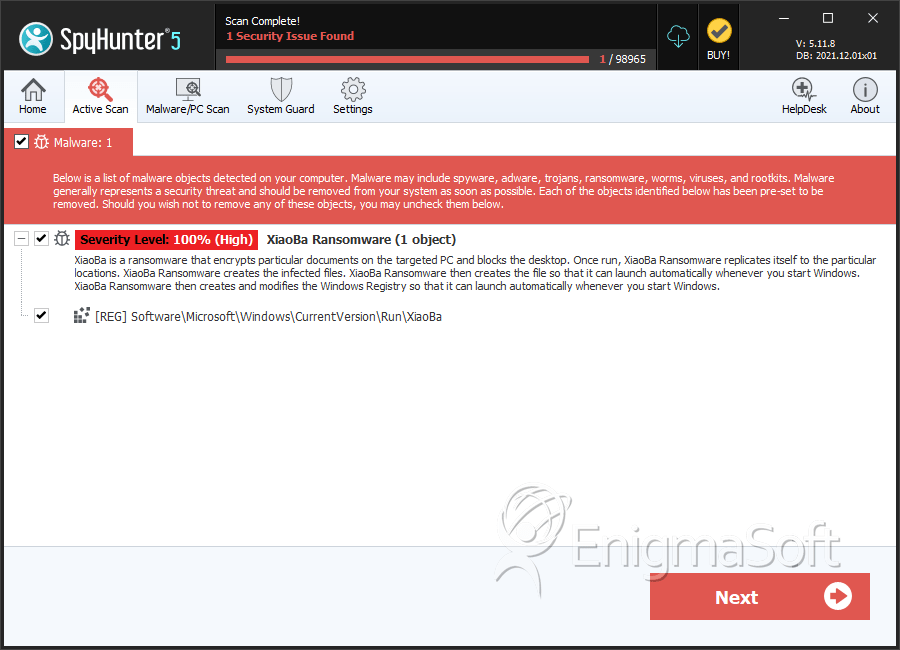
XiaoBa 2.0 Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 71 |
| First Seen: | October 30, 2017 |
| Last Seen: | May 2, 2022 |
| OS(es) Affected: | Windows |
The XiaoBa 2.0 Ransomware is a second version of the XiaoBa Ransomware, an encryption ransomware Trojan spotted by PC security researchers previously, which targeted computer users in Chinese-speaking regions mainly. The most notable update in the XiaoBa 2.0 version is that it adds support for other languages, as well as tweaks to the encryption method and ransom demand. The XiaoBa 2.0 Ransomware can infect computer systems in a variety of ways and be installed via compromised Remote Desktop Protocol connections, corrupted spam email attachments, or when computer users download a damaged file disguised as something else. The XiaoBa 2.0 Ransomware, like most encryption ransomware Trojans, was developed to block the victims' files by encryption them with a strong algorithm, which will make their contents inaccessible to then demand a ransom payment from the victim.
Table of Contents
How the XiaoBa 2.0 Ransomware can Keep Your Files Hostage
The XiaoBa 2.0 Ransomware uses the AES encryption to make the victim's files inaccessible, renaming all the encrypted files by adding the file extension '[xiaoba_666@163.com]Encrypted_.XIAOBA' to each affected file. The XiaoBa 2.0 Ransomware targets the user-generated files, which may include files with the following file extensions:
.ebd, .jbc, .pst, .ost, .tib, .tbk, .bak, .bac, .abk, .as4, .asd, .ashbak, .backup, .bck, .bdb, .bk1, .bkc, .bkf, .bkp, .boe, .bpa, .bpd, .bup, .cmb, .fbf, .fbw, .fh, .ful, .gho, .ipd, .nb7, .nba, .nbd, .nbf, .nbi, .nbu, .nco, .oeb, .old, .qic, .sn1, .sn2, .sna, .spi, .stg, .uci, .win, .xbk, .iso, .htm, .html, .mht, .p7, .p7c, .pem, .sgn, .sec, .cer, .csr, .djvu, .der, .stl, .crt, .p7b, .pfx, .fb, .fb2, .tif, .tiff, .pdf, .doc, .docx, .docm, .rtf, .xls, .xlsx, .xlsm, .ppt, .pptx, .ppsx, .txt, .cdr, .jpe, .jpg, .jpeg, .png, .bmp, .jiff, .jpf, .ply, .pov, .raw, .cf, .cfn, .tbn, .xcf, .xof, .key, .eml, .tbb, .dwf, .egg, .fc2, .fcz, .fg, .fp3, .pab, .oab, .psd, .psb, .pcx, .dwg, .dws, .dxe, .zip, .zipx, .7z, .rar, .rev, .afp, .bfa, .bpk, .bsk, .enc, .rzk, .rzx, .sef, .shy, .snk, .accdb, .ldf, .accdc, .adp, .dbc, .dbx, .dbf, .dbt, .dxl, .edb, .eql, .mdb, .mxl, .mdf, .sql, .sqlite, .sqlite3, .sqlitedb, .kdb, .kdbx, .1cd, .dt, .erf, .lgp, .md, .epf, .efb, .eis, .efn, .emd, .emr, .end, .eog, .erb, .ebn, .ebb, .prefab, .jif, .wor, .csv, .msg, .msf, .kwm, .pwm, .ai, .eps, .abd, .repx, .oxps, .dot.
The XiaoBa 2.0 Ransomware delivers its ransom note in the form of an HTA file named HELP_SOS.hta, which contains the following text:
'File Recovery Guide
You may have noticed that your file could not be opened and some software is not working properly.
This is not wrong. Your file content still exists, but it is encrypted using "XIA08A 2.0 Ransomware".
The contents of your files are not lost and can be restored to their normal state by decryption.
The only way to decrypt a file is to get our 'RSA 4096 decryption key" and decrypt it using the key.
Please enter 0.5 bitcoin into this address: [random characters]
Please contact E-Mail after completing the transaction xiaoba_666@l63.com
Send the file that needs to be decrypted to complete the decryption work
Using any other software that claims to recover your files may result in file corruption or destruction.
You can decrypt a file for free to ensure that the software can recover all your files.
Please find someone familiar with your computer to help you.
You can find the same guide named "HELP_SOS.hta" next to the encrypted file.'
Dealing with the XiaoBa 2.0 Ransomware
The XiaoBa 2.0 Ransomware ransom amount is close to 4,000 USD, and there is no guarantee that the criminals will keep their promise and help victims recover their data. This is what makes malware researchers advise computer users to use file backups to ensure that their data is safe from threats like the XiaoBa 2.0 Ransomware. Apart from file backups, a suitable security program that is fully up-to-date can prevent the XiaoBa 2.0 Ransomware from being installed if there is a trustworthy security program installed and running. This is why any computer user should be aware of how threats like the XiaoBa 2.0 Ransomware are distributed so that they can ensure that appropriate safeguards are in place.
SpyHunter Detects & Remove XiaoBa 2.0 Ransomware