NM4 Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | April 26, 2017 |
| Last Seen: | April 23, 2018 |
| OS(es) Affected: | Windows |
PC security researchers received reports of a NM4 Ransomware attack, a variant of the R Ransomware and the NMoreira Ransomware, both ransomware Trojans that carry out a fairly typical variant of this hoax. The NM4 Ransomware is being distributed through the use of spam email attachments. Ransomware campaigns like the NM4 Ransomware and associated threats created by the same hacking group that developed the NM4 Ransomware are being delivered to victims by exploiting exposed Remote Desktop Protocol connections on the Internet directly. This method of delivery may be used to compromise computers belonging to small and medium businesses, as well as Web servers and corporate networks.
Table of Contents
The NM4 Ransomware is an Updated Version of the NMoreira Ransomware
Like other ransomware Trojans, the NM4 Ransomware is designed to encrypt victims' files using a strong encryption algorithm and then demanding the payment of a ransom from the victim in exchange for the decryption key required to recover the affected files. The NM4 Ransomware will create an index file containing the files that will be targeted in the NM4 Ransomware attack. The NM4 Ransomware will target user-generated files, prioritizing Office documents, media and image files, and files generated by commonly used software. The NM4 Ransomware will add the file extension '.NM4' to the end of the file name after infiltrating a computer, making it simple to see at a glance which files have been compromised in the NM4 Ransomware attack. The NM4 Ransomware will work in the background to make the victim's files inaccessible after infiltrating a computer. The victims of the attack may not notice that anything is wrong until it is too late to react. Unfortunately, the NM4 Ransomware as part of its encryption process also will delete the Shadow Volume Copies of affected files and System Restore points, as well as other possible recovery methods that the victim could use to undo the NM4 Ransomware attack. The NM4 Ransomware delivers a ransom note in the form of an HTML file named 'recovers_your_files.html' on the victim's computer's Desktop. The following message is contained in the NM4 Ransomware's HTML ransom note:
'Your Key: [RANDOM CHARACTERS]'
Encrypted files!
All your files are encrypted using AES256-bit encryption and RSA-2048-bit encryption.
Making it impossible to recover files without the correct private key.
If you are interested in getting is the key and recover your files
You should proceed with the following steps.
The only way to decrypt your files safely is to buy the Descrypt and Private Key software.
Any attempts to restore your files with the third-party software will be fatal for your files!
To proceed with the purchase you must access one of the link below
[LINKS TO TOR-BASED PAGES]'
Dealing with a NM4 Ransomware Attack
Unfortunately, it may not be possible to recover the files affected by the NM4 Ransomware attack currently. The ransom amount associated with the NM4 Ransomware is quite high: 3 BitCoins (approximately $3900 USD at the current exchange rate). Computer users should refrain from paying the NM4 Ransomware's ransom. Apart from the fact that it is quite a lot of money, the people responsible for these attacks may ignore payment, demand additional payments or reinfect the victim's computer. Furthermore, paying these ransoms finances the activities of the extortionists, allowing them to continue creating and developing threats like the NM4 Ransomware and their variants. Instead, ensure that you are protected against these attacks. The best protection against ransomware Trojans is to have file backups on an external memory device or the cloud (on a system that is not synchronized with the main computer). Having the power to restore the affected files from a backup copy quickly and easily nullifies the con artists' attack completely, allowing computer users to be protected from the NM4 Ransomware and similar threats.
SpyHunter Detects & Remove NM4 Ransomware
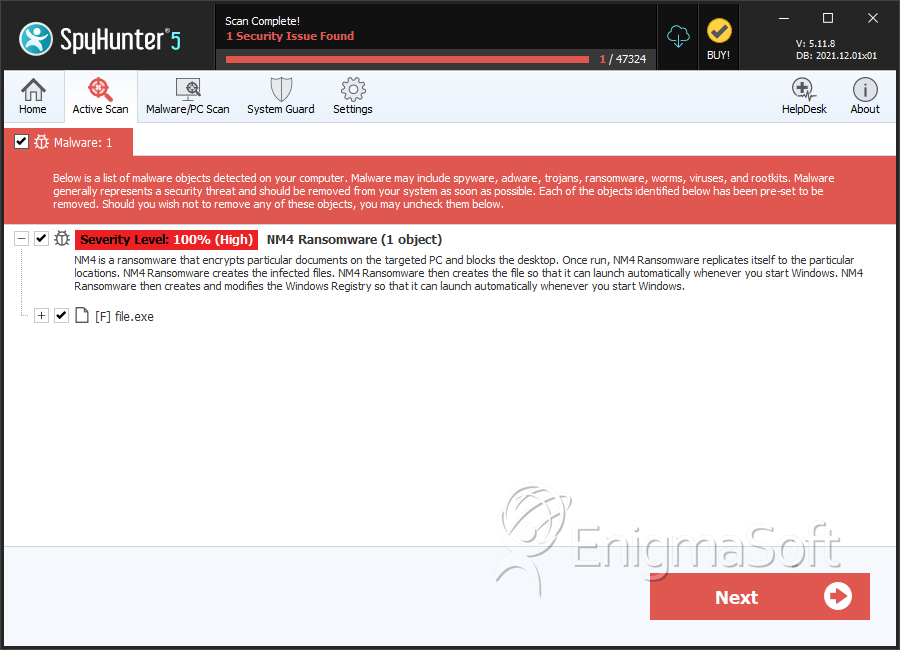
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 85655540a87585854473ce505427ddc1 | 0 |
| 2. | file.exe | f24feeac576c5ac6562167097832a1c0 | 0 |
| 3. | file.exe | 4bf285474eb7175b53158d70f9ba755e | 0 |
| 4. | file.exe | 69bf4135b1dc686406acd9124e344652 | 0 |
| 5. | file.exe | d396b18740bf4951637cc088b24caad0 | 0 |
| 6. | file.exe | 0dbf2623fef240d4442843272fb73007 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.