MVP Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 23 |
| First Seen: | September 13, 2018 |
| Last Seen: | June 14, 2022 |
| OS(es) Affected: | Windows |
The MVP Ransomware is a variant in the Scarab family of ransomware, which has seen multiple releases in 2018. The MVP Ransomware was first observed on September 10, 2018. The MVP Ransomware is mainly being delivered to victims through the use of corrupted spam email messages containing Microsoft Word documents with embedded macro scripts. Computer users should take precautions against the MVP Ransomware and similar threats because sometimes, very simple measures can avoid huge problems.
Table of Contents
Why the Presence of the MVP Ransomware can Cause So Many Problems
The MVP Ransomware carries out a typical encryption ransomware Trojan attack, very similar to the ones perpetrated by the Scarab Ransomware family members, by using the AES encryption to make the victim's files inaccessible so that they may be willing to pay an asked ransom. The MVP Ransomware adds the file extension '.mvp' to each file it encrypts in the MVP Ransomware attack, and also encrypts the files' names, making them appear with ransom characters. The MVP Ransomware and its variants will target these file kinds in their attacks:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
The MVP Ransomware’s Ransom Note
The MVP Ransomware delivers a text note with a ransom demand. This ransom note is written in Russian and is named 'Как расшифровать файлы.TXT' ('How to decrypt files.txt'). The MVP Ransomware's ransom note exhibits the following context:
'Напишите на почту - thermal@cock.li
ВАШИ ФАЙЛЫ ЗАШИФРОВАНЫ!
Ваш личный идентификатор
[random characters]
Ваши документы, фотографии, базы данных и другие важные файлы были зашифрованы.
Каждые 24 часа удаляются 24 файла, необходимо прислать свой идентификатор чтоб мы отключили эту функцию.
Каждые 24 часа стоимость расшифровки данных увеличивается на 30% (через 72 часа сумма фиксируется)
Для расшифровки данных:
Напишите на почту - thermal@cock.li
*В письме указать Ваш личный идентификатор
*Прикрепите 2 файла до 1 мб для тестовой расшифровки.
мы их расшифруем, в качестве доказательства, что ТОЛЬКО МЫ можем их расшифровать.
-Чем быстрее вы сообщите нам свой идентификатор, тем быстрее мы выключим произвольное удаление файлов.
-Написав нам на почту вы получите дальнейшие инструкции по оплате.
В ответном письме Вы получите программу для расшифровки.
После запуска программы-дешифровщика все Ваши файлы будут восстановлены.
Внимание!
* Не пытайтесь удалить программу или запускать антивирусные средства
* Попытки самостоятельной расшифровки файлов приведут к потере Ваших данных
* Дешифраторы других пользователей несовместимы с Вашими данными, так как у каждого пользователя
уникальный ключ шифрования
Ваш личный идентификатор
[random characters]'
The above, translated into English, reads as follows:
'Write to the e-mail - thermal@cock.li
YOUR FILES ARE STRIKED!
Your personal identifier
[random characters]
Your documents, photos, databases and other important files have been encrypted.
Every 24 hours 24 files are deleted, you need to send your ID so that we disable this function.
Every 24 hours the cost of decrypting data is increased by 30% (after 72 hours the amount is fixed)
To decrypt the data:
Write to mail - thermal@cock.li
* In the letter, enter your personal identifier
* Attach 2 files to 1 mb for test decryption.
we decipher them, as evidence that ONLY WE can decipher them.
- The faster you tell us your ID, the faster we turn off arbitrary deletion of files.
-Writing to us on the mail you will receive further instructions on payment.
In the reply letter you will receive a program for decryption.
After starting the decryption program, all your files will be restored.
Attention!
* Do not attempt to uninstall the program or run antivirus software
* Attempts to self-decrypt files will result in the loss of your data
* Decoders of other users are incompatible with your data, as each user
unique encryption key
Your personal identifier
[random characters]'
Computer users are counseled not to follow the instructions proposed by the MVP Ransomware's ransom note. Instead, computer users should take preventive steps, such as using a security program and having backup copies of their files stored on the cloud or an external memory device.
SpyHunter Detects & Remove MVP Ransomware
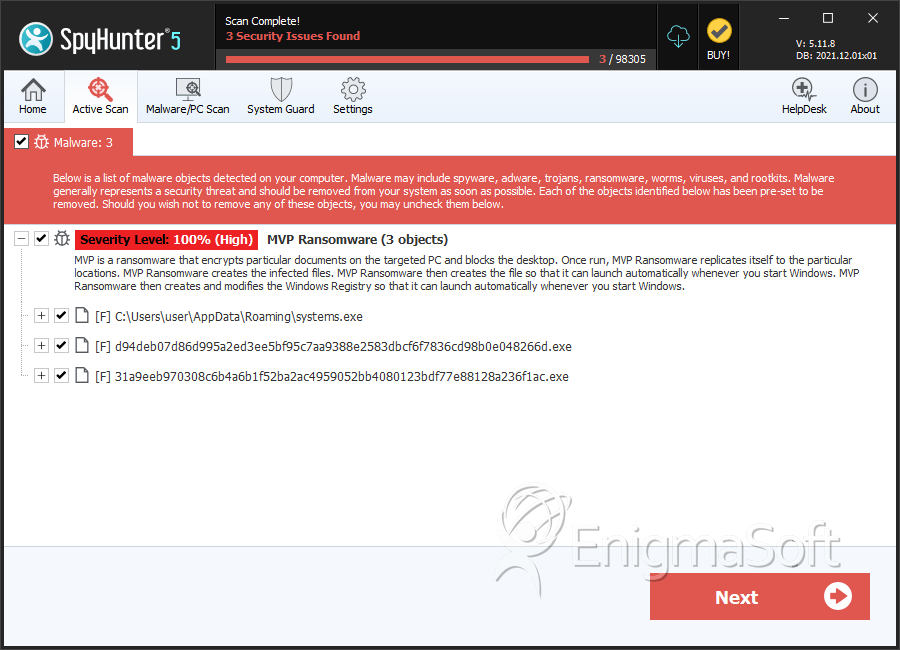
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | systems.exe | db8d2fa8ab3ae1ed767e34792ee23629 | 2 |
| 2. | d94deb07d86d995a2ed3ee5bf95c7aa9388e2583dbcf6f7836cd98b0e048266d.exe | 31de54d2714627b215cb8f114c31256f | 1 |
| 3. | 31a9eeb970308c6b4a6b1f52ba2ac4959052bb4080123bdf77e88128a236f1ac.exe | 138b6212915492757fe767e062e0fe00 | 0 |