Nile Ransomware
Nile Ransomware Image
Modern cyber threats are usually focused on generating revenue for their creators by exploiting the victim in every possible way – some threats are dedicated to collecting payment information, while others try to collect login details and other data that may be sold to other cybercriminals. Ransomware, however, continues to be one of the favorite extortion tools in the arsenal of cybercriminals. Ransomware is a threat that works by encrypting the contents of various files and then offering to provide the victim with a recovery option in exchange for money. Over the past three years, anti-virus product vendors around the world have classified and analyzed hundreds of unique file-lockers that work in a very similar way.
One of the latest additions to the list of active file-encryption Trojans is the Nile Ransomware – this threat is not entirely new, and malware researchers found out that it shared many similarities with the very popular STOP Ransomware family. Unfortunately, the similarities with an old ransomware family are not good news, because both the STOP Ransomware and the Nile Ransomware are not compatible with free decryption tools. Their victims have very limited file recovery options, and they often may be unable to fully recover from the attack.
The STOP Ransomware Legacy Continues with the Nile Ransomware
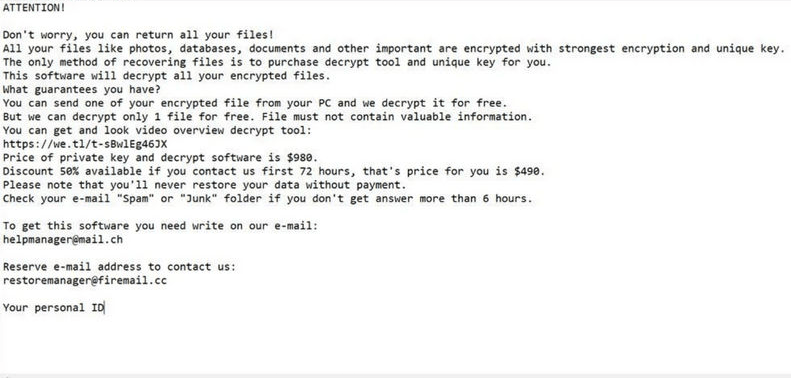
The con artists behind the Nile Ransomware project are using various tricks to spread it online – fake downloads, fake updates, corrupted advertisements and email spam. Users who run the Nile Ransomware on an unprotected system may soon realize that many of their important files have been locked. These files can be spotted by the '.nile' extension that the ransomware adds to their names during the attack. Last but not least, the Nile Ransomware drops a ransom message called '_readme.txt' – it explains the attack to the victim and lists the perpetrators' demands.
The attackers state that they are selling a decryptor for $490, and they warn the victim that this promotional price will only be valid for the next 72 hours – if $490 worth of Bitcoin has not been transferred to their account after 72 hours, they will double the ransom amount. Finally, their message lists the emails helpmanager@mail.ch and restoremanager@airmail.cc that can be used to get in touch.
Ransomware victims should consider paying the ransom fee a last resort – do not forget that the attackers are anonymous cybercriminals who have tricked thousands of users in the past, and they will not hesitate to collect your money too. Sending them Bitcoin is not recommended since it would be impossible to get the money back if they do not honor their promise. If the Nile Ransomware has harmed your files, we suggest using an anti-malware scanner to eliminate the threat, and then try out some of the most popular file recovery options and tools.

