Win 7 Security 2012
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 21 |
| First Seen: | August 9, 2011 |
| Last Seen: | November 4, 2019 |
| OS(es) Affected: | Windows |
Win 7 Security 2012 Image
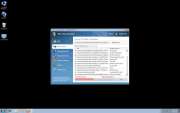
Win 7 Security 2012 is one of the many different versions that exist of Ppn.exe, a malicious file. New versions of programs related to this file are released every day; all of the different versions of Win 7 Security 2012 are the same program, with a different name and theme. Since the rogue programs have different skins according to the user's operating system, Win 7 Security 2012 can be hard to track by security experts. This defining characteristic has caught the attention of computer security specialists around the world.
Table of Contents
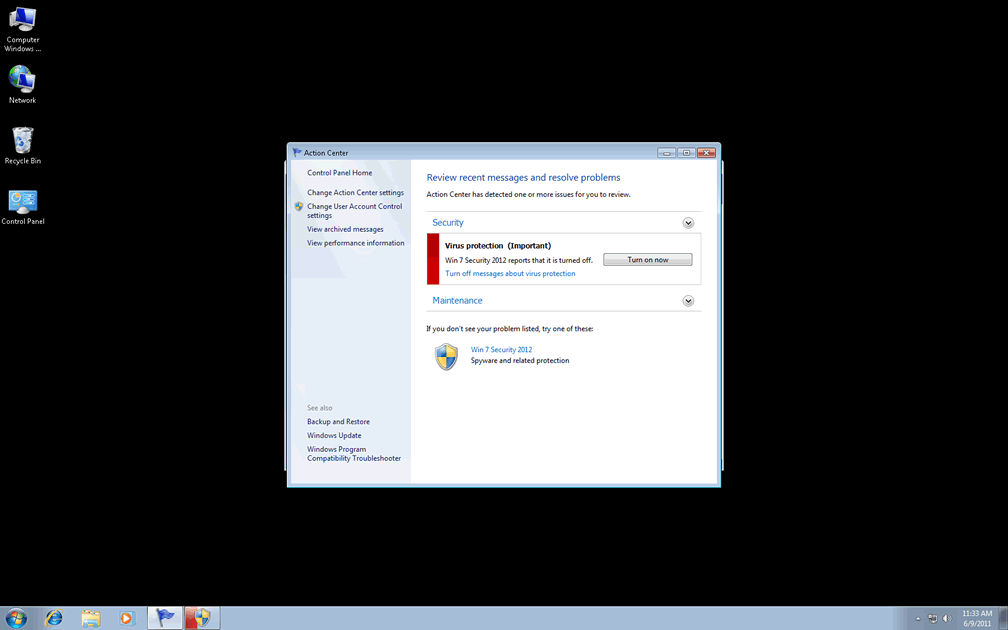
Don’t Fall for the Win 7 Security 2012 Scam
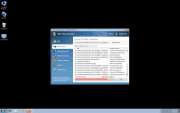
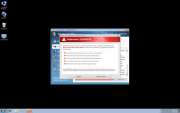
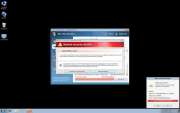
Win 7 Security 2012 is a scam. This rogue security program is designed to prey on inexperienced users by making them think that their computer is under attack. It is, but from Win 7 Security 2012. Despite Win 7 Security 2012's authentic sounding name, this program is really a malicious security application that causes all sorts of problems on a user's computer. Win 7 Security 2012 then poses as a real security utility, to convince the computer user to purchase Win 7 Security 2012. Users terrified of losing the information on their computers fall for the scam, giving Win 7 Security 2012 their credit card information. Of course, giving Win 7 Security 2012 your credit card information is useless, since this fake security program is not equipped to stop any kind of infection, and Win 7 Security 2012 is itself an invasive rogue anti-spyware program.
The Defining Feature of Win 7 Security 2012 and the Ppn.exe Process
There are dozens of known versions of the Ppn.exe process, and new ones are discovered every single day. However, unlike previous spyware, these cannot properly be called clones. Instead, they are all the same program downloading different skins corresponding to the infected computer. Ppn.exe changes identities depending on the user's operating system. Win 7 Security 2012 will rarely infect, if ever, a computer running Windows Vista or Windows XP. These systems would be infected by a version of Ppn.exe which is appropriate for that specific operating system. For example, XP Security 2012 for Windows XP, or Vista Security 2012 for Windows Vista.
