Vista Security 2012
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 5 |
| First Seen: | August 9, 2011 |
| OS(es) Affected: | Windows |
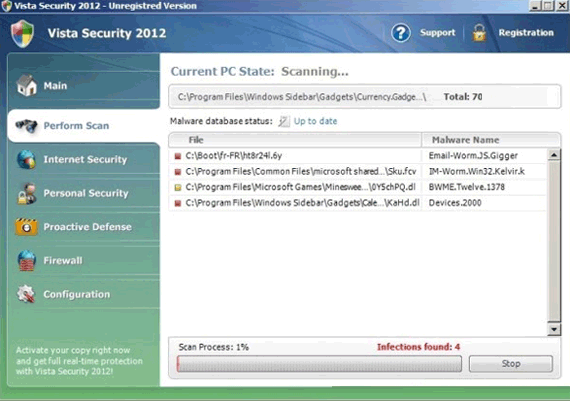
Vista Security 2012 Image
Vista Security 2012 is one of the dozens of different clones of the Ppn.exe process that have flooded the Internet since the beginning of 2012. This rogue anti-spyware application has caught the attention of security experts worldwide, because Vista Security 2012 has a unique feature. Vista Security 2012 changes names and themes according to the user's operating system. That means that instead of there only being one piece of harmful spyware named Vista Security 2012, there are dozens of versions of the same program, which changes according to the computer they are infecting.
Table of Contents
Understanding the Rogue Program Clones Brought by Ppn.exe
New rogueware clones brought by the Ppn.exe process are released every day. There are three main sets of clones. A set corresponding to Windows XP operating systems, a set for Windows 7 operating systems, and a Windows Vista set. Vista Security 2012 is one of the many clones corresponding to the set for Windows Vista. Vista Security 2012's counterparts in the other two sets would be named XP Security 2012 and Win 7 Security 2012 with themes or skins, corresponding to those operating systems. However, what makes the file Ppn.exe unique is that all of these are the same exact program, rather than different processes like previous rogue anti-spyware applications in the same family. After Ppn.exe enters a computer system, usually through a Trojan, part of the installation process is downloading the name and skins corresponding to the computer's operating system. This makes Ppn.exe harder to tell apart from the real thing than previous harmful software from the same family.
Special Considerations for Removing Vista Security 2012
Removing the Ppn.exe process can be done either manually, or with a legitimate anti-virus or anti-malware program. However, the scripts contained by Vista Security 2012 can block the Task Manager and certain system folders, making the removal of Vista Security 2012 much more difficult. Entering one's credit card information is completely useless and should not be done under any circumstances. However, entering the registration code 1147-175591-6550 can stop the constant system alerts and make removal easier. This will not remove Vista Security 2012 from a computer system, but will alleviate some of the symptoms.
Don’t Fall for Vista Security 2012’s Scam
Vista Security 2012 and similar malicious software are designed to prey on inexperienced users. Unlike traditional computer viruses that only attack a computer system, these programs also mess with your head. All of the disruptions caused by Vista Security 2012 and the Ppn.exe process are meant to frighten users into thinking that their system is infected by numerous viruses. Then Vista Security 2012 offers itself as a solution, if the user enters his credit card information. Don't fall for this; legitimate anti-virus applications will never block your computer or restrict your access to certain parts of your own system. They will also never change your browser settings or block access to the Internet. The point of Vista Security 2012 is to make you panic and get you to pay when you aren't thinking clearly. Stay calm, and don't make any hasty decisions. Use a legitimate security program or consult an expert to get rid of the Ppn.exe process. If you have already entered your credit card details, you should call your credit card provider and block the charges.
