Desu Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | July 24, 2018 |
| Last Seen: | July 31, 2018 |
| OS(es) Affected: | Windows |
Desu Ransomware is another low-tier crypto-malware to come out in late July 2018. The Desu Ransomware is suspected to be based on Aurora Ransomware, but more research is needed. Samples of the Desu Ransomware suggest it is distributed via corrupted Microsoft Word files. It is not outside of reason that the threat actors would use logos of trusted Internet companies and push messages under the guise of legitimate government agencies. The cyber threat may be dropped to the Temp folder on the primary system drive and run as 'memka.exe' (MD5:54b5234ec4b3682648cf528039bec59f). The program is known to apply a custom AES-256 cipher to targeted images, audio, video, text, Ebooks, PDFs, and databases. Enciphered data carries the '.desu' extension and sports the default file icons as the original versions of your files. We should note that the malware deletes the original files on your system and writes the encrypted versions. For example, 'Sabaton-Ruina Imperii.mp3' is renamed to 'Sabaton-Ruina Imperii.mp3.desu' and the volume snapshot copy of the file is deleted too. The ransom note is loaded as '@_DECRYPT_@.txt' in Notepad and reads:
'==#desu ransomware#==
SORRY! Your files are encrypted.
File contents are encrypted with random key.
We STRONGLY RECOMMEND you NOT to use any "decryption tools".
These tools can damage your data, making recover IMPOSSIBLE.
Also we recommend you not to contact data recovery companies.
They will just contact us, buy the key and sell it to you at a higher price.
If you want to decrypt your files, you have to get private key.
In order to get private key, write here: jOra@protonmail.com !!
And send me your id: [random characters]
And pay 200$ on lARDXRDsvnsYiM5jazFagtCrAzSFC1Qmy wallet
If someone else offers you files restoring, ask him for test decryption.
Only we can successfully decrypt your files; knowing this can protect you from fraud.
You will receive instructions of what to do next.
==#desu ransomware#=='
The Desu Ransomware Trojan is reported to overwrite the MBR record on Windows and force infected systems to restart. As a result booting into Windows is interrupted by a message that says:
'Oops! Your files have been encrypted.
Your files are no longer accessible.
You might have been looking for any way to recover your files.
Don't waste your time, you can't recover all your files safely. But
you need to pay and get the decryption password.
Email support: j0ra@pronmail.com
Your ID:
[random characters]
Key: [space for user input]'
We advise against making contact with the malware operators via the 'j0ra@protonmail[.]com' email account. The threat actors are likely to direct users pay a hefty "decryption" fee using Bitcoin. That way, the digital coins can be transferred through several accounts before they are converted into standard currencies. Tracking Bitcoin transactions is very difficult, and law enforcement authorities are not always successful at catching Ransomware operators. It is best to avoid the services offered via 'j0ra@protonmail[.]com' and use backup images instead. PC users can eliminate the Desu Ransomware Trojan by running a respected anti-malware solution on their system. Cloud services may help you protect valuable data and recover faster from attacks with Desu Ransomware. Detection names by AVs that recognize the Desu Ransomware include:
BehavesLike.Win32.Generic.dh
ML.Attribute.HighConfidence
Ransom_Genasom.R011C0DGH18
TR/FileCoder.zxehh
Trojan ( 00516bfc1 )
Trojan.FileCoder (A)
Trojan.GenericKD.31098949
Trojan.Siggen7.55992
Trojan.Win32.FileCoder.ffpibu
W32/Trojan.BDCL-1372
SpyHunter Detects & Remove Desu Ransomware
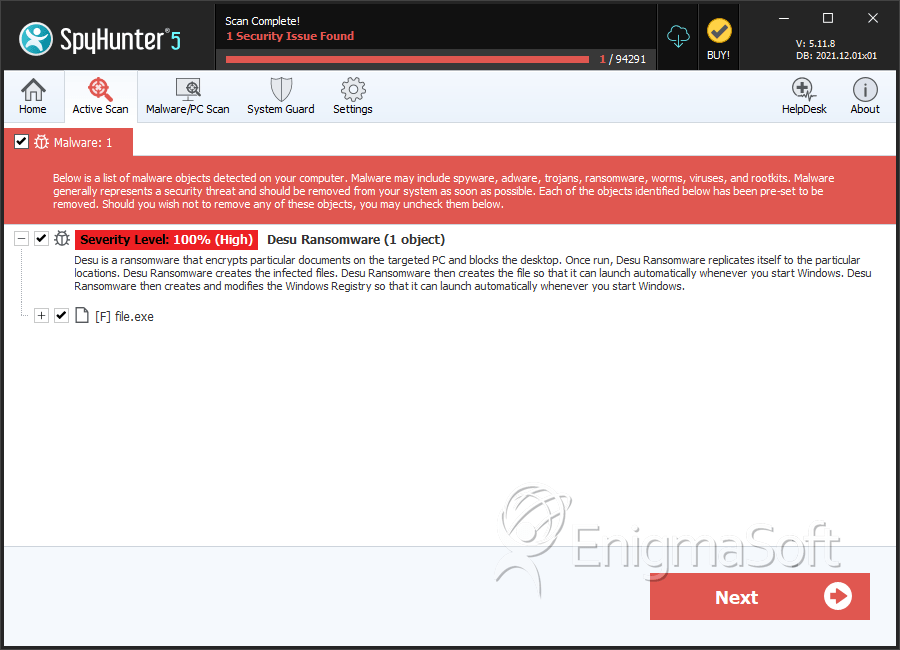
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 54b5234ec4b3682648cf528039bec59f | 0 |