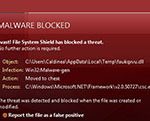
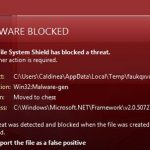
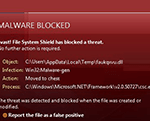
Win32 malware.gen
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 4,476 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 22,473 |
| First Seen: | July 24, 2009 |
| Last Seen: | February 3, 2026 |
| OS(es) Affected: | Windows |
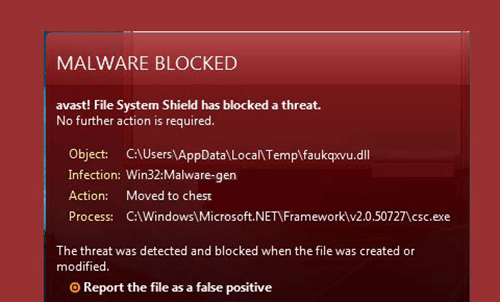
Win32 malware.gen Image
Win32 Malware.gen is a so-called generic threat - a suspicious file fetched by an anti-virus scan that appears to be malicious but does not match any of the definitions of known malware threats contained in the anti-virus software's database. Therefore, an alert from an anti-malware program for a Win32 Malware.gen detection indicates that there is a 32-bit file on a Windows operating system that should be flagged for further inspection. An infection generally described as Win32 Malware.gen is thus a heuristic detection designed to indicate the presence of some kind of a yet undetermined Trojan horse for Windows PCs. It is also possible that files reported as a Win32 Malware.gen infection are actually clean, whereby in this case no further actions on the side of the user are necessary. If malicious though, once installed on a computer, the file alters the system setting and registry which will eventually lead to overall poor performance and a series of undesired security issues. This type of malware could also contain additional malicious codes that can open a backdoor for remote access to the affected device. Particularly annoying is also the fact that this threat can reinstall itself on one and the same system multiple times if its core files have not been deleted. At the same time, there are no visible symptoms, as with any Trojan horse infection. Trojan horses detected by the Win32.Malware.gen definition are capable of performing tasks like installing additional malware, modifying Windows system files, stealing personal details, as well as redirecting users to suspicious domains filled with intrusive ads. Removal can be tricky and usually requires a professional removal tool.
Table of Contents
The Immense and Silent Damage Potential
Malicious programs which are known to exhibit the characteristics of a Win 32 Malware.gen infection operate in an invisible manner. All these hazardous programs have immense potential to perform a wide range of activities that could impose massive damage on the infected computer. What makes this type of malware even more dangerous is the fact that the user does not notice anything of the harmful processes that are running while the virus is working towards achieving its primary goals. Users should be prepared and should be aware of what is coming to them if they do not remove the malware immediately. The most dangerous functionality of the virus is its ability to download and install additional tools on the infected machine, which in turn, could have a variety of malicious functions. Some of the various tasks that a Win 32 Malware.gen payload could be programmed to perform are, therefore, the following:
- Open a backdoor that will provide the attackers with remote access to the affected PC
- Turn the computer into a bot controlled by the hackers
- Install a spying tool/keylogger that collects sensitive data and sends it to cybercriminals
- Display pop-up windows that urge the user to download fake updates of legit programs
- Modify the installed Internet browsers to inject corrupted ads and hyperlinks to the web pages the user visits
Obviously, malware threats from the Win32 Malware.gen group disrupt massively the performance of the infected computer. They can be exploited by hackers to delete or corrupt important Windows system files, making a device not fully functional, or even crashing it down completely. The ability to install spying tools is another feature that deserves special attention. Cyber espionage programs that could be dropped on a computer by a Win32.Malware.gen threat are able to switch on the available recording devices of a system, such as webcams and microphones, and then make video or audio recordings to stalk on the device's owner. Keyloggers, on the other hand, can record all keystrokes made on a keyboard, meaning that they will capture the victim's usernames, passwords, credit card details and so on, and then send these to the malware's owners, providing the cybercriminals with access to all online accounts of the user and with his or her credit card data. The crooks are often also after data related to a targeted user's job and could be willing to collect details about the projects the user is working on for the sake of industrial espionage.
In other cases, a computer's resources could be the actual target of the attackers. Win32 Malware.gen infections can turn a computer into a bot - a machine completely controlled by hackers who then exploit its operating capacity for various illegal purposes like online fraud, DDoS attacks, and many others. Furthermore, many Trojans from the Win 32.Malware.gen-type are also designed to distribute Ransomware threats which encrypt critical files on the affected computer and demand the payment of ransom from the user for a decryption key. Typically, the locked data is never recovered as either the user does not get any decryption key at all, or the one provided by the criminals does not work.
Ways to Spread
Just like the numerous ways that a Win32 Malware.gen infection could harm a Windows computer, it also has many channels of distribution. Win32 malware.gen is able to spread through malicious websites, as well as embedded into torrents in file-sharing networks. However, its favorite way to infiltrate a computer is through obfuscated e-mail attachments, fake updates of software applications, or cracked programs. In any case, a Trojan cannot enter a system without any human interaction, so the attackers need to rely on social engineering techniques to spread the malware rather than exploit system vulnerabilities. To summarize, the tricky ways to persuade a user into downloading and installing the malicious payload include:
- Opening an infected attachment to an email that uses the names/logos of a well-known company, a state institution, or a famous person
- Downloading and installing fake updates of legit software programs
- Clicking on a corrupted link or an eye-catching ad on the Internet
- Downloading shareware/freeware with an embedded malware code
Having all that in mind, there are some cybersecurity tips that users can follow in order to prevent infection with such a dangerous Trojan. Never open suspicious e-mail attachment from unknown senders, do not click on aggressive pop-up windows or security alerts, install software and its updates only from the official website of the developer, avoid visiting websites that are known to have a high risk of malicious scripts (like gambling, adult-themed, or gaming websites), do not download and install files from P2P networks. Finally, install a reliable anti-virus solution that offers real-time protection and has an updated base of malware definitions.