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| Panda | Trj/CI.A |
| AVG | Generic23.ALZH |
| Sophos | Mal/Generic-L |
| BitDefender | Trojan.Generic.KDV.275958 |
| NOD32 | a variant of Win32/Kryptik.PUI |
| Kaspersky | UDS:DangerousObject.Multi.Generic |
| Panda | Adware/XPSecurity2011 |
| Ikarus | Hoax.Win32.ExpProc |
| DrWeb | Trojan.FakeAV.7824 |
| BitDefender | Trojan.Generic.KD.265174 |
| Kaspersky | Hoax.Win32.ExpProc.acxb |
| Symantec | Unvirex!gen1 |
| NOD32 | a variant of Win32/Kryptik.PKH |
| McAfee | FakeAlert-Rena.p |
| Panda | Adware/XPAntivirus2011 |
SpyHunter Detects & Remove Vista Security 2012
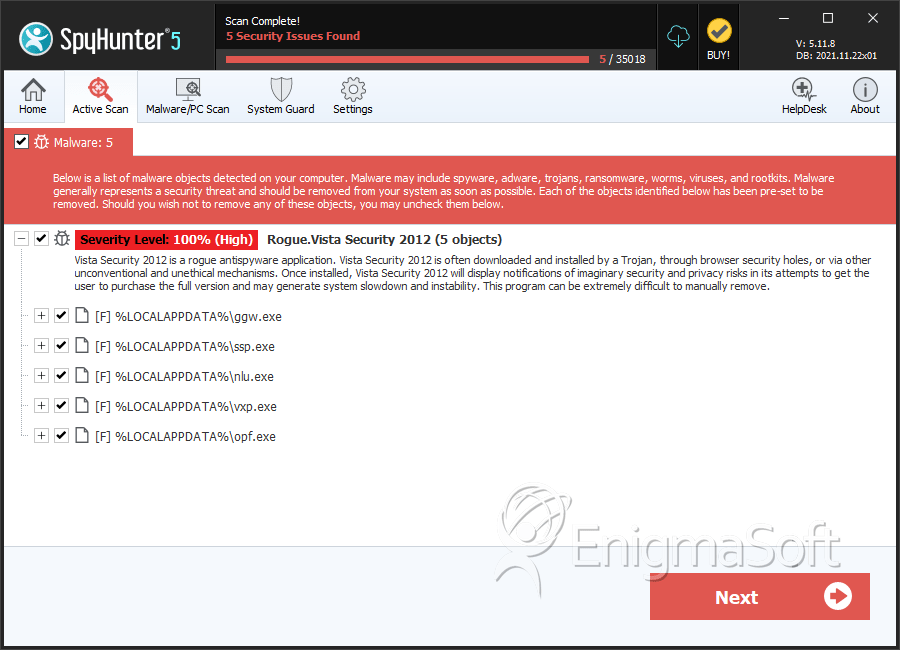
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | ggw.exe | dbdd0edf3fae9e277b7245f2a570cb53 | 1 |
| 2. | ssp.exe | 5c991c7ded7060d69e4844d54f42eaef | 1 |
| 3. | nlu.exe | c40c11b255169ea9a2a96419aa89b63e | 1 |
| 4. | vxp.exe | 2de65fde22d7ed7082f6ae2a3f1c8224 | 1 |
| 5. | opf.exe | 8afe2278f2a8fe1d97f1bc3ac982d1a7 | 1 |
| 6. | %LocalAppData%\kdn.exe | ||
| 7. | kdn.exe | ||
| 8. | ppn.exe | ||
| 9. | %%AppData%\Roaming\Microsoft\Windows\Templates\67sdh53ygdhilutew20ijnbgc | ||
| 10. | %LocalAppData%\u3f7pnvfncsjk2e86abfbj5h | ||
| 11. | %AppData%\Local\67sdh53ygdhilutew20ijnbgc | ||
| 12. | %UserProfile%\Templates\u3f7pnvfncsjk2e86abfbj5h | ||
| 13. | %AllUsersProfile%\67sdh53ygdhilutew20ijnbgc | ||
| 14. | %AllUsersProfile%\Application Data\u3f7pnvfncsjk2e86abfbj5h | ||
| 15. | %Temp%\u3f7pnvfncsjk2e86abfbj5h |

