Aurora Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 107 |
| First Seen: | May 30, 2018 |
| Last Seen: | May 23, 2023 |
| OS(es) Affected: | Windows |
PC security researchers first observed the Aurora Ransomware, an encryption ransomware Trojan, on May 29, 2018. There is very little to differentiate the Aurora Ransomware from the many other encryption ransomware Trojans being used in attacks today. The Aurora Ransomware, like most similar ransomware Trojans, is commonly delivered to the victim through a corrupted spam email file attachment, usually taking the form of a file with embedded macro scripts. The Aurora Ransomware uses a strong encryption algorithm to make the victim's files inaccessible and takes the victim's files captive until the victim pays for the decryption program.
Table of Contents
How the Aurora Ransomware Carries Out Its Attack
The Aurora Ransomware searches for user-generated files on the infected computer and then makes them unusable. Examples of the files that are often targeted in attacks like the Aurora Ransomware include:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
The Aurora Ransomware will mark the affected files with the file extension '.Aurora,' which is added to each affected file's name. The Aurora Ransomware seems to run as an executable file named 'List.exe' on the infected computer, although there are several executable files associated with the Aurora Ransomware, which may include 'OneKeyLocker,' another name by which the Aurora Ransomware may be identified.
The Aurora Ransomware’s Ransom Note
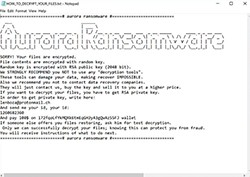
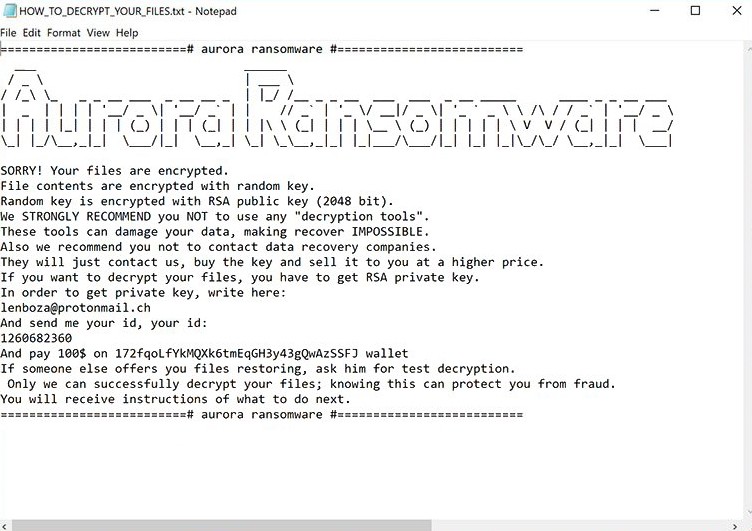
The Aurora Ransomware delivers a ransom note. The Aurora Ransomware delivers its ransom message in the form of a text file dropped on the infected computer's desktop. The Aurora Ransomware ransom note is named 'HOW_TO_DECRYPT_YOUR_FILES.tx' and contains the following message:
'Aurora Ransomware
SORRY! Your files are encrypted.
File contents are encrypted with random key.
Random key is encrypted with RSA public key (2048 bit).
We STRONGLY RECOMMEND you NOT to use any "decryption tools".
These tools can damage your data, making recover IMPOSSIBLE.
Also we recommend you not to contact data recovery companies.
They will just contact us, buy the key and sell it to you at a higher price.
If you want to decrypt your files, you have to get RSA private key.
In order to get private key, write here:
anonimus.mr@yahoo.com
And pay 500$ on 3CwxawqJpM4RBNididvHf8LhFA2VfLsRjM wallet
If someone else offers you files restoring, ask him for test decryption.
Only we can successfully decrypt your files; knowing this can protect you from fraud.
You will receive instructions of what to do next.'
PC security analysts are against contacting the criminals responsible for the Aurora Ransomware attack via the email addresses listed in its ransom note. This may make them vulnerable to additional attacks and will almost never result in the return of their data.
