Naikon APT
 Naikon is the name of an APT (Advanced Persistent Threat) that is believed to originate from China. The Naikon hacking group was first spotted over a decade ago, back in 2010. The Naikon APT made headlines in 2015 when the infrastructure used by the cyber crooks was uncovered by malware researchers. Thanks to this exposé, one of the members of the Naikon hacking group was caught by law enforcement. After this gaffe, cybersecurity analysts assumed that the Naikon APT had gone out of business. However, the Naikon hacking group has reemerged with the Aria-body backdoor Trojan recently – a new threat that has a multitude of features.
Naikon is the name of an APT (Advanced Persistent Threat) that is believed to originate from China. The Naikon hacking group was first spotted over a decade ago, back in 2010. The Naikon APT made headlines in 2015 when the infrastructure used by the cyber crooks was uncovered by malware researchers. Thanks to this exposé, one of the members of the Naikon hacking group was caught by law enforcement. After this gaffe, cybersecurity analysts assumed that the Naikon APT had gone out of business. However, the Naikon hacking group has reemerged with the Aria-body backdoor Trojan recently – a new threat that has a multitude of features.
Table of Contents
Niakon Attacks Attempt to Evade Detection
The Naikon APT is a hacking group that tends to target government officials and institutions. Most of the attacks carried out by the Naikon hacking group are concentrated in the Philippines, Vietnam, Indonesia, Myanmar, Brunei and Australia. Most of the government institutions targeted by the cyber crooks from the Naikon APT usually operate in the foreign affairs sector or science and technology industry. Some businesses and companies, which are government-owned, have reportedly been targeted by the Naikon APT also.
Observing the hacking arsenal of the Naikon APT, malware researchers have concluded that these individuals tend to carry out long-term reconnaissance and espionage operations. This is very typical for hacking groups that target foreign governments and officials. The recent Naikon operation that involved the aforementioned Aria-body hacking tool targeted the Australian government. The goal of the Aria-body backdoor Trojan was to collect data and assume control of the targeted government-linked systems. It is likely that after one of the members of the Naikon APT was caught back in 2015, the hacking group decided to start operating more silently to avoid detection by malware analysts. This likely misled the experts into believing that the Naikon hacking group has retired.
The Naikon hacking group propagates the Aria-body malware via spear-phishing emails. The emails in question were crafted to avoid raising suspicion in the target specifically. The fake emails would contain a corrupted attachment whose goal is to exploit a vulnerability that can be found in the Microsoft Office service.
Naikon Gets a New Lifeline for Targeted Attacks
Even though Naikon remained seemingly dormant for years and some were even speculating that the APT has been disbanded following a detailed 2015 report on its structure, it has now once again reared its head.
Researchers working with Check Point discovered that Naikon spent the last few years continuously targeting the same region – countries and organizations located in the Asia Pacific region. Territories attacked by Naikon include Australia, Indonesia, Vietnam, Brunei, Thailand and Myanmar. The chief tool used in those attacks was Naikon’s Aria-body backdoor and RAT tool.
The organizations targeted in more recent attacks include government ministries and corporations owned by the respective country’s government. A curious observation is that once Naikon gains a foothold in a foreign entity, it then uses it to further spread malware. One such example is a foreign embassy that was used to spread malware to the government of its host country. This approach uses known and trusted contacts within the embassy, which makes infiltration easier.
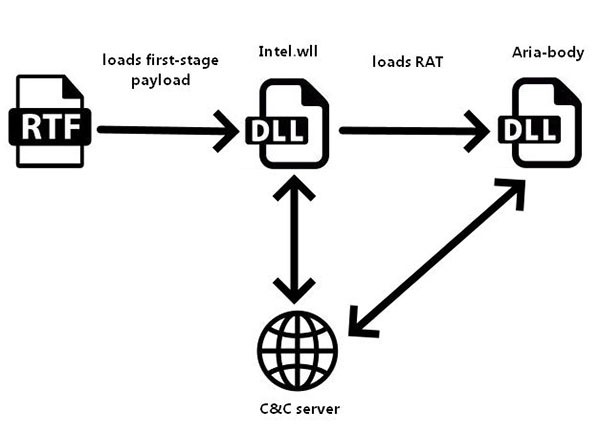
In a recent attack, the Aria-body payload was delivered through a Rich Text Format file named "The Indian Way.doc". The file was weaponized to use certain exploits using the RoyalRoad tool. Once the Rich Text Format file is opened, it drops a file named "Intel.wll", which acts as a loader that attempts to download the second-stage payload from a remote domain.
