CTF Ransomware
The CTF Ransomware is a ransomware Trojan that was the result of a 'Catch the Flag' competition. Programmers had a competition to create a fully functional ransomware Trojan in the shortest possible time. The CTF Ransomware was first observed in May of 2007. Unfortunately, the results of this competition are being used to carry out attacks on victims. The CTF Ransomware is being delivered using corrupted spam email attachments currently. These email messages may be disguised as notifications from messaging companies like FedEx of UPS, with messages such as the following:
'Hello,
We have delivery problems with your parcel #7315475325
Please, open the attachment for more details'
Opening the attachment allows a macro-enabled file to run, which downloads and executes the CTF Ransomware's executable file.
Table of Contents
The CTF Ransomware Works Very Stealthily
Once the CTF Ransomware has made it onto a computer, it encrypts the victim's files using a strong encryption method. The CTF Ransomware will run in the background and not alert the victim of the attack until it has finished its encryption routine. The CTF Ransomware will search for files with the following extensions (among others):
.3gp, .7z, .apk, .avi, .bmp, .cdr, .cer, .chm, .conf, .css, .csv, .dat, .db, .dbf, .djvu, .dbx, .docm, ,doc, .epub, .docx .fb2, .flv, .gif, .gz, .iso .ibooks,.jpeg, .jpg, .key, .mdb .md2, .mdf, .mht, .mobi .mhtm, .mkv, .mov, .mp3, .mp4, .mpg .mpeg, .pict, .pdf, .pps, .pkg, .png, .ppt .pptx, .ppsx, .psd, .rar, .rtf, .scr, .swf, .sav, .tiff, .tif, .tbl, .torrent, .txt, .vsd, .wmv, .xls, .xlsx, .xps, .xml, .ckp, .zip, .java, .py, .asm, .c, .cpp, .cs, .js, .php, .dacpac, .rbw, .rb, .mrg, .dcx, .db3, .sql, .sqlite3, .sqlite, .sqlitedb, .psd, .psp, .pdb, .dxf, .dwg, .drw, .casb, .ccp, .cal, .cmx, .cr2.
The files encrypted by the CTF Ransomware will have the file extension '.ctf' added to the final of each file's name. This makes it simple to know which files have been affected by the CTF Ransomware attack. The CTF Ransomware uses a combination of the AES and RSA encryptions to encrypt the victim's files, making them inaccessible if computer users do not have access to the decryption key. Unfortunately, it is not possible to decrypt the files affected in the CTF Ransomware attack currently.
How the CTF Ransomware Demands Money from the Victim
After encrypting the victim's files, the CTF Ransomware displays a program window that includes a picture of a female model. This window allows victims to enter the decryption key, which is obtained by paying a large ransom. The CTF Ransomware also will deliver its ransom note in the form of a text file named 'How to decrypt files.txt,' which is dropped on the infected computer's desktop. The CTF Ransomware ransom note contains the following message:
'NOT YOUR LANGUAGE? USE https://translate.google.com
What happened to your files?
All your files were protected by a strong encryption with RSA 2048
More information about the encryption keys using RSA-2048 can be found on http://en.wikipedia.org
How did this happen?
!!! Specially for your PC was generated personal RSA-4096 KEY, both public and private.
!!! ALL YOUR FILES were encrypted with the public key, which has been transferred to your computer via the Internet.
Decrypting of your files is only possible with the help of the private key and decrypt program, which is on our secret server.
What do I do?
So, there are two ways you can choose: wait for a miracle and get your price doubled, or start obtaining BTC NOW, and restore your data easy way.
If You have really valuable data, you better not waste your time, because there is no other way to get your files, except make a payment.
For more specific instructions:
Contact us by email only, send us an email along with your ID number.
For you to be sure, that we can decrypt your files - you can send two small files.
please, do not waste your time! You have 72 hours, hurry! After that, the key is deleted from our servers.
E-MAIL1:june7@dr.com
E-MAIL2:june7@iname.com
E-MAIL3:anx@dr.com'
It is clear that a lot of the content used by the CTF Ransomware is recycled from other threats since this ransom note is nearly identical to ransom notes observed in other attacks.
SpyHunter Detects & Remove CTF Ransomware
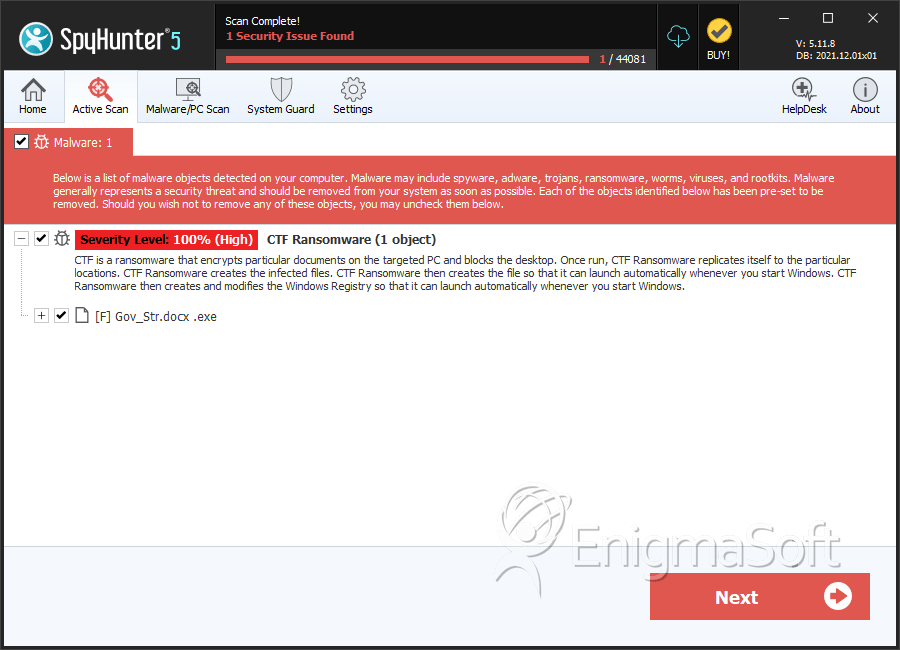
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Gov_Str.docx .exe | 332c21487065b9b3e38238df2825e95f | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.