their attackers. The hackers say that they will provide victims with a decryption tool if they pay off the ransom. They also claim they will decrypt one file as proof that their tool works, and they are sincere. Once again, we want to stress how important it is that you don’t deal with attackers. There’s always a risk involved, and it’s a risk not worth taking. The easiest and safest way to restore your files is through a backup.

