Lucky (Satan) Ransomware
 The Lucky Ransomware is a cryptovirus that primarily attacks Linux and Windows servers aiming to encrypt its victims’ access to their data and demands a whopping 1 BTC in exchange for a decryption key. The encryption process affects a multitude of file types, leaving system files aside.
The Lucky Ransomware is a cryptovirus that primarily attacks Linux and Windows servers aiming to encrypt its victims’ access to their data and demands a whopping 1 BTC in exchange for a decryption key. The encryption process affects a multitude of file types, leaving system files aside.
Security researchers first detected Lucky in November 2018, shortly after it had started attacking some companies' servers in the financial sector. Ransomware threats typically use encryption algorithms to make victims' files inaccessible so that they can demand a ransom payment in exchange for renewed access to the affected data. A thorough analysis of Lucky’s code has revealed striking similarities (including a shared C&C server) to a previously detected ransomware known as Satan. Though the latter has since evolved, Lucky is still all about blackmailing, mining, and everything in between. The latest recorded Lucky ransomware infections have all combined encryption with currency mining.
Table of Contents
A Variant of Satan Ransomware
The main functions Lucky Ransomware sets out to perform every time it strikes a target are file encryption, propagation, and mining. First, Lucky applies an AES algorithm to get a grip on its victims' files. Second, it exploits a slew of well-known server-side vulnerabilities to propagate itself. Finally, the malware utilizes Satan's proprietary coin mining pool address to store the digital currency it has mined during encryption. Lucky's overall architecture is a very close match of Satan’s. It includes several components, like a tiny file named "fast.exe/ft32" that pre-loads the propagation and all cryptographic modules. Then, the malware deploys an encryption module named "cpt.exe/cry32" which encrypts the files, while a propagation module "conn.exe/conn32" spreads the malware after exploiting the corresponding system vulnerabilities. Finally, a mining module named "mn32.exe/mn32 establishes a connection to the mine pool address, and a service module called "srv.exe" makes for smooth task execution by creating a dedicated Windows or Linux background service.
Multimodal Distribution Techniques
Ever since the first reported instances of Lucky ransomware infections in China and Japan came to light, the crooks associated with Lucky have set their eyes on increasing the number of potential victims. In addition to relying on conventional infection vectors such as spam and malvertising, the Lucky Ransomware has also taken advantage of unprotected RDP connections. It has also often found itself bundled with all sorts of software or disguised as fake updates.
Besides the infection paths mentioned above, Lucky has found quite a few ways to reach a targeted system. On the one hand, it has a worm-like design that allows it to spread on its own and without any human interaction. On the other hand, Lucky has reportedly taken advantage of many officially discovered security vulnerabilities, including, but not limited to:
- JBoss deserialization vulnerability (CVE-2013-4810,CVE-2017-12149)
- JBoss default configuration vulnerability (CVE-2010-0738)
- Spring Data Commons remote code execution vulnerability (CVE-2018-1273)
- Windows SMB remote code execution vulnerability (MS17-010)
- Tomcat arbitrary file upload vulnerability (CVE-2017-12615)
- Tomcat web admin console backstage weak password brute-force attack
- WebLogic arbitrary file upload vulnerability (CVE-2018-2894)
- WebLogic WLS component vulnerability (CVE-2017-10271)
- Apache Struts 2 remote code execution vulnerability (S2-045)
- Apache Struts 2 remote code execution vulnerability (S2-057)
Overall, the Lucky Ransomware imposes a reasonably high risk of infection because all of these vulnerabilities are easy to exploit, and actual exploit kits are publicly available on the Internet. As a result, threat actors are free to attack vulnerable systems without actually having to customize the malware script at all. Organizations that have yet to patch their systems are at a greater risk now, as some of the exploited vulnerabilities showed up on the Web several months ago.
User-generated Files Are the Main Target for Encryption
In order to encrypt files, the malware traverses the folder and finds the targeted files through their specific extensions. The ransomware skips system files as they are needed for the normal functioning of the infected machine, while files targeted for encryption by Lucky include all kinds of user-generated files like numerous media file types, documents, databases and others:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
Once encryption has completed, all of the victims’ files are renamed with one of the following patterns:
- [email_ransom][original_file].[random_characters].lucky(most Lucky infections)
- [email_ransom][original_file].[random_characters].nmare(December 2018 infections)
- [email_ransom][original_file].[random_characters].evopro(all China-based infections)
The Ransom Note
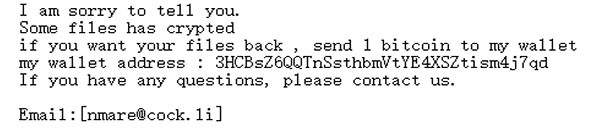
Malware actors indulging in ransomware attacks feel entitled to demand a ransom payment from their victims, and those associated with Lucky make no exception, either. Once encryption has completed, Lucky draws up a text file named "_How_To_Decrypt_My_File_.txt" and places it on the user’s desktop. The note is quite succinct and reads as follows:
'I am sorry to tell you.
Some files has crypted
if you want your files back , send 1 bitcoin to my wallet
my wallet address : 3HCBsZ6QQTnSsthbmVtYE4XSZtism4j7qd
If you have any questions, please contact us.
Email:[nmare@cock.li]'
In addition to the ransom note on the desktop, Lucky creates two more files — fast(dot)exe and random(dot)exe — in the User and Temp folders, respectively.The Lucky Ransomware's ransom note should be ignored, and paying any ransom associated with threats like the Lucky Ransomware should be avoided!
Protecting Your Data from Threats Like the Lucky Ransomware
The best protection against threats like the Lucky Ransomware is to have backup copies of your files, both on external hard drives and in a cloud-based environment. Moreover, you should have a robust security program with real-time protection features. While such a piece of software will not wave a magic wand to undo an already completed encryption process, it will prevent the Lucky Ransomware from infecting your machine in the first place. Since ransomware attacks often take advantage of poorly protected networks and out-of-date software and operating systems, keeping the latter up-to-date should always be a matter of the utmost importance.

