Crypton Ransomware
The Crypton Ransomware is an encryption Trojan that is based on the Hidden Tear project released by Otku Sen in 2015 on Github.com as an 'educational ransomware.' The Crypton Ransomware Trojan was discovered in the second week of November 2016 when users reported that their files were encrypted and they were presented with a decryptor that is activated after making a payment. Researchers were able to discover a Trojan dropper linked to the Crypton Ransomware that was delivered to users as a document they downloaded from spam emails. As in many other cases that involve threats like the HCrypto Ransomware, the Crypton Ransomware was introduced in the PC by exploiting macro. The dropper for the Crypton Ransomware may appear as an archive containing photos, but it is an executable. AV vendors detected the dropper for Crypton Ransomware as:
- Troj.Generic.mrgk
- malicious_confidence_64% (W)
- HEUR/QVM03.0.0000.Malware.Gen
Table of Contents
The Crypton Ransomware is Hidden in Macro and JavaScript-Enabled Documents and Archives
However, the authors of the Crypton Ransomware have many options when they want to disguise their threat and can use various packaging, encryption and obfuscation techniques. Users need to avoid spam email and pay attention to the sender, as well as visual elements and links embedded in the messages they receive. The Crypton Ransomware is a standard encryption Trojan that uses the AES-256 cipher to lock data. Analysts report that the Crypton Ransomware does not append a unique identifier to files it have modified as opposed to the '.UCRYPT File Extension' Ransomware. The Crypton Ransomware is designed to scan local drives and removable storage for the following formats:
.XSLX, .CDR, .XLS, .VSD, .DOCX, .DOC, .JPG, .PDF, .XML, .DAT, .PSD, .CD, .TXT, .TBB, .TBN, .DB, .DBX, .PST, .PPT, .PNG, .TIFF, .RTF, .HTM, .HTML, .MHT, .ZIP, .RAR, .7X, .DBF, .MDB.
As you can see, the Crypton Ransomware is aimed at users who work with Microsoft Office, SQLite databases, and image editors on a daily basis. The ransom notification is available as 'readme_encrypted.txt' and says:
'This files are encrypted! Follow the instructions on the screen. Эти файлы зашифрованы! Следуйте инструкциям на экране.'
The decryptor for the Crypton Ransomware is provided as an HTA app that is executed when the encryption procedure is complete. Samples of the Crypton Ransomware reveal that the author created versions of the Trojan for users who speak English and Russian. The CryptonDecryptor shows the following message, which is available in Russian as well:
'Attention!
All data on you PC is encrypted!
To decrypt your data, you need to pay the amounts shown below.
Please note that the payment confirmation may take some time (from 1 hour to 1 day).
All this time, the program must be running and have an internet connection.
After the successful confirmation of payment - decoding will start automatically.
Read more about how to make a payment using Bitcoin can be found on the internet network.
In destination address - specify the Bitcoin address, listed below.
It is not recommended to attempt to recover the data, or remove this program! This can lead to a complete loss of your data forever! To restore data, you must be connected to the Internet.'
Paying the Ransom is not Your Only Option When Dealing with the Crypton Ransomware
Security analysts note that the Crypton Ransomware may require users to deliver payment of 5000 Rubles or 77 USD to gain a decryption key as we saw as the standard in the Telecrypt Ransomware campaign. We should note that paying the ransom is not encouraged since the operators of the Crypton Ransomware are not likely to keep their end of the bargain. The focus of activities involving ransomware is to infect as many users as possible and wait for desperate people make a payment. You can take a smarter approach to solving a problem with the Crypton Ransomware. Threats like the Crypton Ransomware are ineffective against users who have backups and archives stored on unmapped drives, cloud storage (Google Drive, OneDrive, Dropbox, etc.) and CD/DVDs. You should clean your PC with a trustworthy anti-malware utility and recover your data using clean backups. AV software may detect objects associated with the Crypton Ransomware as:
- HEUR/QVM03.0.0000.Malware.Gen
- Ransom_CRYPTEAR.SM
- UDS:DangerousObject.Multi.Generic
- malicious_confidence_82% (D)
SpyHunter Detects & Remove Crypton Ransomware
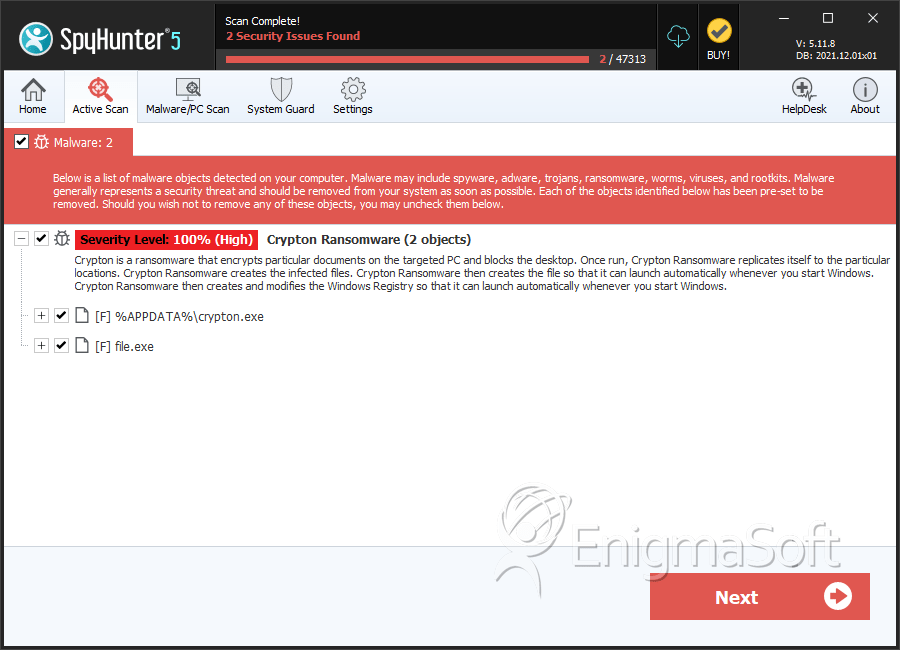
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | crypton.exe | 237bf11449a2018b058643c38f12430c | 0 |
| 2. | file.exe | 1aee345a73b07c3ec4c829c1a335c38b | 0 |
| 3. | file.exe | 3b1436993c031702b2c46b78c24da658 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.