RansomWarrior 1.0 Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 7 |
| First Seen: | August 12, 2018 |
| Last Seen: | February 5, 2019 |
| OS(es) Affected: | Windows |
The RansomWarrior 1.0 Ransomware is an encryption ransomware Trojan first observed on August 8, 2018. The RansomWarrior 1.0 Ransomware is most likely being developed by a group of hackers located in India and carries out a typical variant of an encryption ransomware Trojan attack. The RansomWarrior 1.0 Ransomware takes the victims' files hostage and then demands a ransom payment from the victim to retrieve access to the compromised files.
Table of Contents
The Warrior against Your Files
The RansomWarrior 1.0 uses the AES 256 encryption to make the victim's files inaccessible. The RansomWarrior 1.0 Ransomware marks the files encrypted by the attack by adding the file extension '.THBEC' to each file's name. The RansomWarrior 1.0 Ransomware is delivered to the victim's computer using spam email attachments. Once installed, the RansomWarrior 1.0 Ransomware encrypts the user-generated files, which may include files with the following file extensions:
.ebd, .jbc, .pst, .ost, .tib, .tbk, .bak, .bac, .abk, .as4, .asd, .ashbak, .backup, .bck, .bdb, .bk1, .bkc, .bkf, .bkp, .boe, .bpa, .bpd, .bup, .cmb, .fbf, .fbw, .fh, .ful, .gho, .ipd, .nb7, .nba, .nbd, .nbf, .nbi, .nbu, .nco, .oeb, .old, .qic, .sn1, .sn2, .sna, .spi, .stg, .uci, .win, .xbk, .iso, .htm, .html, .mht, .p7, .p7c, .pem, .sgn, .sec, .cer, .csr, .djvu, .der, .stl, .crt, .p7b, .pfx, .fb, .fb2, .tif, .tiff, .pdf, .doc, .docx, .docm, .rtf, .xls, .xlsx, .xlsm, .ppt, .pptx, .ppsx, .txt, .cdr, .jpe, .jpg, .jpeg, .png, .bmp, .jiff, .jpf, .ply, .pov, .raw, .cf, .cfn, .tbn, .xcf, .xof, .key, .eml, .tbb, .dwf, .egg, .fc2, .fcz, .fg, .fp3, .pab, .oab, .psd, .psb, .pcx, .dwg, .dws, .dxe, .zip, .zipx, .7z, .rar, .rev, .afp, .bfa, .bpk, .bsk, .enc, .rzk, .rzx, .sef, .shy, .snk, .accdb, .ldf, .accdc, .adp, .dbc, .dbx, .dbf, .dbt, .dxl, .edb, .eql, .mdb, .mxl, .mdf, .sql, .sqlite, .sqlite3, .sqlitedb, .kdb, .kdbx, .1cd, .dt, .erf, .lgp, .md, .epf, .efb, .eis, .efn, .emd, .emr, .end, .eog, .erb, .ebn, .ebb, .prefab, .jif, .wor, .csv, .msg, .msf, .kwm, .pwm, .ai, .eps, .abd, .repx, .oxps, .dot.
The RansomWarrior 1.0 Ransomware delivers a lengthy ransom note in the form of a program window containing the following message:
'Oops!!! Your Files Has Been Encrypted By RansomWarrior 1.0
Message for you from RansomWarrior 1.0 Hello, we are a group of dedicated hackers from India. We have encrypted all your files so we can get your money. All your important files has been encrypted which means you are going to pay us a ransom of 349 USD in Bitcoins. So first of all you can decrypt to of your important files and we will show you which files has been decrypted. Just so you can see that we do have your decryption key, and you will be able to buy it from us. You won't be able to get your important files back if you don't buy your decryption key. Notice a clock on the side, when that date arrives your important files will be deleted(You have 24 hours to pay the ransom).
You will be able to get Bitcoins, at sites such as coinbase.com or localbitcoins.com. There are also others, but usually these are the usual choice (Make sure to get a little bit more Bitcoins, due to transaction fees and the crypto currency is very volatile. Its also a good idea to get the Bitcoins, as soon as possible, because sometimes the purchasing process can take hours. You would also need a wallet for your Bitcoins if you are not using the coinbase.com wallet. When you have your Bitcoins in your wallet. You are going to download and install the for browser. Go to torproject.org and then follow the instructions given there.
