VirTool:Win32/Obfuscator.XX
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 2,653 |
| First Seen: | December 20, 2010 |
| Last Seen: | October 2, 2025 |
| OS(es) Affected: | Windows |
Microsft Windows has built-in essential security mechanisms that may notify PC users of a detected VirTool:Win32/Obfuscator.XX threat. Security experts note that the VirTool:Win32/Obfuscator.XX detection is a broad term that encompasses programs that are obfuscated deliberately to prevent runtime analysis and code execution prevention. Technically, VirTool:Win32/Obfuscator.XX may be a detection of ransomware, backdoor trojans, RATs, worms, viruses and trojan downloaders. Users that are presented with security alerts about VirTool:Win32/Obfuscator.XX should revise recently installed free programs, check their extension managers for suspicious additions and ensure that they are using the most recent version of Java and Adobe Flash Player. Given the broad spectrum of malware that could be detected as VirTool:Win32/Obfuscator.XX you should take into consideration that most cyber threats are propagated as attachments to spam mail, and you may want to check your Downloads folder.
VirTool:Win32/Obfuscator.XX may appear as an archive file but don't be fooled by its icon because it may have a double file extension and prove to be an executable program. The VirTool:Win32/Obfuscator.XX malware may contain the payload of threats like CrypVault and TorrentLocker that are famous for their obfuscation techniques. Advanced obfuscation methods can be seen in Xpiro and AutoIt/Fadef that could extract valuable credentials from infected systems. Computer users should employ the services of a renowned anti-malware solution to prevent malware in the VirTool:Win32/Obfuscator.XX category from running on their PC, steal valuable data and install other malware.
Table of Contents
Aliases
15 security vendors flagged this file as malicious.
| Antivirus Vendor | Detection |
|---|---|
| McAfee | Artemis!D46F296693C7 |
| McAfee-GW-Edition | Heuristic.LooksLike.Win32.Suspicious.F |
| McAfee | Generic.grp!ec |
| CAT-QuickHeal | (Suspicious) - DNAScan |
| Fortinet | W32/Black.A!tr |
| Ikarus | Trojan.Win32.Scar |
| AntiVir | TR/Dropper.Gen |
| Avast | Win32:Banker-KBN [Trj] |
| McAfee | Artemis!2EC3705B6072 |
| Symantec | WS.Reputation.1 |
| NOD32 | probably a variant of Win32/Spy.Banker.WUH |
| McAfee | Artemis!DBFBCDDED55E |
| Avast | Win32:Spyware-gen [Spy] |
| McAfee | Artemis!D2408DCF0EB3 |
| Ikarus | possible-Threat.Crack.TMPGEnc |
SpyHunter Detects & Remove VirTool:Win32/Obfuscator.XX
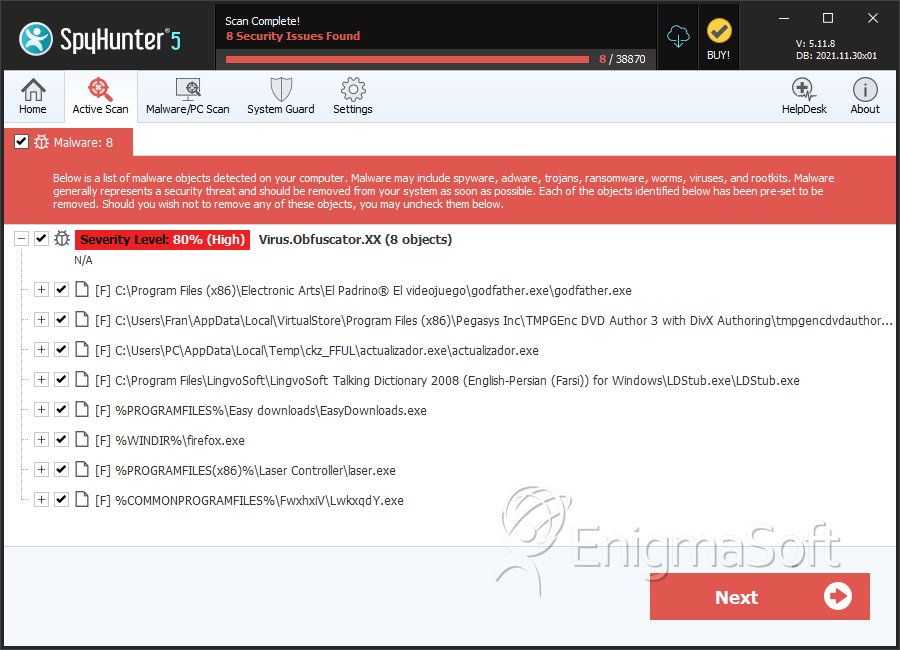
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | godfather.exe | 509241b364a0d311e4e819ce677f5d3d | 180 |
| 2. | tmpgencdvdauthor3.exe | fa491a0eb9cd1675e3d032cea2775c3f | 88 |
| 3. | actualizador.exe | 1f6e2ff217ad06c4cb40d9964f41b3fd | 60 |
| 4. | EasyDownloads.exe | f29e5a8475aace521e9993543754c786 | 46 |
| 5. | LDStub.exe | f897ad390168dfca209841fa8810841a | 44 |
| 6. | laser.exe | afb42069447d9c4164ba312deb5ce977 | 9 |
| 7. | temps.exe | 7da2c02cdfca6f5499976224f6feb727 | 9 |
| 8. | LwkxqdY.exe | 33a6fa202f48c1b9042d6980ff4a62e5 | 5 |
| 9. | Amado Batista Alucinação.exe | 20cedfad4359c817390dbdcc95f3ff3c | 5 |
| 10. | firefox.exe | d46f296693c7270622e112fd02f19eb0 | 4 |
| 11. | ipsechlp.exe | 30b2b3b7f3d3b37fea1113d00220fd8e | 3 |
| 12. | PSa74_2247.exe | 8e08b1e92a024386479c6bae9e70fae4 | 3 |
| 13. | waconsts.dll | 505d588b92a609931b07921345aa4add | 2 |
| 14. | nerACD.dll | c51b190e86e83e44697e292319437418 | 2 |
| 15. | GxvhdaB.exe | c5678e0508d6e4f5ed749e1419b62177 | 2 |
| 16. | wchksys.exe | bb759d37432e6d5d744214eebf7346ef | 2 |
| 17. | syst32.exe | a4270648b3e2496897cc5f300b435fa4 | 2 |
| 18. | tenthas.exe | dbfbcdded55eb8e4d9dbd492f91474a0 | 2 |
| 19. | mshicwer.dll | ae9ca423fdee3568885ae201104f2894 | 1 |
| 20. | IA882_2211.exe | 16dd0001a1c8b27ab4c2db3fcc3d0c61 | 1 |
| 21. | IAf8a_2164.exe | 2440c41dfe11f7ae1d3d3ee6f7b59523 | 1 |
| 22. | IA856_289.exe | 0b5487b3f6c401dcdda00c75901d6b89 | 1 |
| 23. | IA965_302.exe | 5dce68809f701a77de6eb3fa56c5b34d | 1 |
| 24. | Shell_Update.exe | 69276bab749f4f06e148031d68af92bf | 1 |
| 25. | 000003B214FA9539.exe | 63dbf019d5f1edf0abf53fc675fe6a72 | 1 |
| 26. | B6232F3A65D.exe | c2ff997255f81a0042b6b58e20d1ddcc | 1 |