PowerWare Ransomware
The PowerWare Ransomware is a ransomware Trojan. One of the main issues about the PowerWare Ransomware that has attracted the attention of PC security researchers is that the PowerWare Ransomware operates in a manner that is fileless, making it more difficult to intercept and remove. The PowerWare Ransomware exploits PowerShell, the native framework for the Windows operating system. The people responsible for new ransomware threats have improved their ransomware creations gradually in the last few months to make them more effective. For example, the Petya Ransomware now overwrites the Master Boot Record to cause Blue Screens of Death on the victim's computer. The PowerWare Ransomware introduces infection methods that make it abnormally difficult to deal with this threat. As of the writing of this report, the PowerWare Ransomware is being used in targeted attacks against computers involved in the healthcare sector.
Table of Contents
The PowerWare that Sells a Harmful Product
The PowerWare Ransomware was first detected in late March of 2016 by PC security researchers at the Carbon Black security firm. The most enthralling and unique feature of the PowerWare Ransomware is that it does not require a file. Although many threat infections that are active today operate in a fileless manner, this is not a common feature in ransomware threats, making the PowerWare Ransomware fairly unique.
The PowerWare Ransomware is spread using corrupted email attachments. The PowerWare Ransomware infections may be the result of downloading an infected Word document file attachment that may be disguised as an invoice. The PowerWare Ransomware attack uses a trick that is fairly well-known. The PowerWare Ransomware attachment will display a message asking the computer user to enable macros to view the document correctly. When the macros are enabled, they run a cmd.exe, which will launch PowerShell that is a framework native to the Windows operating system used to perform tasks from a command line shell. Through the use of this method, the PowerWare Ransomware can operate without writing files to the infected computer's disk. This makes it particularly difficult for security software to detect or intercept the PowerWare Ransomware infection.
Understanding the PowerWare Ransomware Infection
Apart from this particularly unique infection method, the PowerWare Ransomware infection is fairly typical in that the PowerWare Ransomware still encrypts the victim's files to ask for a ransom payment in exchange for the decryption key. Many threat infections may use macros in Microsoft Word documents. These macros may be exploited to download additional binaries that may then be used to install other threats or create a backdoor to the victim's computer. In the case of the PowerWare Ransomware, no additional binaries or executable files are downloaded. Instead, the PowerWare Ransomware leverages PowerShell to carry out its attack. In this case, only a script is needed to carry out the attack, rather than an executable file.
How the PowerWare Ransomware Attack is Carried Out
Once the victim's files have been encrypted by the PowerWare Ransomware, it demands the payment of a $500 USD ransom to deliver the decryption key. Like many other ransomware threats, the PowerWare Ransomware claims that the amount will be doubled to $1000 USD if payment isn't carried out before a particular deadline. PC security researchers suspect that the PowerWare Ransomware is related to PowerSniff, an emerging family of ransomware Trojans that use fileless attacks to bypass many security applications. PC security researchers believe that it is highly likely that this approach to deliver a threat will increase in popularity in the future since not relying on executable files does give con artists a significant advantage in carrying out these attacks. Like with other ransomware Trojans, the best protection against the PowerWare Ransomware is to backup all files so that one can recover quickly from an attack without resorting to the payment of the ransom.
SpyHunter Detects & Remove PowerWare Ransomware
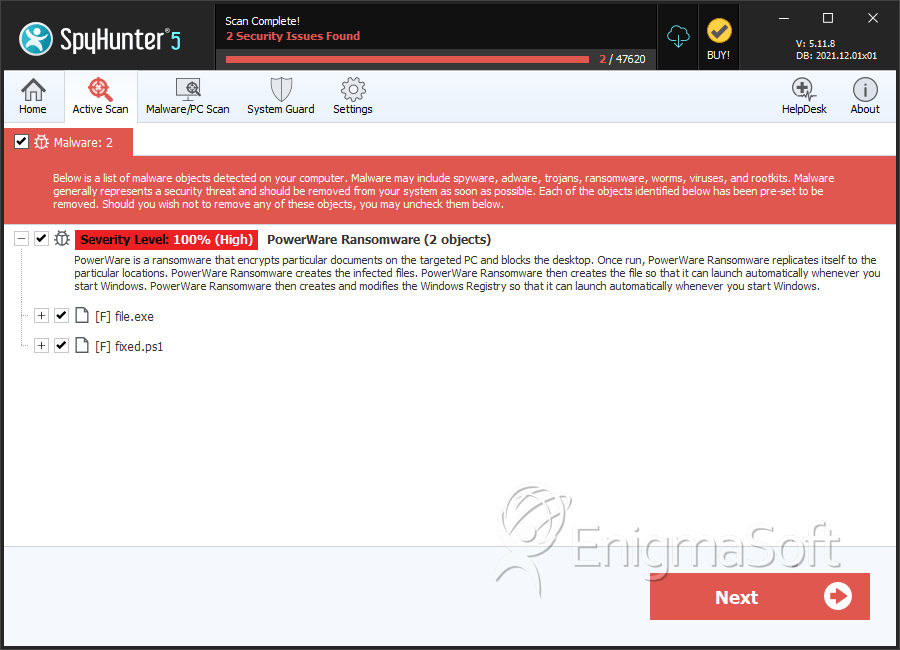
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 3433a4da9d8794709630eb06afd2b8c1 | 0 |
| 2. | fixed.ps1 | 1928d857932f23f2a47e77163cb5eb3c | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.