Aliases
A Win32 Malware.gen infection can be detected under many different names. Some of the names under which most anti-malware applications detect a Windows32 Malware.gen threat are aspnet_compiler.exe, BrowserAir, RedBoot, WinSec, Wooly, Filelce, and Revenge. These are all malware threats that lead to data loss, identity theft, stolen online banking credentials, encrypted files, poor browsing experience, overall sluggish PC performance, and many other undesired side effects. Cleaning your machine of this types of malware is, therefore, of crucial importance.
Aliases
15 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| Antiy-AVL | VCS/Environment.DigitalFN |
| AVG | Agent2.CBME |
| Fortinet | W32/BHO.AQ!tr |
| Ikarus | Trojan.BHO |
| AhnLab-V3 | Dropper/Bho.221184 |
| Microsoft | TrojanDownloader:Win32/Regonid.A |
| Antiy-AVL | Trojan/win32.agent.gen |
| Sophos | Mal/BHO-AY |
| BitDefender | Trojan.Generic.5408453 |
| Kaspersky | HEUR:Trojan.Win32.Generic |
| eSafe | Win32.TRBHO.Dl |
| McAfee | Generic.dx!vpv |
| ClamAV | Win.Trojan.Agent-68510 |
| Comodo | TrojWare.Win32.TrojanDownloader.Swizzor.Gen |
| Fortinet | Riskware/Ardamax |
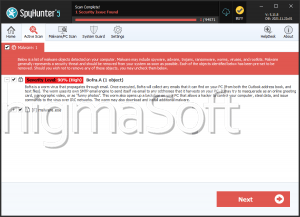
SpyHunter Detects & Remove Win32 malware.gen
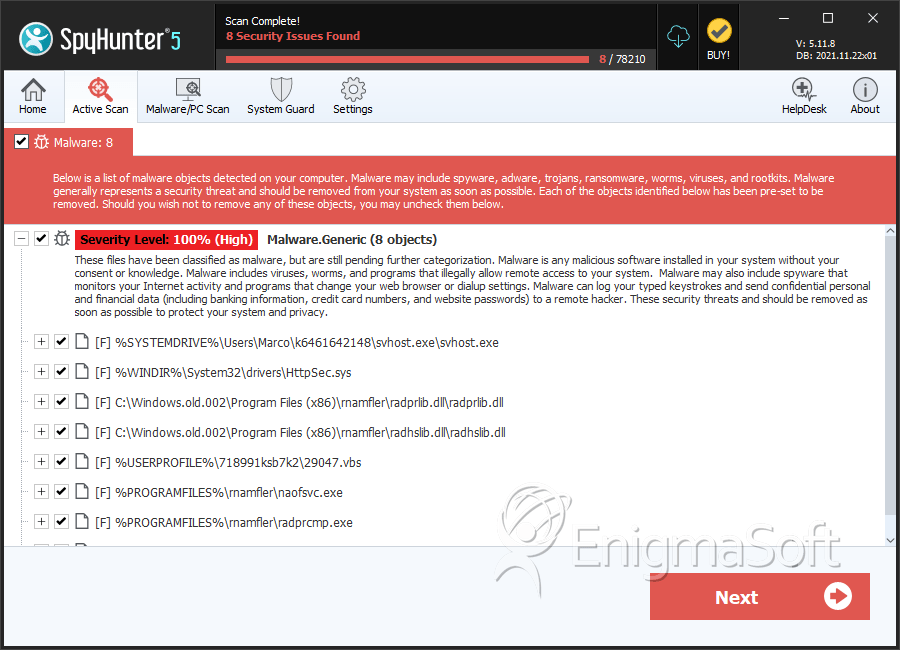
Win32 malware.gen Screenshots
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | svhost.exe | 6a93a4071cc7c22628af40a4d872f49b | 9,742 |
| 2. | radprcmp.exe | f40251bda02e554a4f6721436cd720de | 641 |
| 3. | httpsec.sys | da2411237a40b8cfc775fc25d7463a60 | 295 |
| 4. | radprlib.dll | 52c6d734c288a026f2b19ce6bbefa302 | 258 |
| 5. | radhslib.dll | 54fc6b247afa41b7a4b24bca0d911d40 | 207 |
| 6. | naofsvc.exe | a12135effabb3b40b01c723d4958a37d | 2 |
| 7. | naomf.exe | df19fb8d135fa3a2b3aa6f0abc8a9649 | 2 |
| 8. | svchost.exe | d306de53ce9a97060e4f686566c40bc6 | 2 |
| 9. | SMcoc.exe | b7114bd26cadc3c9db1fe918165cfbe8 | 1 |
| 10. | 29047.vbs | 1fcdd9fd021d815e25a716660814dee8 | 1 |
| 11. | document.exe | dae4bc7cf2df5e00e8f8cbdeba9b9976 | 0 |