You need the for browser, because our payment website is located in darknet. When you have downloaded and installed the for browser. Go to this link: zpkjjp57apz76k3q[.]onion\Pay\PayThis\Payment_1000731.PHP When you are on the website, you simply transfer your Bitcoins to the address that are provided to you(You can copy the address and then paste it in your Bitcoin wallet when you are transfering the Bitcoins). When your Bitcoins arrive to our wallet, you will be notified and then be able to download the decryption key. When you have your decryption key, simply place the key in your C:\ And then get all your important files back. The ransomware will then decrypt everything and remove itself.
Here is the entire lists of the way it's done:
1. Decrypt 2 important files as proof of decryption key and we decrypt to keep a good reputation about RansomWarrior 1.0.
2. Get a Bitcoin wallet(If needed)
3. Get the Bitcoins from coinbase[.]com or localbitcoins[.]com or an alternative.
4. Download and install the for browser from torproject.org
5. Go to our website: zpkjjp57apz76k3q[.]onion\Pay\PayThis\Payment_1000731.PHP
6. Pay your Bitcoins to the Bitcoin address showed.
7. When accepted download your decryption key and put it in your C:\.
8. Then decrypt all of your important files and wait till the ransomware deletes itself.'
Protecting Your Data from the RansomWarrior 1.0 Ransomw
The best protection against threats like the RansomWarrior 1.0 Ransomware is to have file backups. Apart from file backups, you should have a reliable security program to prevent the RansomWarrior 1.0 Ransomware from being installed. File backups and security software can help prevent the worst consequences of threats like the RansomWarrior 1.0 Ransomware.
SpyHunter Detects & Remove RansomWarrior 1.0 Ransomware
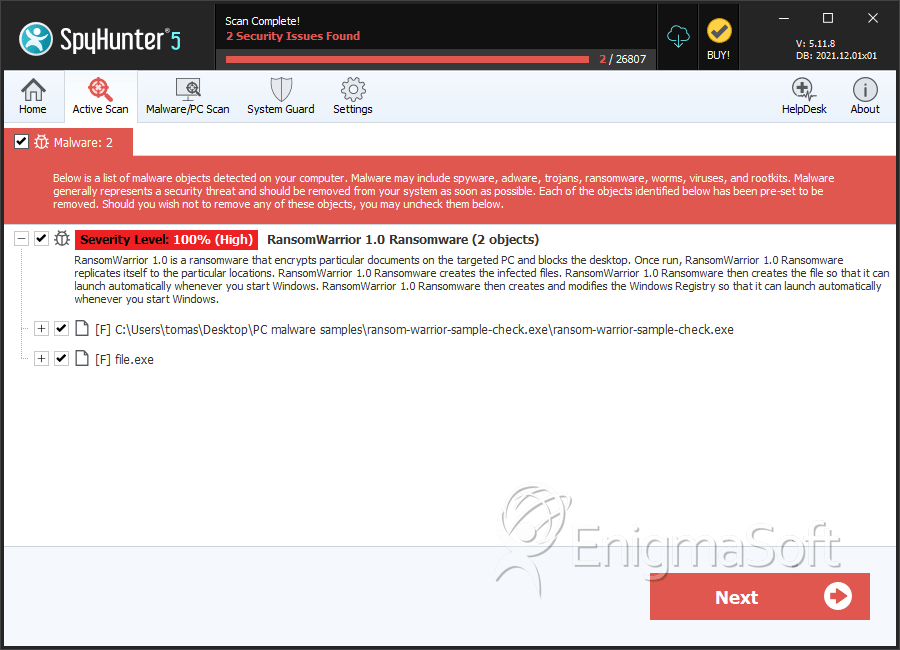
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | ransom-warrior-sample-check.exe | d7d38fe6f2e94f0d0210a9e15ef45e4e | 6 |
| 2. | file.exe | 36f130c8abbd25c056b3ee1d1605a6ba | 0 |

