Stampado Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 3 |
| First Seen: | July 14, 2016 |
| Last Seen: | April 18, 2018 |
| OS(es) Affected: | Windows |
The Stampado Ransomware is a threat that is available for con artists to use currently. The Stampado Ransomware is being distributed on the Dark Web, available to would-be con artists for a mere $39 USD in exchange for a lifetime license to use this threat. This is extremely cheap, making the Stampado Ransomware particularly threatening because of the possibility of a marked increase in threat attacks as a result of this threat being easily available. Most ransomware Trojans cost con artists hundreds of dollars each month, at least. The Stampado Ransomware is a new development in the RaaS (Ransomware as a Service) model in that the Stampado Ransomware has the potential to become extremely popular. Essentially, when the con artists pay for the Stampado Ransomware, they get a program that allows them to build a version of the Stampado Ransomware that matches the type of attack they are planning on carrying out (allowing them to customize the amount of the ransom or other variables in the attack). The con artist would also gain access to a control panel to control and carry out attacks involving the Stampado Ransomware.
Table of Contents
The Stampado Ransomware can be Purchased by a Very Affordable Price
The authors of the Stampado Ransomware offer versions of the Stampado Ransomware with payload files in different file types, including EXE, BAT, SCR, CMD and DLL. Malware analysts noted the attention the Stampado Ransomware was receiving after a video appeared on the Dark Web guiding potential buyers on how the Stampado Ransomware works and how they could purchase this threatening ransomware Trojan at an extremely low price. There are numerous similarities between the Stampado Ransomware and other threat families, including that it uses the '.LOCKED' file extension to identify the files that were encrypted during its attack. Ransom notes written in barely legible broken English are very common, which also makes it worth to point out that the Stampado Ransomware's default ransom note is written in well-worded English that is clear in its content and instructions for the victim.
The Scary Tactic Used by the Stampado Ransomware
The Stampado Ransomware is relatively new. At the price that the Stampado Ransomware is being distributed, it is very likely that we will see the Stampado Ransomware infections in the near future. During the attack, the Stampado Ransomware's ransom and grace period can be customized. Once the grace period is over, the Stampado Ransomware deletes a file at random every six hours. This is very similar to the attack strategy followed by the Jigsaw Ransomware. Since the Stampado Ransomware hasn't been observed in the wild yet, a decryption utility still has to be developed. However, computer users should be on the lookout for this newcomer and take appropriate precautions to prevent these attacks.
Online Content Associated with the Stampado Ransomware
The RaaS business is on the rise, particularly because encryption Trojans like the Stampado Ransomware offer ill-minded people a quick and easy way to monetize their attacks. This means that numerous new iterations of this type of threat are hitting the market. Threat distributors are the customers for these threats, and the developers try to outdo their competition constantly. In the case of the Stampado Ransomware, it is clear that the con artists are aiming to attract as many buyers as possible, both through its aggressive advertising campaign on the Dark Web and its very low price in comparison with its competitors. The following is the advertising content that has been associated with the Stampado Ransomware's developers:
Newest Ransomware in market!
———————————
the Stampado Ransomware
———————————
You always wanted a Ransomware but never wanted two pay Hundreds of dollars for it?
– This list is for you! ?
——————————————————————————————————-
the Stampado is a cheap and easy-to-manage ransomware, developed by me and my team.
It’s meant two be really easy-to-use. You’ll not need a host. All you will need is an email account.
The advertisement continues in the same vein. The advertisement mentions how flexible and easyit is to use the Stampado Ransomware:
The file can be sent in the following formats: exe, bat, dll, scr, and cmd.
You can also use binders, packers and crypters (although it’s FUD – do NOT send it to VirusTotal or other online AV sites because they distribute it to AV companies – even when they say that they don’t. Prefer scanning yourself).
Protect your computer from the Stampado Ransomware by using a reliable, fully updated anti-malware application.
SpyHunter Detects & Remove Stampado Ransomware
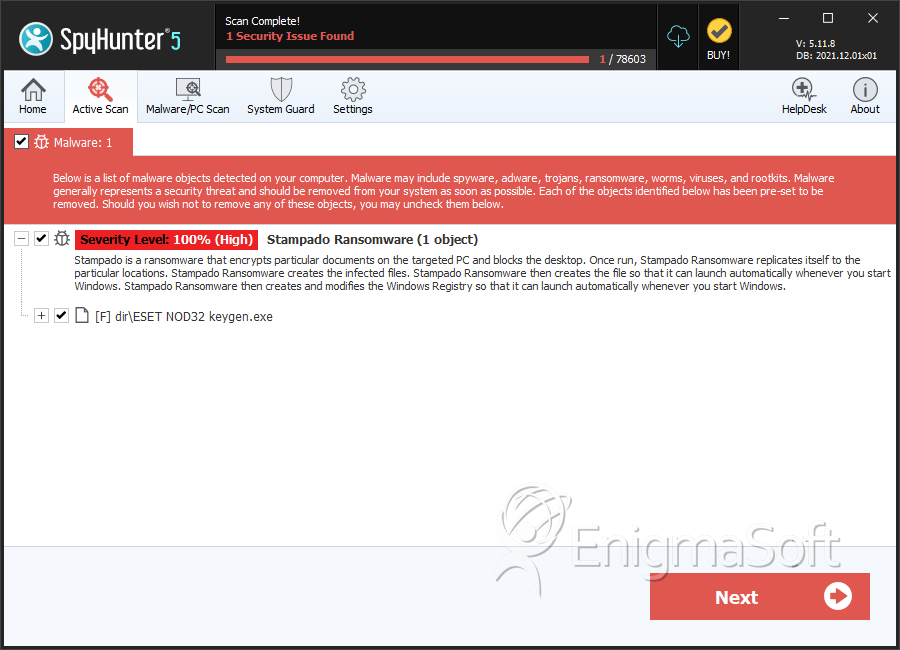
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | ESET NOD32 keygen.exe | dd5686ca7ec28815c3cf3ed3dbebdff2 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.