Microsoft Decryptor Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 3 |
| First Seen: | July 11, 2016 |
| Last Seen: | April 18, 2018 |
| OS(es) Affected: | Windows |
The Microsoft Decryptor Ransomware is a ransomware Trojan that recycles elements of previous threats. The Microsoft Decryptor Ransomware is an updated clone of the UltraCrypter and the CryptXXX, both threatening ransomware Trojans that have identical ways of attacking computers. Like other ransomware Trojans, the Microsoft Decryptor Ransomware uses an asymmetric encryption method to encrypt victims' files and asks for the payment of a ransom in exchange for the decryption key. The Microsoft Decryptor Ransomware, unlike many other similar threats, does not change the affected files' extensions (a feature that may be used to differentiate one encryption ransomware Trojan from another. The Microsoft Decryptor Ransomware will introduce its ransom message by delivering three files to the victim's computer, dropping a copy in each directory where it encrypted content. The three files are named 'README' and have the extensions TXT, BMP and HTML (a text file, an image file and an online Web page). These files contain identical content, alerting the victim of the attack and demanding the payment of the ransom.
Table of Contents
How Con Artists can Profit from the Microsoft Decryptor Ransomware Infection
The Microsoft Decryptor Ransomware's ransom notes contain information on what happened to the victim's files and how to pay the ransom. Unfortunately, to get back the files encrypted by the Microsoft Decryptor Ransomware the infected computer user needs the decryption key, which is in the con artists' hands. These people take the victim's files hostage essentially, by offering the private key in exchange for the payment of 1.2 BitCoin (approximately $800 USD at the current average exchange rate). According to the Microsoft Decryptor Ransomware's ransom note, the ransom is doubled (2.4 BitCoin) if it is not paid immediately. Payment is carried out through the Tor browser, which allows the con artists to remain anonymous throughout the attack.
How the Microsoft Decryptor Ransomware may be Distributed
Most ransomware Trojans are very similar and use common threat delivery avenues to enter a computer. The most common sources for threats like the Microsoft Decryptor Ransomware include corrupted email attachments and embedded links, fake software updates, and files distributed through peer-to-peer (P2P) file sharing networks. The Microsoft Decryptor Ransomware also may be installed by other threats or linked to a different infection. Caution online and the use of reliable security programs that are fully up-to-date are the best ways to ensure that the Microsoft Decryptor Ransomware and similar threats don't enter your computer.
The following is the full text of the Microsoft Decryptor Ransomware's ransom notes:
What happened to your files ?
All of your files were protected by a strong encryption with RSA4096
More information about the encryption keys using RSA4096 can be found here: hxxp://en.wikipedia.org/wiki/RSA_(cryptosystem)
How did this happen ?
!!! Specially for your PC was generated personal RSA4096 Key , both public and private.
!!! ALL YOUR FILES were encrypted with the public key, which has been transferred to your computer via the Internet.
!!! Decrypting of your files is only possible with the help of the private key and decrypt program , which is on our Secret Server
What do I do ?
So , there are two ways you can choose: wait for a _miracle_ and get _your_ PRICE DOUBLED! Or start obtaining *BITCOIN NOW! , and restore _YOUR_ _DATA_ easy way
If You have really valuable _DATA_, you better _NOT_ _WASTE_ _YOUR_ _TIME_, because there is _NO_ other way to get your files, except make a _PAYMENT_
Your personal ID:
For more specific instructions, please visit your personal home page, there are a few different addresses pointing to your page below:
1 - http://*************.onion.to
2 - http://*************.onion.city
If for some reasons the addresses are not availablweropie, follow these steps:
1 - Download and install tor-browser: hxxp://www.torproject.org/projects/torbrowser.html.en
2 - Video instruction: hxxps://www.youtube.com/watch?v=NQrUZdsw2hA
3 - After a successful installation, run the browser
4 - Type in the address bar: http://*************.onion
5 - Follow the instructions on the site
Once computer users enter the anonymous website associated with the Microsoft Decryptor Ransomware, the following instructions appear:
How to use the Microsoft Decryptor?
Decrypt Soft Help
To decrypt your files you need to make pay for the Microsoft Decryptor and receive a private key to decrypt your files
Download the Microsoft Decryptor to begin to decrypt your files
The link to download the program will appear here, after you pay
Note that the con artists claim that the Microsoft Decryptor Ransomware is related to Microsoft, a claim that is easily refuted, but that may trick inexperienced computer users into paying the Microsoft Decryptor Ransomware's ransom more readily. The following text is included in a FAQ (Frequently Asked Questions) section of the Microsoft Decryptor Ransomware website:
We present a special software - the Microsoft Decryptor - which allows to decrypt and return control to all your encrypted files.
Question: How can I decrypt my files after the payment?
Answer: After the successful payment, you can download the Microsoft Decryptor on your personal page. We guarantee that all your files will be successfully decoded.
Question: What exactly should I specify in the field "Transaction ID"?
Answer: Specify the transaction ID you received during the Bitcoin successful purchase on the merchant’s site.
SpyHunter Detects & Remove Microsoft Decryptor Ransomware
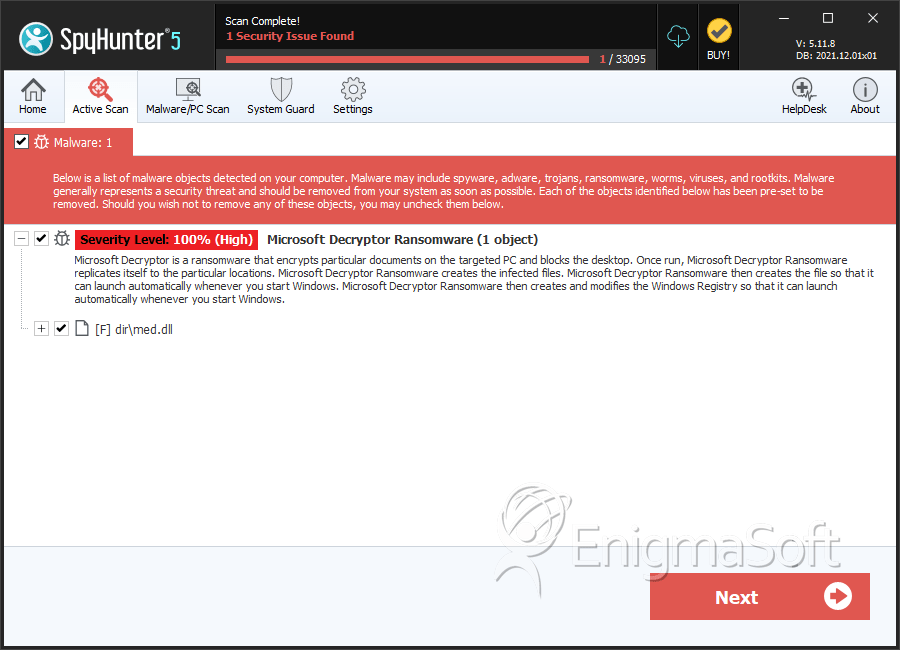
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 272eb6ff1aaa98dc3e36b35a0a9bd10ce8e79344cbf2c33104a4d470be8a9eac | 0bcca95bdc4e404da1754142e80e72d0 | 1 |
