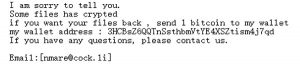
Satan Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 3 |
| First Seen: | January 19, 2017 |
| Last Seen: | July 23, 2019 |
| OS(es) Affected: | Windows |
The Satan Ransomware is a RaaS, or Ransomware as a Service, that is being used to infect computer users. According to the Satan Ransomware's own creators, the following is an accurate description of what the Satan Ransomware does and the service they provide to other con artists:
'What is the Satan?
Apart from the mythological creature, the Satan is a ransomware, a malicious software that once opened in a Windows system, encrypts all the files, and demands a ransom for the decryption tools.
How to make money with the Satan?
First of all, you'll need to sign up. Once you've sign up, you'll have to log in to your account, create a new virus and download it. Once you've downloaded your newly created virus, you're ready to start infecting people.
Now, the most important part: the bitcoin paid by the victim will be credited to your account. We will keep a 30% fee of the income, so, if you specified a 1 BTC ransom, you will get 0.7 BTC and we will get 0.3 BTC. The fee will become lower depending on the number of infections and payments you have.'
Table of Contents
Instead of Your Soul this Ransomware Wants Your Money
Anyone can register for an account and create a customized variant of the Satan Ransomware, which makes this threat particularly threatening. It is up to each user to decide how to spread their newly created Satan Ransomware variant. Common methods include using botnets to send out massive amounts of infected spam email messages, as well as hacking certain Web pages so that they will infect the visitors' computers. Other methods that could be used to distribute the Satan Ransomware include disguising the Satan Ransomware as a popular file download on file sharing networks and using corrupted advertisements to trick computer users into downloading this threat.
How the Satan Ransomware Attack Works
Once a con artist has created a customized version of the Satan Ransomware, they can make certain changes, such as changing the ransom amount and configuring the Satan Ransomware so that the ransom amount will increase over a certain amount of dates. However, it does not seem that the creators of the Satan Ransomware give their clients many customization options, at least when compared to other known RaaS services.
One of the most threatening aspects of the Satan Ransomware, however, is that it includes a page on Droppers, which provides resources to assist clients in creating corrupted installers and files that abuse macros on Microsoft Word, which can then be distributed using a variety of methods. This help with distribution has not been observed before with other RaaS providers, making it possible that the Satan Ransomware may attract more active users and result in a higher amount of infections. Apart from the page on Droppers, the Satan Ransomware also includes a Translate page that allows con artists to create ransom notes for their Satan Ransomware variant in numerous different languages.
A Brief Analyze of the Satan Ransomware Infection Itself
The Satan Ransomware Trojan itself is a fairly typical ransomware threat that runs on the infected computer's memory, injecting itself into other running processes. During its attack, the Satan Ransomware will encrypt the following file types:
.incpas, .mp4, .pab, .st6, .sas7bdat, .wmv, .backup, .drf, .ibank, .3ds, .odg, .cer, .tif, .cs, .dotx, .7z, .png, .bak, .ibz, .db3, .pbl, .3fr, .dxf, .nk2, .bkp, .mdf, .svg, .xlm, .3dm, .pct, .java, .pot, .sxi, .ibd, .sxw, .pspimage, .ppt, .kbx, .ppsm, .ndd, .txt, .pdb, .say, .backupdb, .fla, .swf, .asx, .accdt, .mp3, .ycbcra, .erf, .cr2, .pfx, .potx, .qby, .sqlite, .blend, .class, .pat, .odp, .gray, .qbw, .tib, .thm, .htm, .mos, .rm, .key, .std, .tlg, .lua, .pst, .sqlitedb, .grey, .cdr4, .dc2, .ce1, .ps, .tex, .eml, .xlam, .pages, .st8, .jar, .st7, .potm, .sdf, .db-journal, .pcd, .aspx, .rwl, .kpdx, .fmb, .xlr, .gry, .kc2, .oil, .moneywell, .xlk, .sti, .accdr, .oth, .c, .xml, .nd, .mdb, .pem, .erbsql, .bpw, .ffd, .ost, .pptm, .dwg, .zip, .qbm, .cdx, .des, .dng, .pdd, .cfp, .nyf, .cgm, .sldm, .xla, .odf, .raf, .crw, .mef, .raw, .x11, .nsd, .fff, .design, .dcs, .ptx, .al, .ns2, .bik, .back, .accdb, .nwb, .cpi, .ads, .odt, .sqlite3, .docm, .drw, .pl, .nx2, .fpx, .rdb, .otp, .msg, .accde, .agdl, .php, .csv, .py, .rtf, .ach, .sda, .ddd, .asf, .dotm, .cmt, .h, .hbk, .xlsx, .s3db, .tga, .wav, .iif, .dxb, .sql, .db, .sd0, .bgt, .djvu, .jpg, .doc, .craw, .mpg, .sxd, .kdc, .jpeg, .psafe3, .flac, .dtd, .act, .qba, .vob, .cdrw, .eps, .bkf, .mdc, .rar, .mov, .cdf, .m4v, .ab4, .bank, .pps, .cib, .dot, .dgc, .exf, .flv, .xlsb, .ddrw, .adb, .srw, .plc, .csh, .xls, .fxg, .otg, .pas, .xlt, .indd, .rwz, .xltx, .apj, .stw, .xltm, .orf, .ott, .qbb, .max, .cls, .obj, .docx, .dcr, .cdr3, .qbx, .pdf, .nef, .ots, .srt, .ddoc, .rat, .phtml, .m, .dbx, .nxl, .avi, .p12, .awg, .dbf, .ns3, .mmw, .prf, .wallet, .rw2, .jin, .odc, .qbr, .ppsx, .ns4, .wpd, .wps, .nsh, .dxg, .fhd, .dac, .wb2, .nrw, .odb, .ait, .jpe, .odm, .sldx, .fdb, .acr, .war, .oab, .sxc, .cpp, .r3d, .hpp, .asm, .st5, .stx, .xis, .dds, .xlsm, .p7c, .cdr5, .3g2, .mrw, .sr2, .html, .cdr, .idx, .st4, .bdb, .kdbx, .nsg, .der, .ods, .myd, .nop, .ppam, .pptx, .yuv, .xlw, .mfw, .nsf, .csl, .php5, .p7b, .crt, .asp, .srf, .jsp, .cdr6, .sxm, .iiq, .3gp, .ce2, .arw, .bay, .ai, .sxg, .psd, .3pr, .fh, .pef .x3f, .sik, .bpp, .vmdk, .spi, .bup, .cvt, .bb, .fkc, .tjl, .dbk, .swp, .fb, .vib, .dtb, .bke, .old, .bkc, .jou, .rpb, .abk, .sav, .bkn, .tbk, .fbw, .vrb, .spf, .bk, .sbk, .umb, .ac, .vbk, .wbk, .mbk.
The encrypted files will have their names scrambled and will be identified with the extension '.stn'. The Satan Ransomware delivers its ransom note in the form of an HTML file named 'HELP_DECRYPT_FILES.html,' which is dropped in each directory where the files were encrypted.
SpyHunter Detects & Remove Satan Ransomware
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 860b29dda2616be5e14abb7936dcc2a2 | 1 |
| 2. | file.exe | e877d12971849fcdceac4f98bcad4a56 | 1 |
| 3. | file.exe | 24ba6c990e9bfad87e7ecc61f8462f92 | 0 |
| 4. | file.exe | ba6a6c2f68edf77e55d6a529c0eaa99e | 0 |