ShadowPad
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 60 % (Medium) |
| Infected Computers: | 324 |
| First Seen: | August 17, 2017 |
| Last Seen: | April 21, 2023 |
| OS(es) Affected: | Windows |
 The ShadowPad program is a particular piece of malware that managed to remain undetected in supply-chain networks and enable threat actors to have backdoor access to the compromised systems. The ShadowPad program was discovered in July 2017. The investigation into the ShadowPad cyber began with questionable DNS (Domain Name Server) requests that were reported to computer security authorities. The researchers were led to an unlikely culprit — a legitimate server management kit utilized by financial institutions, education organizations, telecom companies, factories, energy distributors and transportation firms.
The ShadowPad program is a particular piece of malware that managed to remain undetected in supply-chain networks and enable threat actors to have backdoor access to the compromised systems. The ShadowPad program was discovered in July 2017. The investigation into the ShadowPad cyber began with questionable DNS (Domain Name Server) requests that were reported to computer security authorities. The researchers were led to an unlikely culprit — a legitimate server management kit utilized by financial institutions, education organizations, telecom companies, factories, energy distributors and transportation firms.
Table of Contents
ShadowPad’s association with threat actors seeking data
A closer look at the server management kit revealed that a recent update through the official update channels added a new module to the software. The new module was responsible for the questionable DNS requests mentioned above. The corrupted server management kit was confirmed to come from the official developer and have a valid digital signature. Moreover, the new module was configured to contact a particular set of domains every 8 hours. The domains proved to be 'Command and Control' servers. The ShadowPad program reported general computer information like active username, IP address, associated domain, hostname and software configuration. A network-wide search showed that not all infected computers receive a response from the command servers. It is suspected that the threat actors go over the received DNS requests and target specific PCs that may have valuable data manually.
The Winnti Group and backdoor malware, the known threat actor with Chinese origins that develops and uses ShadowPad, kept updating it throughout 2019. A recent report by researchers working with ESET outlines the major new features added to ShadowPad.
ShadowPad does not obtain its C&C server address and protocol the way most other malware does. Instead, it parses information from publicly available pages, hosted by various legitimate services, including Valve's Steam profile pages, GitHub repos, even Google Docs files. It has been doing that for a while, but researchers discovered that there were newly timestamped modules, compiled in 2019, that use additional obfuscation and random module identifiers. The ShadowPad backdoor also uses a specific campaign identifier that is located in its configuration.
ShadowPad activities evolve to take aggressive destructive path
The actions of ShadowPad have evolved and the latest destructive actions take place in a series of steps, which are outlined in the Figure 1 infographic below. Sourced from the Eset Security website welivesecurity.com, the infographic represents the methods that threats out of the Winnti conduct for their infection and destruction on systems. Within the attack methods, one would take notice to the family of Winnti threats compromising many different entities and then ending up with a variation of ShadowPad and other threats, such as ShadowHammer.
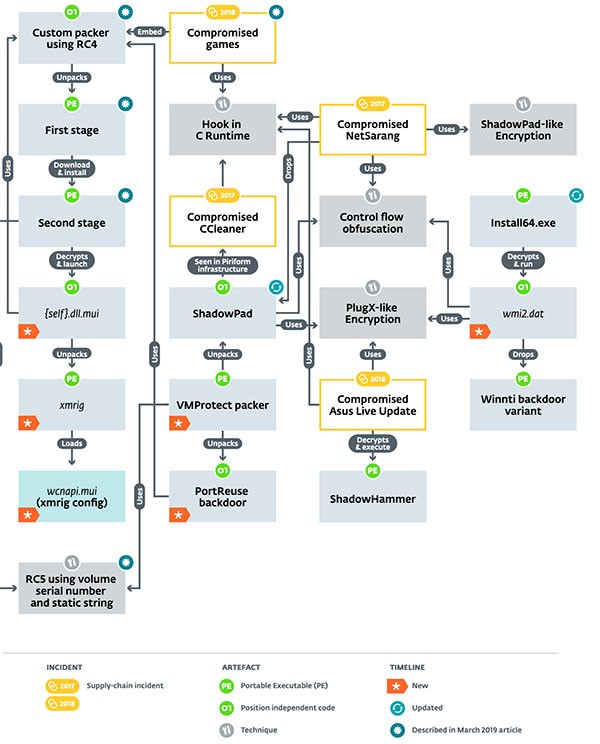
ShadowPad's configuration module contains a pool of encrypted strings that represent two separate URLs of publicly available pages on legitimate services, such as the aforementioned Google Docs or Steam profile pages. Those pages contain the real C&C server URL that the module decrypts. The campaign identifier string is also contained in the same pool. A lot of the publicly available documents have been taken down by the bad actors but a number of decrypted C&C server IPs have been recovered by researchers using Google Docs' document history feature.
A response from the command server was recorded shortly after the investigation into the ShadowPad started. The threat actors deployed a full-featured Backdoor Trojan that achieved persistence by writing a Registry key. That way the ShadowPad Backdoor Trojan managed to load with Windows and enable remote desktop access. The attackers were able to download more unsafe tools and install ransomware given the nature of the compromised systems. Fortunately, the ShadowPad malware would go down in cyber history as a missed opportunity since AV manufacturers managed to block its spread on time. The ShadowPad project may be revised on a later date and transformed into a new cyber-threat. You may want to check your PC for opened ports, poorly configured remote desktop accounts and questionable DNS requests using a trusted anti-malware suite.
SpyHunter Detects & Remove ShadowPad
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 0009f4b9972660eeb23ff3a9dccd8d86 | 5 |
| 2. | file.dll | 97363d50a279492fda14cbab53429e75 | 0 |
| 3. | file.dll | dac6dd4943f23b325e361552c0b8b77a | 0 |
| 4. | file.dll | 82e237ac99904def288d3a607aa20c2b | 0 |
| 5. | file.dll | 22593db8c877362beb12396cfef693be | 0 |

