Agenda Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 4 |
| First Seen: | July 19, 2022 |
| Last Seen: | March 1, 2023 |
| OS(es) Affected: | Windows |
The Agenda Ransomware, also known as Qilin, is a potent threat primarily targeting corporate or business entities. However, the threat actors behind the Agenda Ransomware could easily use it against individual users as well. Details about the malware were disclosed by a cybersecurity researcher that goes by Petrovic on Twitter.
Table of Contents
Origin and Operation of Qilin Ransomware
Qilin, a ransomware-as-a-service criminal operation, collaborates with affiliates to encrypt and exfiltrate data from hacked organizations before demanding a ransom. The name "Qilin" is derived from Chinese mythology, where it represents a creature combining the features of a dragon and a horned beast, akin to a unicorn. Despite its name, the group behind Qilin ransomware appears to be linked to Russia, not China.
Technical Capabilities of Agenda Ransomware
The invasive threat can lock numerous important file types, rendering them completely unusable and inaccessible. Each encrypted file will have a random string of characters appended to its original name as a new extension. Additionally, the Agenda Ransomware delivers a text file named '[random_string]-RECOVER-README.txt,' containing a ransom note from the attackers.
History and Notable Attacks
Qilin first posted about a victim on its darknet leak site in October 2022 and has since increased its activities, targeting organizations like street newspaper The Big Issue, automotive parts giant Yanfeng, and the Australian court service. Recently, it was thrust into the spotlight when an emergency "critical incident" was declared at several London hospitals following a ransomware attack on the blood testing and transfusion firm Synnovis. Qilin announced on its dark web leak site that it would release data stolen during the attack, demanding a staggering US $50 million (approximately £40 million) for the tools to decrypt its systems and a promise not to publish the data.
Ransom Demands and Communication Methods
The ransom-demanding message states that the cybercriminals have collected various confidential and sensitive data from the victim's network and devices, detailing the potentially exfiltrated information in the note. It also reveals that the only way to contact the ransomware operators is by visiting their dedicated website hosted on the TOR network. Users are expected to access the site by entering the login information found in the ransom note.
Dubious Claims of Political Motivation
Interestingly, despite the hefty ransom demand, the Qilin ransomware gang has claimed in media interviews that their attack on the hospitals was not financially motivated but rather a protest against the British government's involvement in an unspecified war. This claim is dubious, given the group's history of indiscriminately targeting various entities, including businesses, schools, and healthcare organizations. The US $50 million ransom demand reflects the significant disruption faced by hospitals and patients, undermining the supposed political agenda.
Why Healthcare Organizations Are Frequent Targets
Public healthcare providers are frequent targets of ransomware due to their complex IT systems and limited budgets. The critical difference between a company being unable to manufacture widgets and a hospital being unable to treat patients makes healthcare organizations appealing "soft targets" for ransomware groups.
The full text of Agenda Ransomware's message is:
'-- Agenda
Your network/system was encrypted.
Encrypted files have new extension.-- Compromising and sensitive data
We have downloaded compromising and sensitive data from you system/network
If you refuse to communicate with us and we do not come to an agreementyour data will be published.
Data includes:
- Employees personal dataCVsDLSSN.
- Complete network map including credentials for local and remote services.
- Financial information including clients databillsbudgetsannual reportsbank statements.
- Complete datagrams/schemas/drawings for manufacturing in solidworks format
- And more…-- Warning
1) If you modify files - our decrypt software won't able to recover data
2) If you use third party software - you can damage/modify files (see item 1)
3) You need cipher key / our decrypt software to restore you files.
4) The police or authorities will not be able to help you get the cipher key. We encourage you to consider your decisions.-- Recovery
1) Download tor browser: hxxps://www.torproject.org/download/
2) Go to domain
3) Enter credentials-- Credentials
Extension:
Domain:
login:
password:'
Agenda Ransomware, aka Qilin, represents a significant threat to various organizations, especially those in the healthcare sector. However, it can be safely detected and removed using a reputable anti-malware program. Computer security experts recommend utilizing these programs as part of a comprehensive security strategy to protect against such invasive threats.
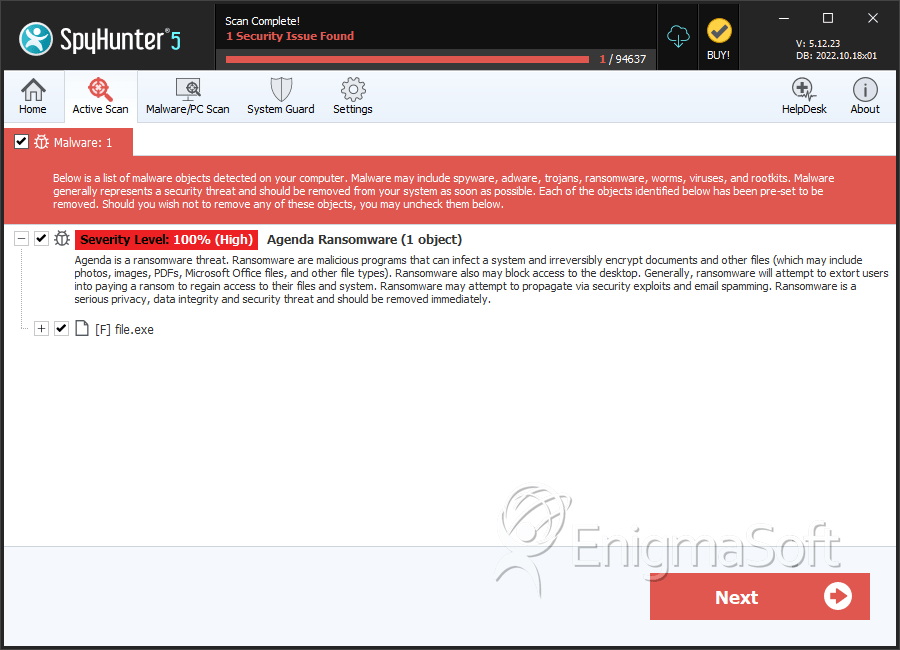
SpyHunter Detects & Remove Agenda Ransomware
Agenda Ransomware Video
Tip: Turn your sound ON and watch the video in Full Screen mode.

File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | a7ab0969bf6641cd0c7228ae95f6d217 | 2 |
