PyCL Ransomware
Computer users have reported their files becoming inaccessible, and a suspicious message being displayed on their computers. This message reads as follows:
'Your Personal Files Are Encrypted
Your documents, photos, databases and other important files have been encrypted with strongest encryption and unique key, generated for this computer. Private decryption key is stored on a secret Internet server and nobody can decrypt your files until you pay and obtain the private key.
1. Pay amount BTC (about of USD) to address:
2. Transaction will take about 15-30 minutes to confirm.
Decryption will start automatically. Do not: power off computer, run antivirus program, disable internet connection. Failures during key recovery and file decryption may lead to accidental damage on files.
Your files will be lost without payment through:'
This message and the inability to access the files on the infected computer indicate that the PyCL Ransomware has entered the victim's computer. The PyCL Ransomware is being distributed using the RIG Exploit Kit. This recent PyCL Ransomware attack may not be a full-fledged threat campaign, but it may just have been designed to test how to distribute this threat to potential victims. Factors that indicate this include the fact that the threat is not being deployed in its full version, and in the manner in which it is being distributed.
Table of Contents
The PyCL Ransomware may be Delivered to Your PC by an EK
PC security researchers are referring to the PyCL Ransomware using this name because the PyCL Ransomware is programmed using Python and is delivered in a script with the file name 'cl.py' to the victims' computers. EITest seems to be used to deliver the PyCL Ransomware to victims through the use of exploits associated with the RIG Exploit Kit. Apparently, con artists have hacked into these websites to redirect computer users to ransomware infections. The PyCL Ransomware was being distributed along with another known ransomware Trojan, named Cerber. However, the PyCL Ransomware distribution was only carried out for one day, indicating that this may be part of a test run. Like other ransomware Trojans, the PyCL Ransomware is designed to encrypt the victims' files and then asks for the payment of a ransom from the victim.
How the PyCL Ransomware Carries out Its Attack
One of the files used in the PyCL Ransomware attack is named 'user.txt,' including the string 'xkwctmmh.' The string is included in every request to the PyCL Ransomware's Command and Control server. It seems likely that the PyCL Ransomware is part of the testing for a RaaS (Ransomware as a Service) platform that is not fully finished yet. These are services that allow con artists to lease the use of a ransomware Trojan, handling all distribution aspects of the infection. It seems that this user name, the string identified in the attack, is meant as the placeholder for the affiliate using the PyCL Ransomware. The PyCL Ransomware is distributed as an NSIS installer that includes the PyCL Ransomware files and a tutorial explaining how to pay the ransom to recover the affected files. The PyCL Ransomware connects to its Command and Control server constantly, providing status and debugging information, which also is an indicator of a ransomware Trojan in development. The PyCL Ransomware uses a strong encryption engine to make the victim's files completely inaccessible, but the current state of the attack seems to vary, as it is apparent that the PyCL Ransomware has not been released in its full form.
The PyCL Ransomware Attack in Its Current State
The PyCL Ransomware displays a four-day timer and the ransom note. The PyCL Ransomware displays a ransom note from its Command and Control server and decrypts the victim's files automatically if a ransom payment is carried out. However, the PyCL Ransomware in its current state does not delete the original files after the encryption, meaning that victims of the PyCL Ransomware attack do not need to fear that they will lose their data currently.