Experts believe the purpose of Naikon’s attacks is gathering intelligence and spying on governments. The bad actors behind the Naikon APT can access files on infected systems and even log keystrokes and take screenshots. Part of the reason why the APT evaded detection of its more recent activities for so long was that Naikon used government servers that were already compromised as its command and control points.
The Naikon APT has not hung up their gloves yet, certainly. However, the cyber crooks have taken some measures to remain under the radar of cybersecurity researchers.
Naikon APT Targets
Comparing the recent attacks to the ones from several years ago show that Naikon APT continues to target the same regions. As mentioned, their targets five years ago included governments across the Asia-Pacific region, and their recent attacks appear to do the same.
One interesting thing to note about the group is that they have been slowly expanding their foothold in various governments. The group does this by launching attacks from one breached government in an attempt to infect another government. There was one case where a foreign embassy unknowingly sent infected documents to the government of its host country. This incident shows just how effectively the hackers are exploiting trusted contacts to infiltrate new targets and further developer their espionage network.
Given the capabilities and targets of Naikon APT, it becomes clear that the purpose behind the attacks is to spy on the target governments and gather intelligence on them. The group is gathering specific documents from their targets within government departments, and also grabbing data from removable drives, collecting screenshots of infected computers, and using the stolen data for espionage.
If all that wasn’t bad enough, Naikon APT has proven adept at evading detection when passing through government networks. The group does this by compromising servers within an infected ministry and using those computers as a command and control server to collect and send the stolen data. It is almost impossible to trace them thanks to this infection method. This was one of the ways that they were able to avoid detection for five years.
The Aria-Body Infection Chain
Research shows the group has several different ways to infect computers with Aria-Body. The investigation into the group started when researchers spotted a malicious email sent to the Australian state government by a government embassy in the region. The infected document was called "The Indians Way" and was an RTF file. The file was weaponized with the RoyalRoad exploit builder, which drops the intel.wll loader into the Word folder on the computer. The loader attempts to download the next stage of infection from spool.jtjewifyn[.]com and execute it.
This wouldn’t be the first time that hackers have used the RoyalRoad malware to make the final delivery. Other ATP groups, such as Vicious Panda, also use the RoyalRoad delivery method. Naikon has also been seen using archive files that contain legitimate files loaded with malicious DLL files. This method takes advantage of Outlook and other legitimate executable files to conduct a cyber-attack on a target. Naikon APT appears to have gotten very adept at hiding in plain sight.
Naikon’s First-stage Loader
Before the Aria-body RAT is deployed, the first-stage loader performs a number of tasks on the infected system. The loader is responsible for ensuring persistence on the victim's machine, often using the Startup folder. Then the payload injects itself into another process, with some examples of targeted processes being dllhost.exe and rundll32.exe. The loader decrypts its configuration and contacts the C&C to download the next stage payload - the Aria-body RAT, which is then decrypted and loaded.
Naikon's Aria-body Process Path
A Closer Look at Aria-body
The recent attacks carried out by Naikon once again used the Aria-body custom RAT, likely developed by the APT for its purposes. The filename of the payload is what researchers used for its name - aria-body-dllx86.dll. The custom RAT has the functionality found in most other RATs:
- manipulation of files and directories
- taking screenshots
- searching for files
- launching files using the ShellExecute function
- closing a TCP session
- checking a victim system's location, using Amazon's 'checkip' service
Researchers have spotted different instances of Aria-body that had some of the following functionality as well:
- gathering USB data
- keystroke logger
- reverse socks proxy
Aria-body's first task is to scrape as much information about the victim system as possible. Details collected include host name, username, OS version, CPU frequency, MachineGUID key and public IP address. The collected chunk of data is zipped with a randomly generated password that is then encrypted.
The RAT can communicate with its C&C servers using either HTTP or TCP. Which of the protocols is used is determined by a flag in the loader's configuration. The victim zipped system data is transferred to the C&C together with the encrypted archive password. After the transfer is complete, the RAT starts listening to its C&C for incoming commands.

