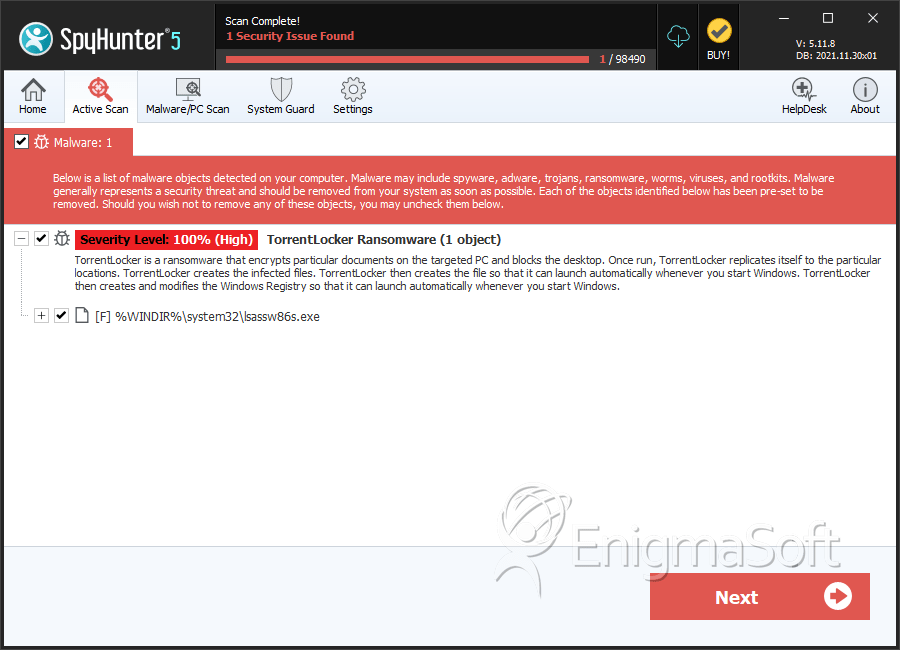
TorrentLocker Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 803 |
| First Seen: | August 19, 2014 |
| Last Seen: | June 29, 2021 |
| OS(es) Affected: | Windows |
As a new file encryptor Trojan that borrows its structure and aesthetics from previous, unrelated threats, the TorrentLocker Ransomware continues the overall theme of encrypting files on infected computers and then demanding illegal ransom fees to restore the affected files back to readability. Although the TorrentLocker Ransomware uses ransom messages that misidentify the TorrentLocker Rnmsomware as a variant of the CryptoLocker Virus deliberately, malware researchers have verified that the TorrentLocker Ransomware is unrelated to CryptoLocker (or similar PC threats) in terms of code. The same precautions in use against other ransomware also should be used to protect against the TorrentLocker Ransomware attacks, or remove the TorrentLocker Ransomware, if necessary.
Table of Contents
The Trojan File Locker with Less Originality than Malice
The TorrentLocker Ransomware was identified being circulated in recent phishing attacks, which may use e-mail attachments or mislabeled Web links to compromise vulnerable computers. Major TorrentLocker Ransomware campaigns, so far, have targeted Australian residents through fake e-mail-based invoice documents. Relevant file attachments are executable files, or EXE files, but are mislabeled to look like another, harmless file type, such as a text document. 'Parcel_information.exe' is one example of a file name used by the TorrentLocker Ransomware for its installation.
Like past ransomware families, the TorrentLocker Ransomware encrypts the files on your PC (using a relatively simple, Rijindael-based algorithm) to make them unreadable. The TorrentLocker Ransomware then displays ransom messages that resemble those of other, thoroughly-identified file lockers intentionally: CryptoLocker and CryptoWall Ransomware. However, malware experts have verified that the TorrentLocker Ransomware uses a weaker form of encryption than either of these two families, and is unrelated to them – except for superficially resembling them in its warning messages.
The TorrentLocker Ransomware does share a vulnerability in common with CryptoLocker and is unable to implement its file-encrypting attacks without first contacting its Command & Control server. Similarly, PCs that are compromised by the TorrentLocker Ransomware but lack Internet access also will be unaffected by current versions of the TorrentLocker Ransomware and its attacks. However, vulnerable machines, documents, audio files, images and other data could be encrypted and rendered potentially irretrievable.
