Phreaker Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 4 |
| First Seen: | October 6, 2022 |
| Last Seen: | March 1, 2023 |
| OS(es) Affected: | Windows |
The Phreaker Ransomware is malware based on a ransomware strain very e popular among cybercriminals, known as the Chaos Ransomware. Threats of this type are used to specifically target the data on the breached devices and render them completely unusable. Ransomware threats achieve this hurtful goal by running an encryption process with a sufficiently strong cryptographic algorithm. Restoration of the affected files is typically impossible without having the correct decryption keys.
When Phreaker is executed on an infected system, it will encrypt the documents, archives, databases, PDFs, and many other file types. Most ransomware threats mark the files they lock by attaching a specific file extension to the original file names. However, Phreaker operates in a different way - it appends the file names with a different randomly generated 4-character string. Finally, a ransom note is delivered inside a text file named 'read_it.txt.'
Phreaker's ransom note states that its victims must pay $100 to the attackers. The money must be sent to the provided crypto-wallet address using the Bitcoin cryptocurrency. In addition, the confirmation of the transaction must be sent to an email address controlled by the hackers. In exchange, victims are promised to receive the necessary decryption keys and a decryptor key. However, the ransom note doesn't contain the exact email addresses and instead has a placeholder. This means that even if victims decide to make the ransom payment, they will still have no way to restore the locked data.
The full text of Phreaker Ransomware's message is:
'Phreaker malware has infected your machine.
Lucky for you this is based out of America and we pride ourseleves on helping you get your files back.Send a small bitcoin payment off 100$ to
19DpJAWr6NCVT2oAnWieozQPsRK7Bj83r4Email @protonmail of your payment and public key to recieve your private key and decryptor.'
SpyHunter Detects & Remove Phreaker Ransomware
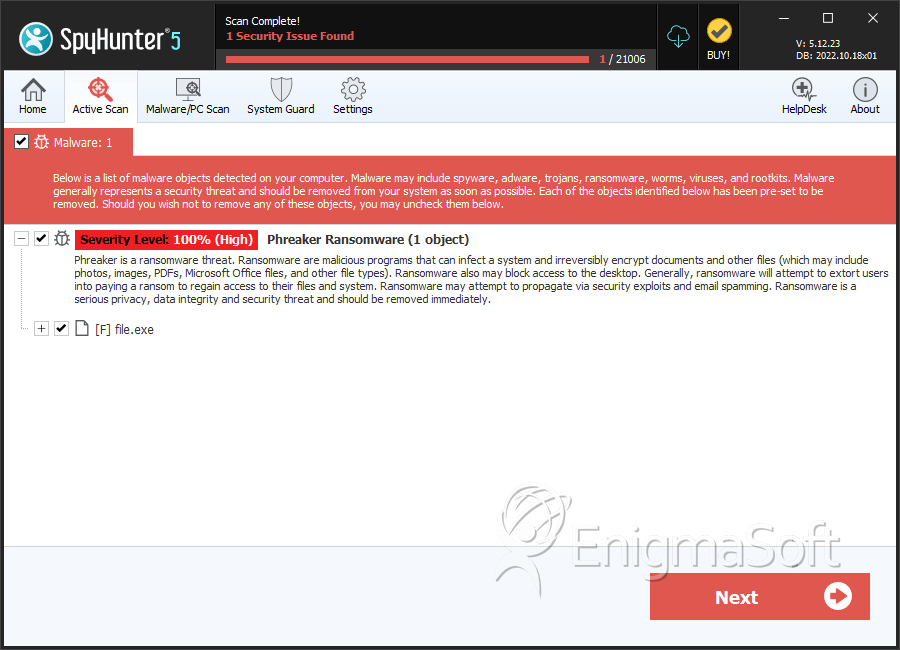
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | f4f13a5e6735a9d891a242e8d2f5c57e | 2 |

