Philadelphia Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1,284 |
| First Seen: | September 9, 2016 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |
The Philadelphia Ransomware is being sold for $400 USD. The Philadelphia Ransomware seems to be a new version of an already existing threat known as the Stampado Ransomware. A threat developer going by the name of ‘The Rainmaker’ is developed the Philadelphia Ransomware. The Philadelphia Ransomware is being offered as a cheap ransomware kit that can be used by nearly anyone to start a ransomware campaign without the need of advanced computer skills, knowledge or funding. Despite that the Philadelphia Ransomware is being advertised as an advanced ransomware threat, however, PC security researchers have determined that the Philadelphia Ransomware is most definitely not as sophisticated as most ransomware Trojans on the market.
Table of Contents
The Philadelphia Ransomware is not as Sophisticated as Its Creators Claim
The Philadelphia Ransomware is compiled using the AutoIT scripting language, which can be decompiled and studied by PC security analysts. After having studied the Philadelphia Ransomware's code, it is only a matter of time before the Philadelphia Ransomware can be decrypted (which is not the case for ransomware Trojans with more complex code and encryption methods). Many of the supposed innovations offered by the Philadelphia Ransomware have already been a standard part of numerous other ransomware Trojans, for example, the auto-detection of payments and decryption as a result, infection of USB drives, and infections distributed via a network. One particular option in the Philadelphia Ransomware that has not been seen before in other ransomware Trojans is the introduction of the 'Mercy Button,' which would allow a con artist to take pity on the victim and decrypt the victim's files for free.
Part of the advertising material linked to the Philadelphia Ransomware, as put out by The Rainmaker, include:
Everything is customisable:
You can set the folders where the Ransomware will look for files as well as the depth/recursion level
You can set the extensions, you can enable, disable and define intervals for the deadline and the russian roulette (as well as editing how many files are deleted on every russian roulette interval and whether the files or the crypt key gets deleted once the deadline ends
You can edit file icon and Mutex
You can edit the UAC (user access control) in four available options: (1) do not ask for admin privilleges; (2) ask and insist until it is given; (3) ask but run anyway even if it is not given; (4) ask and give up if it is not given
You can edit all the interface texts as well as add multiple languages to the same file (it will detect the machine language and display the texts you edited for that locale or a default/fallback one)
You can enable or disable USB infect, network spread and Unkillable Process, as well as set the process name
The the Philadelphia Headquarter is a software that works on your machine and allows you to generate unlimited builds, see the victims on a map and on a list (with country flags and all the data you need) and also a "Give Mercy" button if you're too good 0:)
But the coolest the Philadelphia feature (and what makes its maintenance so cheap) is that, instead of huge servers on our controls where you must pay high amounts monthly, we present you the "Bridges". Bridges are the way victims and attacker enters in touch in a distributed network. It's simply a PHP script that uses itself as database (no MySQL or whatever needed, just PHP). Bridges store the clients keys, verifies payments and provide the victims informations to the headquarters safely. And they can be hosted on nearly any server: even hacked servers, shared hosting (free hosting works but it is not recommended as they can delete your account if it's not a fully functional website), dedicated or VPS (recommended for bigger attacks, although the requests are small and are only done a few times). As the bitcoin payment verification is done on the server side, by the bridge, there is no way to spoof it on the victim machine. Also, the distributed bridges network will grant a better anonimity.
Everything very well documented on a plain-english help file!
One of the main problems with threat campaigns using the Philadelphia Ransomware is that they require the installation of PHP scripts called Bridges on certain websites, which receive information from the Philadelphia Ransomware with the encryption key and data about the infected computer. The Philadelphia Ransomware is controlled via a management client with all the options outlined above. However, the use of Bridge poses a fundamental problem: these cannot be stored on public websites, especially since the Philadelphia Ransomware's Bridges' IP addresses are coded into the Philadelphia Ransomware, which makes blocking them and taking them down a trivial matter. With these missing, the Philadelphia Ransomware loses all functionality, and victims cannot recover from attacks. The solution would be to implement Bridges by using an anonymous network like TOR, but this would be much too complex for the Philadelphia Ransomware's intended audience.
Apart from this odd implementation and its announce features, the Philadelphia Ransomware carries out a typical ransomware attack, encrypting the following types of files on victims' computers and demanding the payment of a ransom afterward:
*.7z;*.asp;*.avi;*.bmp;*.cad;*.cdr;*.doc;*.docm;*.docx;*.gif;*.html;*.jpeg;*.jpg;*.mdb;*.mov;*.mp3;*.mp4;*.pdf;*.php;*.ppt;*.pptx;*.rar;*.rtf;*.sql;*.str;*.tiff;*.txt;*.wallet;*.wma;*.wmv;*.xls;*.xlsx;*.zip.
SpyHunter Detects & Remove Philadelphia Ransomware
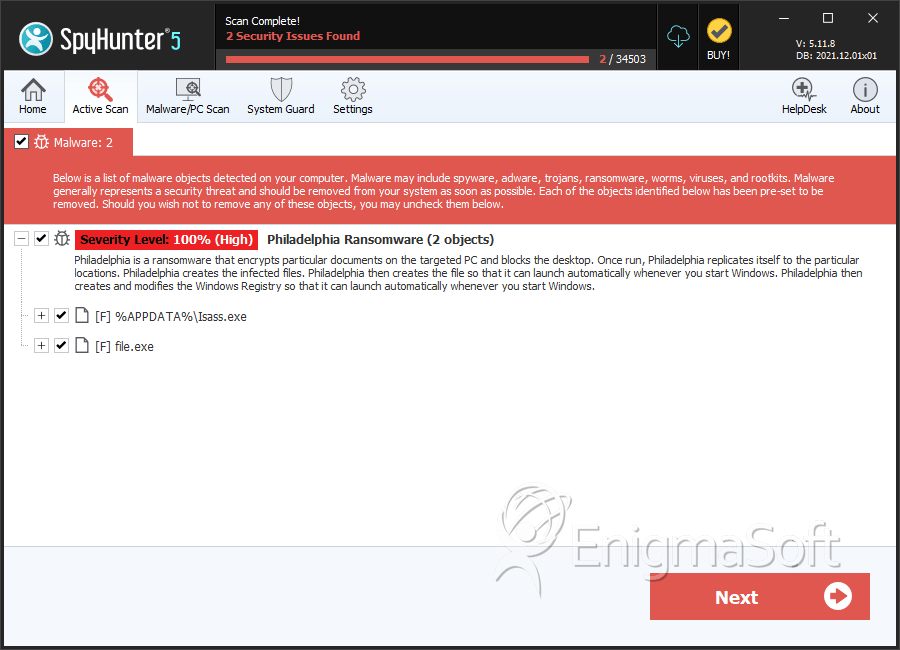
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | Isass.exe | 94910a42606413fdeb9b44346b5741c0 | 87 |
| 2. | Isass.exe | 741ed2478baaa8fd28d626bbaf7b5156 | 8 |
| 3. | file.exe | 33473f907c07244158560c052a930634 | 1 |