Fighting Back Against the Torrent of File Lockers
Since the TorrentLocker Ransomware lacks major features besides copying the external details of other, more professionally-designed threat than itself, the TorrentLocker Ransomware currently is estimated to be unlikely to see the same in-depth development as other file encryptor Trojans. However, for victims who are affected, the TorrentLocker Ransomware may damage a wide range of files on your hard drive and may mislead some victims into paying its BitCoin ransom for file recovery. The TorrentLocker Ransomware also injects its primary file component into Explorer.exe, which is a normal Windows component, thus complicating identification or removal of the infection.
File types known to be targeted by the TorrentLocker Ransomware include documents like DOCX, XML spreadsheets, JPEG pictures and a range of other, specialized files, such as database files for SQLite software. Until the TorrentLocker Ransomware's servers are taken down by authorities, and its campaign brought to a halt, malware researchers encourage disconnecting infected PCs from the Internet and using anti-malware tools for deleting the TorrentLocker Ransomware (which, by default, will launch two separate copies of itself).
Instead of utilizing the TorrentLocker Ransomware's recommended BitCoin ransom to restore affected files, you should restore any files from a remote, uninfected backup. Due to the weakness of the TorrentLocker Ransomware's chosen encryption method relative to CryptoWall or CryptoLocker, it may only be a matter of time before third party tools for reversing the TorrentLocker Ransomware's attacks also become available to the public.
SpyHunter Detects & Remove TorrentLocker Ransomware
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | lsassw86s.exe | 2a3677209976516d5925140e56d2b3fc | 50 |
| 2. | lsassw86s.exe | bad2a98576d366faeb5285b0d40fad3c | 40 |
| 3. | lsassw86s.exe | dddb0f61a2464e5dd086d331edef9ed7 | 29 |
| 4. | lsassw86s.exe | 24cba908a0c694b3f7b01f9e06834dfb | 23 |
| 5. | lsassw86s.exe | c6cdf1ab343efcc37a3e617edb741017 | 23 |
| 6. | lsassw86s.exe | e507ad76527cd063c12798a1d6169837 | 15 |
| 7. | lsassw86s.exe | 33a2ac19e8c6c2ba26e9cab5b2d2b42c | 15 |
| 8. | lsassw86s.exe | ba4687e7af60c53bcc65bff2e2b65293 | 14 |
| 9. | lsassw86s.exe | 6c439da60aba9c17132e7676173689ee | 14 |
| 10. | lsassw86s.exe | eba596e4d56211596bcd711e2f877e60 | 11 |
| 11. | lsassw86s.exe | d85620cae65e8f0e994afcb79c7b0178 | 9 |
| 12. | lsassw86s.exe | 6f766b8e7b67e7118b55972a3b9c5f72 | 8 |
| 13. | lsassw86s.exe | 03bc5a3cf6221b57e22977abfc4a2978 | 8 |
| 14. | lsassw86s.exe | 6548ae9209723c67276629d30cc676d0 | 8 |
| 15. | lsassw86s.exe | cd88c44effa80d1eacefdd357934d9c7 | 7 |
| 16. | lsassw86s.exe | 33e6a5d26d9a427d270f0f0251dc3dce | 6 |
| 17. | lsassw86s.exe | ffe0bbe76e85a0285c1b0872911efaeb | 6 |
| 18. | lsassw86s.exe | 2b9ac3b518a724549b1870d994b4338c | 6 |
| 19. | lsassw86s.exe | be8174c65aa8b6ee80719bf64fd10de6 | 5 |
| 20. | lsassw86s.exe | e88b66496a794889c09d2917c185049b | 4 |
| 21. | lsassw86s.exe | 9794f91db5e133e1071b9b93fae10bcc | 4 |
| 22. | lsassw86s.exe | f265b5d9e0060a3203dbd2489f8c2b56 | 4 |
| 23. | lsassw86s.exe | 59b03095693ccf1ba32b3908d57c2ae6 | 4 |
| 24. | lsassw86s.exe | ae6c0969b3925f3f6de0f05b20b29244 | 4 |
| 25. | lsassw86s.exe | cb47181ccb0825195672c726e2487893 | 3 |
| 26. | lsassw86s.exe | 5848056b3093a661c3efdd8c5e22bd7a | 3 |
| 27. | lsassw86s.exe | c899164239f9d84be9035716a2435767 | 3 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.