ShadowHammer
 ShadowHammer is a name that cybersecurity companies associate with a major security compromise of the update channels used by the hardware and software manufacturers at ASUS. Several leading computer security vendors alerted of the ShadowHammer campaign towards the end of March 2019, and a dedicated security patch was issued by ASUS shortly after that. Computer security researchers noticed questionable 'critical system updates' pushed through the legitimate update servers utilized by ASUS. The threatening updates included a valid digital certificate issued to developers at ASUS and instructions on which systems the update should be installed.
ShadowHammer is a name that cybersecurity companies associate with a major security compromise of the update channels used by the hardware and software manufacturers at ASUS. Several leading computer security vendors alerted of the ShadowHammer campaign towards the end of March 2019, and a dedicated security patch was issued by ASUS shortly after that. Computer security researchers noticed questionable 'critical system updates' pushed through the legitimate update servers utilized by ASUS. The threatening updates included a valid digital certificate issued to developers at ASUS and instructions on which systems the update should be installed.
The threat actors behind the ShadowHammer campaign may have gained access to the legitimate update servers via a software exploit and compromised remote desktop accounts. However, elevated access was needed to apply the legitimate digital certificate, and it is possible that someone in the higher-ranks at ASUS may have been the victim of a spear-phishing attack. A compromised top-level account can explain how the corrupted ASUS update managed to slip by security scanners and arrive on targeted computers. The threat actors operating the ShadowHammer malware used lists with targeted MAC (Media Access Control address is an address associated with a network adapter) address as a way to infect users selectively. That way, the ShadowHammer actors managed to send infected data packets to computers regardless if they are connected to an extensive home network.
ShadowHammer's method of exploitation and attack has many steps
ShadowHammer comes from a lineage of the Winnti group of threat actors, known for their infiltration of systems to compromise data via the Winnti family of backdoor malware. Exploiting certain aspects of compromised computers, ShadowHammer may in-turn first go through many processes to exploit data. Such a process is outlined in the Figure 1 image below from the Eset security company and their website welivesecurity.com. The chart outlines the several steps the Winnti group takes to eventually end up with a variation of ShadowHammer or its associated threats such as ShadowPad.
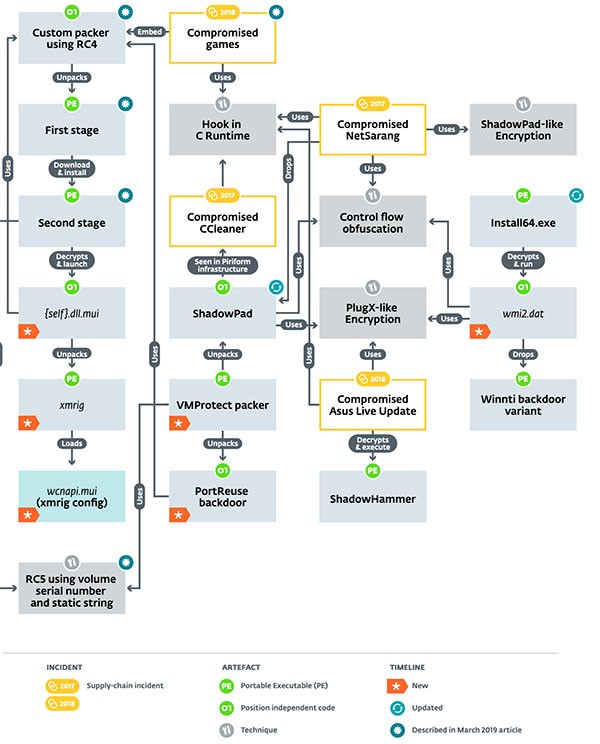
Security reports suggest that the ShadowHammer malware landed on at least sixty thousand devices that have utilities by ASUS installed. A sophisticated attack like this one is suspected of being funded by a nation-state, and we may be facing a significant cyber-espionage effort. The ShadowHammer malware may grant top-tier access to devices and install a backdoor. ShadowHammer may be used to collect saved credit card information in your Web browser, extract files, and export your emails to a remote server. ASUS released a special tool to detect the compromised updates linked to ShadowHammer that you can download from https://dlcdnets.asus.com/pub/ASUS/nb/Apps_for_Win10/ASUSDiagnosticTool/ASDT_v1.0.1.0.zip. You might want to run a complete system scan using a respected anti-malware solution and terminate the files that may be used by ShadowHammer.