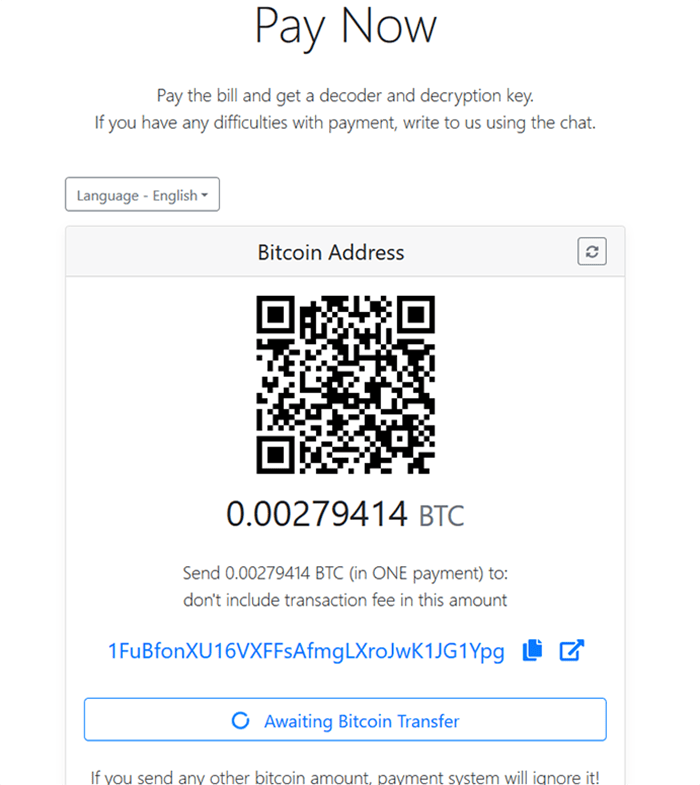
Update January 4th, 2020 - .crypton File Extension Variant
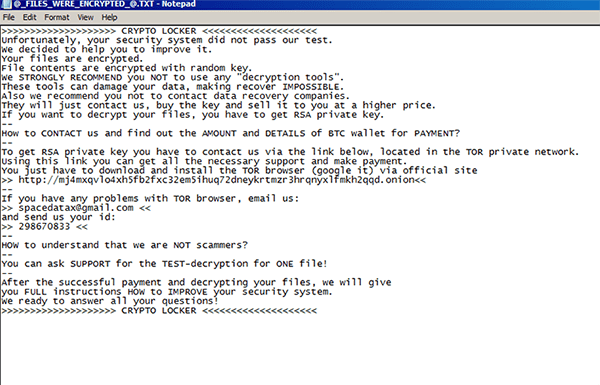
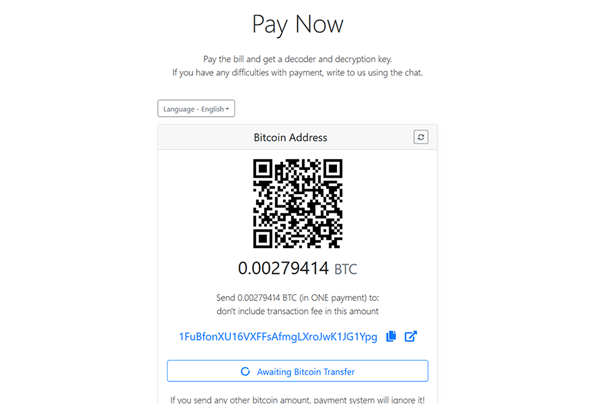
Security researchers came across a new version of the Aurora ransomware on January 4th, 2020, which appended the encrypted files with the .crypton extension. This time around, the threat actors seem to be aiming for quantity, rather than quality of the infections, as they demand a ransom payment of 0.00279414BTC(worth about $20 on the day of detection). The ransom notes that the Crypton Aurora variant deposits on the infected system are named @_FILES_WERE_ENCRYPTED_@.TXT, @_HOW_TO_DECRYPT_FILES_@.TXT, and @_HOW_TO_PAY_THE_RANSOM_@.TXT. and contain the following message:
>>>>>>>>>>>>>>>>>>>> CRYPTO LOCKER <<<<<<<<<<<<<<<<<<<<
Unfortunately, your security system did not pass our test.
We decided to help you to improve it.
Your files are encrypted.
File contents are encrypted with random key.
We STRONGLY RECOMMEND you NOT to use any ''decryption tools''.
These tools can damage your data, making recover IMPOSSIBLE.
Also we recomment you not to contact data recovery companies.
They will just contact us, buy the key and sell it to you at a higher price.
If you want to decrypt your files, you have to get RSA private key.
- -
How to CONTACT us and find out the AMOUNT and DETAILS of BTC wallet for PAYMENT?
- -
To get RSA private key you have to contact us via the link below, located in the TOR private network.
Using this link you can get all the necessary support and make payment.
You just have to download and install the TOR browser (google it) via official site
>>http://mj4mxqvlo4xh5fb2fxc32em5ihuq72dneykrtmzr3hrqnyxlfmkh2qqd.onion<<
- -
If you have any problems with TOR browser, email us:
>>spacedatax@gmail.com<<
and send us your ID:
>> random numbers <<
- -
HOW to understand that we are NOT scammers?
- -
You can ask SUPPORT for the TEST-decryption for ONE file!
- -
After the successful payment and decrypting your files, we will give you FULL instruction HOW to IMPROVE your security system.
We ready to answer all your questions!
>>>>>>>>>>>>>>>>>>>> CRYPTO LOCKER <<<<<<<<<<<<<<<<<<<
Aurora Ransomware alternate variant image
Aurora Ransomware alternate variant image
As you can see from this ransom note, the people behind the Crypton Aurora variant are trying to pass as security experts that are selling you a service. The Crypton Aurora variant also comes with a customer support feature in 18 languages that makes the whole transaction even smoother, and they're even willing to decrypt one file for free, just to show you they mean business. There are, however, no guarantees that the cyber crooks will keep their promise and not demand further payment once they see you are willing to spend money to get your files back.
Dealing with the Aurora Ransomware
The best way to protect your data from threats like the Aurora Ransomware is to have file backups. Having file backups ensures that you can restore your files easily with no need to contact the criminals. A reliable, dependable program that is fully up-to-date also should be used to prevent threats like the Aurora Ransomware from being installed.