XiaoBa Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
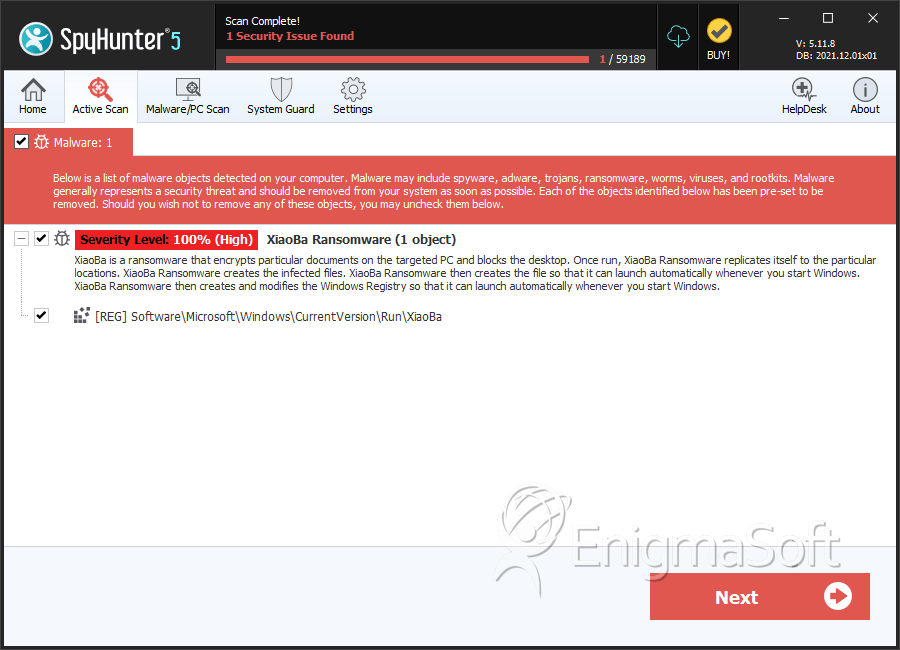
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 71 |
| First Seen: | October 30, 2017 |
| Last Seen: | May 2, 2022 |
| OS(es) Affected: | Windows |
The XiaoBa Ransomware is an encryption ransomware Trojan that is used to carry out attacks on Chinese victims. However, there is nothing stopping the XiaoBa Ransomware from attacking targets in other countries. However, computer users may be confused by the appearance of a ransom note on their computers written entirely in Chinese. The XiaoBa Ransomware carries out a typical encryption ransomware attack, encrypting the victim's files and then demanding a ransom from the victim. Because of this, you must take precautions against the XiaoBa Ransomware and the numerous other encryption ransomware Trojans that carry out similar attacks.
Table of Contents
What the XiaoBa Ransomware Does with Your Files
The XiaoBa Ransomware carries out an effective encryption ransomware attack, making the victim's files inaccessible. The XiaoBa Ransomware is delivered to victims through bogus versions of pirated software or software updates. It is also possible for the XiaoBa Ransomware to spread using spam email attachments, which will often be linked to spam email social engineering campaigns designed to trick computer users into downloading and installing the XiaoBa Ransomware onto their computers.
How the XiaoBa Ransomware Carries out Its Attack
The XiaoBa Ransomware encrypts the victim's files using a strong encryption algorithm. It seems that the XiaoBa Ransomware has several layers of obfuscation and uses compromised websites as Command and Control servers to hide its activities from PC security researchers. Many encryption ransomware Trojans mark the victim's files with custom extensions after an attack. The XiaoBa Ransomware will use numerous extensions to mark the victim's files, with numbers from '.XiaoBa1' to '.XiaoBa34.' The XiaoBa Ransomware will encrypt the targeted files and rename these files to add a file extension to the end of the affected file, which is the string '.XiaoBa' followed by a number from 1 to 34. The XiaoBa Ransomware targets the user-generated files while avoiding the Windows system files. This is because threats like the XiaoBa Ransomware need Windows to continue to function after the attack so that the victim can carry out the ransom payment. A few examples of the files types that the XiaoBa Ransomware targets in its attack are:
.3gp, .7z, .apk, .avi, .bmp, .cdr, .cer, .chm, .conf, .css, .csv, .dat, .db, .dbf, .djvu, .dbx, .docm, ,doc, .epub, .docx .fb2, .flv, .gif, .gz, .iso .ibooks,.jpeg, .jpg, .key, .mdb .md2, .mdf, .mht, .mobi .mhtm, .mkv, .mov, .mp3, .mp4, .mpg .mpeg, .pict, .pdf, .pps, .pkg, .png, .ppt .pptx, .ppsx, .psd, .rar, .rtf, .scr, .swf, .sav, .tiff, .tif, .tbl, .torrent, .txt, .vsd, .wmv, .xls, .xlsx, .xps, .xml, .ckp, .zip, .java, .py, .asm, .c, .cpp, .cs, .js, .php, .dacpac, .rbw, .rb, .mrg, .dcx, .db3, .sql, .sqlite3, .sqlite, .sqlitedb, .psd, .psp, .pdb, .dxf, .dwg, .drw, .casb, .ccp, .cal, .cmx, .cr2.
The XiaoBa Ransomware will change the infected computer's desktop image and drop three files, named as decryptor, '_@XiaoBa@_.bmp' and '_@Explanation@_.hta' after encrypting the victim's files. The XiaoBa Ransomware's new desktop image features the XiaoBa Ransomware's ransom note, written in Chinese. The translation of the XiaoBa Ransomware's ransom note reads:
'Warning! Encrypted files!
All files are encrypted using the RSA-2048 AES-128 algorithm
Please don't try to crack, because you might corrupt the files
Only our decryptor can help you
If you see this wallpaper but do not see "XiaoBa" window, then your anti-virus software removed this decryption software.
If you want your files you need the program
Please find the decryption program or recover it from the anti-virus software
Run the decryption program and follow the instructions
Please send about 1,200 yuan = 180.81 $ worth of Bitcoin to the specified address
Bitcoin currency wallet: 1GoD72v5gDyWxgPuBph7zQwvR6bFZyZnrB
For more information click on _@Explanation@_.hta
Email: B32588601@163.com'
Dealing with the XiaoBa Ransomware
PC security analysts counsel computer users not to agree with the payment of the XiaoBa Ransomware ransom or contacting the team behind the XiaoBa Ransomware. Instead, computer users should restore the affected files from a backup copy. File backups combined with a reliable malware removal program that is fully up-to-date are the best way to deal with threats like the XiaoBa Ransomware.
SpyHunter Detects & Remove XiaoBa Ransomware