Adage Ransomware
Adage Ransomware Image
Adage Ransomware is a recent form of cryptovirus capable of locking target users out of their PC systems. To do so, Adage performs all-out encryption of the victims' data appending the '.adage' extension to each affected file. In terms of its architecture, Adage bears a striking resemblance to Phobos Ransomware, leading researchers to consider Adage to be an offshoot of Phobos Ransomware.
Table of Contents
Infection Vectors
Similar to Phobos, Adage Ransomware is most likely to arrive embedded in spam email campaigns, usually in the form of malicious attachments or web links. That is why Adage can be particularly dangerous to credulous users who tend to open every email they receive without searching for typical spam symptoms beforehand. The thing is, an attached invoice and another macro-enabled document may often look harmless at first sight, only to do pervasive damage later on after misleading the unsuspecting user into enabling macros to access the text. The same goes for embedded URLs designed to redirect the victim to a malware-laden web page rather than the seemingly genuine destination it pretends to.
When it comes to spreading Adage, hackers can take advantage of social media and file-sharing platforms, too. In this case, the cryptovirus may be lying dormant in web ads, disguised as a useful PC optimization tool, or bundled with other software as a drive-by download.
Regardless of which infection vector Adage ransomware has used to reach your PC system, it always pursues the same goal – to encrypt your data and extort money in exchange for restoring them.
Actual Infection
A close analysis of a recent Adage ransomware sample revealed how the parasite works once it has landed on a PC. Like other ransomware threats, Adage’s payload dropper contains more than one malicious tool because of the sheer amount of operations it has to perform before executing successful encryption. In brief, Adage ransomware is responsible for:
- Neutralizing any installed AV solutions
- Modifying your start menu, web browser settings, and file names
- Tampering with the Windows Registry to gain persistence during system startup
Once all the steps mentioned above have come to an end, Adage proceeds with the actual encryption process. If successful, the latter appends an additional extension to each infected file. This extension consists of two parts – an email address [in brackets] and the '.adage’ supplement. To date, every Adage infection we have witnessed so far features one of the following two extensions:
- [wewillhelpyou@qq.com].adage
- [helpteam38@protonmail.com].adage
Given that Adage Ransomware is still active at the time of this writing, future infections may feature a different email address as an extension. The '.adage’ component, on the other hand, would be highly unlikely to go away.
The Ransom Note
Following full-blown file encryption, Adage ransomware generates the ransom note outlining the terms and conditions for restoring all data. The note accompanying Adage ransomware is quite similar to the one seen in Phobos infections.
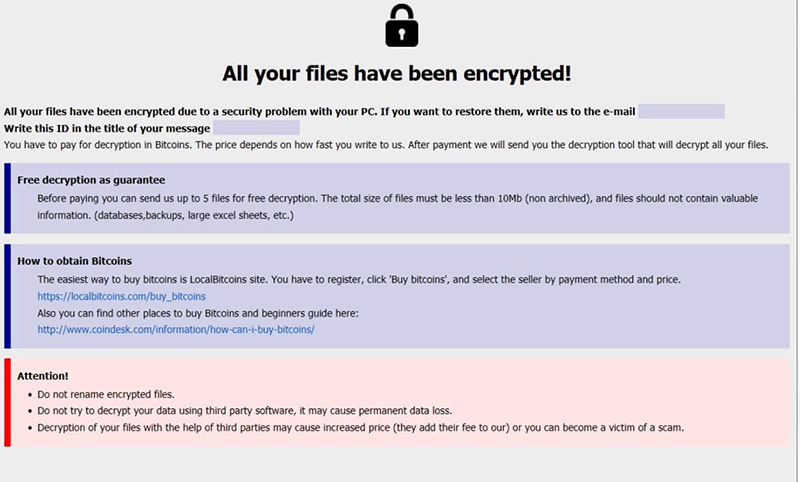
Here is the text of the note:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the email [highlighted box]
Write this ID in the title of your message [highlighted box]
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 10Mb (non archived), and files should not contain valuable Information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price. https://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here: http://www.coindesk.comiinformation/how-can-i-buy-bitcoins/
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
The ransom note arrives in duplicate – as a pop-up Info.hta and in the form of an Info.txt file. The actual ransom amount is missing in the note. Instead, it is subject to further correspondence between the victim and the cybercriminal(s).
Aftermath and Precautions
A successful ransomware attack might as well render your files inaccessible to you. You could try to restore them via Microsoft Windows' Volume Shadow Copy Service (VSS) to retrieve backup copies or file snapshots. Unfortunately, that would only work if the Adage Ransomware virus has not already deleted those Shadow Volume Copies. Using a third-party anti-malware tool may help you remove Adage's malicious files from your system, but it won't decrypt your data if the disaster has already struck. Unless researchers have developed and shared a free decryption tool on the Web, you may decide on paying the crooks for a promised decryptor as a last resort. However, we advise against you doing so because the prospect of the cybercriminals honoring their promise to give you a working decryption tool is inconsistent with the empirical evidence amassed so far.
In light of the grim consequences surrounding an Adage ransomware infection, it is crucially important to perform regular data backups as the ultimate preventive measure. More often than not, this is the only action that may avoid any data loss. On the other hand, running a reputable anti-malware solution on your system is just as paramount as it will provide you with real-time protection against such nasty threats.