SpyHunter Detects & Remove PyCL Ransomware
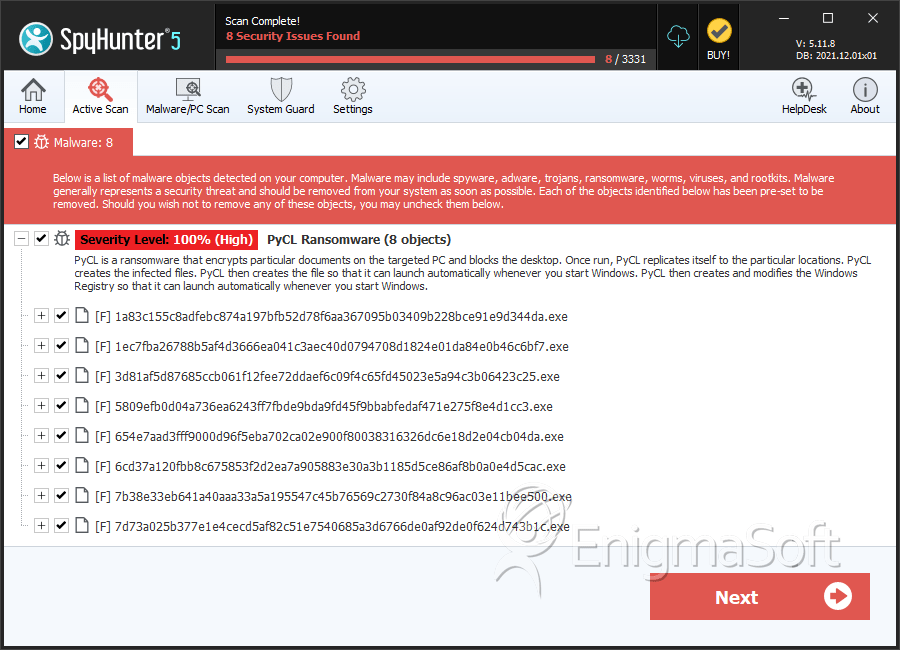
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 1a83c155c8adfebc874a197bfb52d78f6aa367095b03409b228bce91e9d344da.exe | 01cc60cef0b287d5ae2a2f0b7719a14a | 0 |
| 2. | 1ec7fba26788b5af4d3666ea041c3aec40d0794708d1824e01da84e0b46c6bf7.exe | 8b8fcd6595eff3b6f135775dc3b06331 | 0 |
| 3. | 3d81af5d87685ccb061f12fee72ddaef6c09f4c65fd45023e5a94c3b06423c25.exe | cc3f19a561c66f9fc85700de69f7d084 | 0 |
| 4. | 5809efb0d04a736ea6243ff7fbde9bda9fd45f9bbabfedaf471e275f8e4d1cc3.exe | 13ad144fe1b79bd3d87f5baa3e016ec5 | 0 |
| 5. | 654e7aad3fff9000d96f5eba702ca02e900f80038316326dc6e18d2e04cb04da.exe | c2a4224455de94a9e90966d8725fdf61 | 0 |
| 6. | 6cd37a120fbb8c675853f2d2ea7a905883e30a3b1185d5ce86af8b0a0e4d5cac.exe | 9970db10dfd35bf4df2e999d5d63a4c7 | 0 |
| 7. | 7b38e33eb641a40aaa33a5a195547c45b76569c2730f84a8c96ac03e11bee500.exe | d79b9f680c9ac58c7bc2e821048ac632 | 0 |
| 8. | 7d73a025b377e1e4cecd5af82c51e7540685a3d6766de0af92de0f624d743b1c.exe | 8e82cfea40df9deb97b9a001f75244bf | 0 |
| 9. | 80d402f38ff9849ea5e9f8a126e00f423ca1b4f1121c8059aebed8336bfc6f30.exe | 0b71016ac598c45e8a2a219eba903ec8 | 0 |
| 10. | a0b1f5ab11a8250d7102bcab07f6dc770c0ca7cea9730028028dba0fbfad1210.exe | 2509eae5750dbdec6430aafb651d0c68 | 0 |
| 11. | b461fcc111346b09393bb7605d55ce93a45aa1b42277e16f12b600e235cd8162.exe | 73acf2f69d68b4be4baffa33b70ef62d | 0 |
| 12. | b66d636e3261a39642938ea13babb248116a9b909eb4855be5a1c805a45d3bf3.exe | 846eb8b919bfbd89274141dbc5c8cbd9 | 0 |
| 13. | d58eb7b4b78db2d11f2a4288245a448a923ce30ebb5894f63cce2743e865bc49.exe | 4e3aa8a35f0027bbecf6eb8f5f161b26 | 0 |
| 14. | e38098502de083f7a5dbb7aefdc5732259f7718e69c03f52a5e968bc29fbb73e.exe | 074b1d5e99a6873102aefac4e434ace5 | 0 |
| 15. | f241f35bb0f53a1baf0e5da26ef7bb86f3de83e94f3ccab04086b26f2f95dde5.exe | 2f03bf90f0b0ffbe9240782090aa9038 | 0 |
| 16. | f28abe9533f44db0487e79d78eb67ed70b1a62c8ddb6444567eff40abf83577a.exe | e4ce87a7829d11dc397d797fa675996c | 0 |
| 17. | f89cd790ea52c857918dde0fa634a8e1b780f28b381325174e2a9c2d64194892.exe | d911b8312d5d2eaf86c03856c7b657d7 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.