The Ppn.exe Infiltration and Adaptation Process
Ppn.exe first infiltrates a computer through a Trojan, probably downloaded inadvertently from a dodgy website. This Trojan delivers Ppn.exe into the computer that is being attacked, by displaying a notification that is very similar to the ones displayed by Windows Automatic Update. Most users will simply click on it as they would with any other automatic update. This will start the Win 7 Security 2012 installation process. The program will detect the operating system being used and will then download one of three sets of skins appropriate for that operating system. These three sets of skins correspond to the three main Windows operating systems: Windows XP, Windows Vista, and Windows 7. Each of these sets includes a great number of different possible names and designs to mimic a legitimate anti-spyware application. Ppn.exe will also alter the registry so that Win 7 Security 2012 will be started up along with the operating system. The next time the user starts up Windows, he will be greeted by the Win 7 Security 2012 splash screen. The program will perform a fake scan and return numerous false positive results. Then Win 7 Security 2012 will prompt the user to enter his credit card information.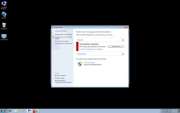
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| Comodo | TrojWare.Win32.Trojan.Agent.Gen |
| Kaspersky | HEUR:Trojan.Win32.Generic |
| NOD32 | a variant of Win32/Kryptik.QUY |
| Kaspersky | Trojan.Win32.FakeAV.ecou |
| AVG | Generic23.CFUB |
| Ikarus | Trojan.Cryptic |
| GData | Win32:Renosa-J |
| Sophos | Mal/FakeAV-MQ |
| DrWeb | Trojan.AVKill.2 |
| BitDefender | Trojan.Generic.KD.302340 |
| Kaspersky | UDS:DangerousObject.Multi.Generic |
| Avast | Win32:Renosa-J [Wrm] |
| Symantec | Trojan.Gen.2 |
| NOD32 | a variant of Win32/Kryptik.QVV |
| Panda | Suspicious file |
SpyHunter Detects & Remove Win 7 Security 2012
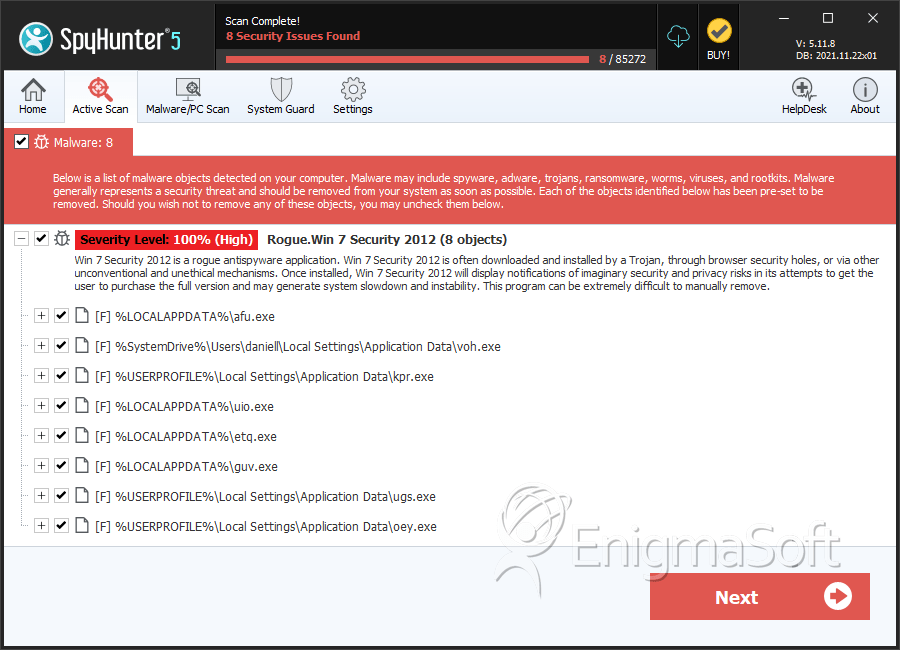
Win 7 Security 2012 Video
Tip: Turn your sound ON and watch the video in Full Screen mode.
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | afu.exe | e86a084051e4fb393b282858357e6a79 | 2 |
| 2. | voh.exe | 22fab34f18e5a7e564d4c546b0d4fca4 | 2 |
| 3. | kpr.exe | 16eea9f8977d11cbd3a3d80fafdef3cb | 2 |
| 4. | uio.exe | 953e9170934cfeccb7d4509a70274d4d | 1 |
| 5. | etq.exe | 784b903aefb5b895c65b20da699db29c | 1 |
| 6. | guv.exe | ccfbc220b145119da810362bee192638 | 1 |
| 7. | ugs.exe | 3241489ed05497104d196812ea610a8d | 1 |
| 8. | oey.exe | c61f2496eb9da3c68d5c7129572be209 | 1 |
| 9. | auf.exe | 8b7f140ecd9593fee3c86b607afdc8bd | 1 |
| 10. | cil.exe | c634de87f21ee489080d2845c83a7566 | 1 |
| 11. | fvg.exe | 65e061905342551e8bc9ead11c0d17ba | 1 |
| 12. | mbw.exe | 1fe4e5893ef9b3b03dbc1bcea96923c4 | 1 |
| 13. | xwo.exe | 63edc3d8270df5d5da81ffc654a8e9be | 1 |
| 14. | nur.exe | 12d802c56e02606be89f0f7807833c83 | 1 |
| 15. | %LocalAppData%\ppn.exe | ||
| 16. | %AppData%\Local\[RANDOM CHARACTERS].exe | ||
| 17. | %AppData%\Local\[RANDOM CHARACTERS] | ||
| 18. | %LocalAppData%\U3F7PNVFNCSJK2E86ABFBJ5H | ||
| 19. | %Temp%\[RANDOM CHARACTERS] | ||
| 20. | %AppData%\TEMPLATES\U3F7PNVFNCSJK2E86ABFBJ5H | ||
| 21. | %AllUsersProfile%\[RANDOM CHARACTERS] | ||
| 22. | %AppData%\Roaming\Microsoft\Windows\Templates\[RANDOM CHARACTERS] |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.