Total Protect 2011
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 2 |
| First Seen: | September 23, 2011 |
| Last Seen: | January 7, 2026 |
| OS(es) Affected: | Windows |
Total Protect 2011 is a thinly veiled clone of Total Security, a rogue security program with dozens of different versions. Just a few of Total Protect 2011's many clones include Total Protect, Total Protect Antivirus Solution, Total Security, and Total Security 2011. Total Protect 2011 is a kind of malware infection that is designed to scam computer users by convincing them to spend their money on a useless fake security application. ESG security researchers consider that Total Protect 2011 is a dangerous threat to a computer system and that Total Protect 2011 is also part of a well-known scam. Falling for the Total Protect 2011 does not only mean losing the payment for this fake security program; it also means putting yourself at risk for identity theft and credit card fraud. If Total Protect 2011 is installed on your computer system, ESG security researchers recommend the use of a real, fully-updated anti-malware solution, to get rid of Total Protect 2011 as soon as possible.
Table of Contents
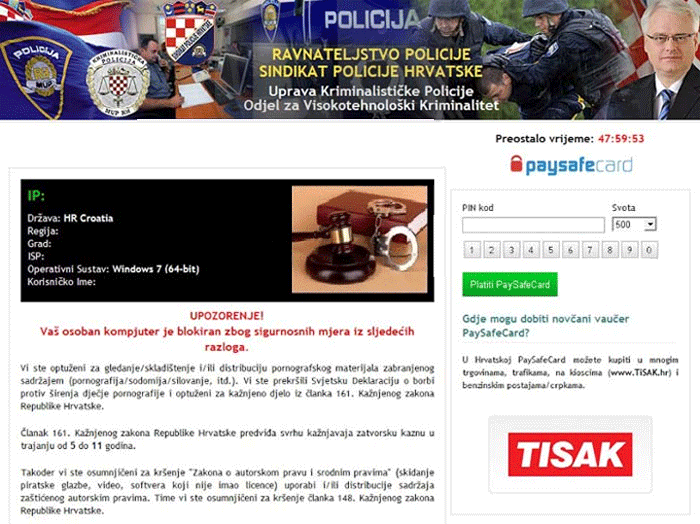
How the Total Protect 2011 Scam Works
Total Protect 2011 is part of a well-known Internet scam. Criminals use programs like Total Protect 2011 to take advantage of computer users that are not experienced with computer security or with the Internet in general. Basically, Total Protect 2011 is designed to cause a number of problems on a computer system. It, then, displays a large number of alarming messages, fake security alerts, and fake system errors. Total Protect 2011 does this so that a computer user will panic and think that Total Protect 2011 is a real security program that has detected a severe problem on the infected computer system. Not knowing that the problems are caused by Total Protect 2011 itself, inexperienced computer users often fall for this scam and purchase this fake security application. Spending your money on Total Protect 2011 will usually do nothing to stop the problems on your computer system. More importantly, putting your credit card information into the hands of the unscrupulous criminals that would use malware like Total Protect 2011 is probably not a good idea.
Additional Dangers Associated with Total Protect 2011
According to ESG malware analysts, there are other dangers associated with Total Protect 2011:
- Malware like Total Protect 2011 seldom comes alone. The presence of Total Protect 2011 on your computer means that there is a high probability of other malware on your hard drive.
- Total Protect 2011 is often installed through a Trojan or rootkit infection, which remains on your computer system even if you pay for the useless "full version" of Total Protect 2011.
- Total Protect 2011 can protect itself by making your security applications crash or blocking them altogether. Start up your computer in Safe Mode to bypass this "feature."
Analysis Report
General information
| Family Name: | Trojan.Banker.IC |
|---|---|
| Packers: | UPX! |
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
83a5ce5516bae53a59a436a5f140eab4
SHA1:
10c9e6360e00576909c8e78e485b5da0aec24e00
SHA256:
2D3177D8CFAB121BB452CA8389001B50C54C3233C3C4F884CD4DE66E79D36705
File Size:
253.44 KB, 253440 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have security information
- File has been packed
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- IMAGE_FILE_DLL is not set inside PE header (Executable)
Show More
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Traits
- dll
- packed
- WriteProcessMemory
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 2,991 |
|---|---|
| Potentially Malicious Blocks: | 14 |
| Whitelisted Blocks: | 2,977 |
| Unknown Blocks: | 0 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Similar Families
Similar Families
This section lists other families that share similarities with this family, based on EnigmaSoft’s analysis. Many malware families are created from the same malware toolkits and use the same packing and encryption techniques but uniquely extend functionality. Similar families may also share source code, attributes, icons, subcomponents, compromised and/or invalid digital signatures, and network characteristics. Researchers leverage these similarities to rapidly and effectively triage file samples and extend malware detection rules.- Banker.THA
- Delf.XB
- Injector.FGSA
- Injector.KDF
- Injector.KFAD
Show More
- Injector.XF
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Syscall Use |
Show More
|
| Process Manipulation Evasion |
|
| Process Shell Execute |
|
| Anti Debug |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\10c9e6360e00576909c8e78e485b5da0aec24e00_0000253440.,LiQMAxHB
|