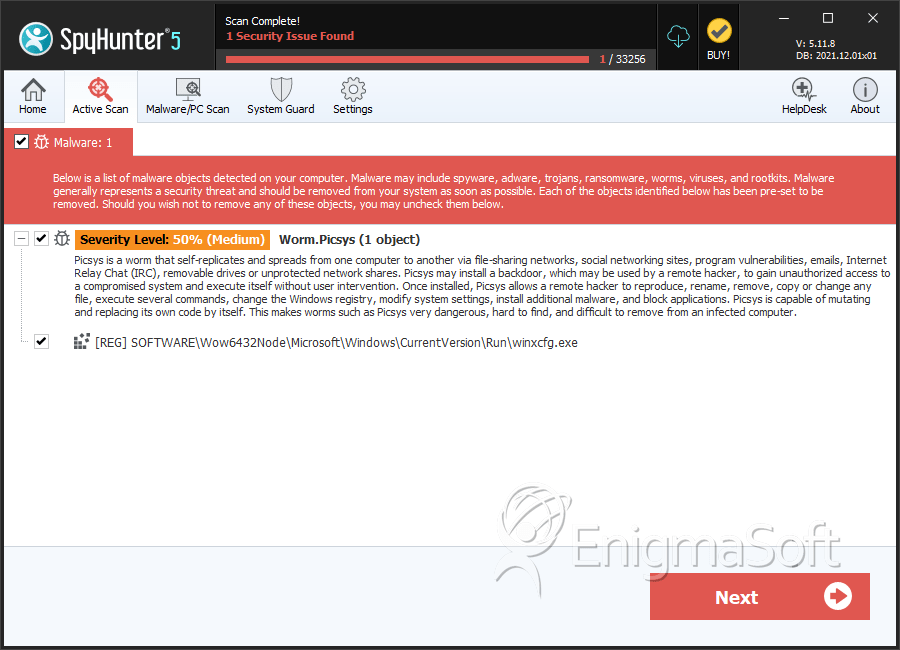
Worm.Picsys
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 50 % (Medium) |
| Infected Computers: | 71 |
| First Seen: | January 16, 2013 |
| Last Seen: | May 2, 2022 |
| OS(es) Affected: | Windows |
The Picsys malware falls into the category of Worms, which are specialized threatening programs that can replicate themselves. The Worm.Picsys malware is packed as an executable DLL and may be delivered to users via spam emails and Trojan-Droppers like Rovnix and Calimocho. You may be interested to know that computer worms like Picsys do not require instructions from 'Command and Control' servers and can run independently. The Worm.Picsys cyber threat may be used to gather sensitive information and files from infected computer systems. The Worm.Picsys malware can spread via WiFi and LAN networks as well as virtual LAN networks. Security authorities report that the Picsys Worm is equipped with software exploits and a hard coded database of logins that might allow it to penetrate most firewalls and sandboxes. The payload of the Picsys Worm is encoded with the Yoda's Crypter and may prove to be hard to detect. Most versions of the Picsys malware are tagged as Worm.Picsys.CC1, Worm/Picsys.A, Win32.Worm.P2p.Picsys.C and Win32.HLLW.Morpheus.3.
The Picsys Worm is known to inject code into winxcfg.exe and launch a clone of the file if necessary. The Picsys malware may allow its handler to make modifications to the file system of the infected computer, and change variables in the Windows Registry potentially. Samples of the Picsys Worm have been found on corporate servers across the globe, which suggest that the Picsys malware is used for corporate espionage actively. Worms like Picsys, Dunihi and Arcdoor may be valuable to APT groups that seek to map and infect targeted networks, and users should not rely on endpoint protection solely. Security authorities advise users to make the first step in countering the Picsys Worm by disabling Autorun files to be executed without the proper runtime scan. Additionally, employing the services of a trustworthy anti-malware shield can limit the attack surface of your PC significantly.
SpyHunter Detects & Remove Worm.Picsys


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.