'COVID-19.exe' Wiper
A burgeoning number of cyber crooks are taking advantage of the COVID-19 pandemic by creating malware and various online tactics. It is not surprising that individuals who lack morality are trying to exploit a worldwide crisis of the proportions of the Coronavirus outbreak to make a buck. Many cyber crooks have created Coronavirus-based ransomware threats that encrypt users’ data and blackmail them for cash. Others have used the pandemic to propagate infostealers that are capable of collecting information from the compromised hosts. However, the creators of the ‘COVID-19.exe’ threat have taken a different approach.
The ‘COVID-19.exe’ malware is a wiper program that has the potential to cause a lot of harm to the hosts it manages to compromise. The malware experts who spotted the ‘COVID-19.exe’ wiper report that this threat is yet to be distributed and used. However, the ‘COVID-19.exe’ wiper is fully built and ready to be deployed whenever its creators choose to.
When the ‘COVID-19.exe’ wiper infects a targeted host, it will spawn a fake Windows error alert and then display a new window, which states that ‘Coronavirus has infected your PC!.’ Needless to say, a real-life virus, like COVID-19, is not capable of compromising your computer, but the attackers have still opted to use this tactic, likely because the name is widely recognizable to users worldwide. The users may not be able to close the ‘Coronavirus has infected your PC!’ window, which is likely to keep them distracted while the ‘COVID-19.exe’ wiper is operating in the background. The ‘COVID-19.exe’ threat will first wipe out the user’s MBR (Master Boot Record) and overwrite it completely. This means that next time the users reboot their computers, they may not be able to start Windows properly. Instead, they will likely see an MBR screen that was set up by the threat. The new screen carries the message of the attackers – it states that the ‘COVID-19.exe’ wiper was the creation of ‘Angel Castillo’ and the PC is no longer usable. The creators of the ‘COVID-19.exe’ wiper also have added their Discord profile, likely as a means of communication with the victims – ‘Windows Vista #3294.’ It does not appear that the authors of the ‘COVID-19.exe’ wiper demand any payment. This means that the attackers may be deploying the ‘COVID-19.exe’ wiper because they get pleasure from causing destruction.
Table of Contents
COVID-19.exe Wiper Rewrites MBR on Computers
Researchers analyzed four malware samples, two of which were able to rewrite MBR sectors on a computer. It would take technical knowledge to create a virus capable of rewriting the master boot record. Changing the MBR is something that an amateur could never do, and it could make a computer unable to start at all.
MalwareHunterTeam discovered the first of the MBR-rewriting viruses. The team published a report about the virus, called COVID-19.exe. The virus has two infection stages that leave computers crippled.
The first phase is simple enough; the virus displays a popup window that can't be closed because users can't access Task Manager.
The popup is more dangerous than it looks. As users try to get rid of the annoying window, the virus is running silently in the background, altering the master boot record. The virus restarts the computer after it changes the MBR. With the MBR changed, users are taken to a new pre-boot screen that locks them out of their computers. It is possible to restore access to the computer, but it takes special tools to rebuild the original MBR and get it back in working condition.
Another Coronavirus-Malware Threat
Unfortunately, there was a second strain able to mess with the MBR. This latter strain was more advanced than the first. The second strain disguised itself as the "Coronavirus Ransomware" but was, in reality, stealing passwords. The virus disguised itself as ransomware to trick users into not realizing what was going on.
After stealing information from a computer, the fake ransomware rewrote the MBR on the computer. Like the first virus, this sent users to a pre-boot message so they couldn't access their computer. After being locked out of their computer and seeing a ransom note, most people would assume they were hit with ransomware and wouldn't think to check if their passwords were stolen.
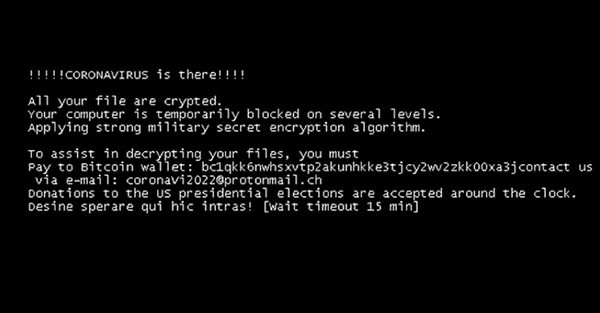
Example of 'COVID-19.exe' Wiper Ransom note
Researchers say the malware had the code necessary to wipe information from a system, but that this feature wasn't active on the sample they used. This sample was also seen twice, with the second version appearing two weeks later. The second sample was discovered by Karsten Hahn, a researcher with G Data. The second version of the malware still rewrote the MBR but worked as a screen-locker instead of a data wiper.
Coronavirus-Themed Data Wipers
Security researchers discovered coronavirus-themed data wipers on top of the MBR rewriters. MalwareHunterTeam found two such data wipers.
The first data wiper appeared in February. It had a Chinese file name and likely targeted Chinese users. There's no concrete evidence if the virus was ever sent out into the wild or if it was just created as a test. The second appeared more recently. It appeared on the VirusTotal portal after being uploaded by an Italian user.
According to MalwareHunterTeam, both wipers are of low quality. The wipers use inefficient, time-consuming, error-prone methods to erase files on systems. They still work despite the low quality, though, and should be considered a threat.
Given how much malware is designed to steal money, it seems strange someone would create malware to destroy information like this. There are plenty of malware samples created by people like jokes. Something similar happened during the WannaCry crisis, where endless clones of WannaCry were created for no real reason.
It is not known how the ‘COVID-19.exe’ wiper will be distributed yet. However, users are advised to be very careful when installing any software or downloading any files related to the Coronavirus outbreak, as many cybercriminals are taking advantage of the pandemic to spread malware.

