CryptXXX Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 255 |
| First Seen: | April 21, 2016 |
| Last Seen: | April 8, 2022 |
| OS(es) Affected: | Windows |
The CryptXXX Ransomware is a ransomware Trojan. The CryptXXX Ransomware does not limit its attack to encrypting the victim's files; the CryptXXX Ransomware also has the capacity of taking BitCoins from the victim's wallet and collect passwords from the infected computer. The combination of a ransomware Trojan with information collecting components has proven to be highly effective and with a great potential for future attacks. PC security analysts are concerned that the addition of an information collecting component to the CryptXXX Ransomware infection could set a new standard for encryption ransomware Trojans in the future.
Table of Contents
Besides Encrypting Files, the CryptXXX Ransomware may Execute Additional Harmful Actions
The CryptXXX Ransomware encrypts the victim's files using the AES encryption. The CryptXXX Ransomware also may collect BitCoins, passwords, and other private data from the infected computer. The CryptXXX Ransomware was first detected in late March of 2016. PC security researchers have associated the CryptXXX Ransomware with the Angler Exploit Kit, which has been used to compromise various websites. This exploit kit is used to leverage vulnerabilities on the victim's computer to install Bedep on the victim's computer. Bedep is a Trojan downloader that may download and install the CryptXXX Ransomware and other possible threats on the victim's computer. The CryptXXX Ransomware downloads a delayed execution DLL file, which waits 62 minutes before launching on the victim's computer. After the time has elapsed, the CryptXXX Ransomware carries out its attack, encrypting the victim's files and collecting important data and money in the form of BitCoins.
Mapping the CryptXXX Ransomware Infection
The CryptXXX Ransomware asked ransom is 1.2 BitCoins. After encrypting the victim's files, the CryptXXX Ransomware changes the victim's Desktop image into its ransom message and drops text and HTML ransom notes on the victim's computer. The CryptXXX Ransomware's ransom messages are instantly recognizable and can be used to identify this threat. The files associated with these ransom notes are named 'de_crypt_readme.txt' and 'de_crypt_readme.html.' The CryptXXX Ransomware appends the file extension 'crypt' to the files it has encrypted. At the current rate, the CryptXXX Ransomware ransom averages at about $515 USD, an amount that is significantly higher than the average encryption ransomware threats.
The Information Collecting Capabilities of the CryptXXX Ransomware
Bedep has been used to deliver data collecting threats in the past. In this case, the CryptXXX Ransomware also will contain a feature that allows it to collect data from the victim's computer. The CryptXXX Ransomware can collect files, passwords, and other data, focusing on login credentials from the victim's instant messenger applications, email clients, FTP programs, and Internet browsers particularly. The CryptXXX Ransomware also may collect BitCoin wallet credentials according to reports from PC security researchers. PC security analysts have detected a link between the CryptXXX Ransomware and Reveton, an older ransomware threat that was quite effective in its time. There are various similarities, including that both threats are encoded using Delphi, use a DLL with a delayed start, the same type of function to call on the corrupted DLL file, collect BitCoins and login credentials, and make use of a custom Command and Control protocol using TCP port 443.
Who may be Responsible for the CryptXXX Ransomware?
PC security researchers suspect that the same group that created the CryptXXX Ransomware also created Bedep, the Angler Exploit Kit and Reveton. This means that the people responsible for the CryptXXX Ransomware may have significant resources and experience, making this threat particularly worrying for security researchers. Malware analysts observed a similar pattern in 2015, when the Locky Ransomware family first appeared. At first, the CryptXXX Ransomware seemed to come out of nowhere, with sophisticated new features and an approach that had not been seen before in ransomware threats. Locky quickly become one of the most widely disseminated ransomware threats. The CryptXXX Ransomware is not the work of an amateur group, and the CryptXXX Ransomware may become a significant threat in the coming year.
SpyHunter Detects & Remove CryptXXX Ransomware
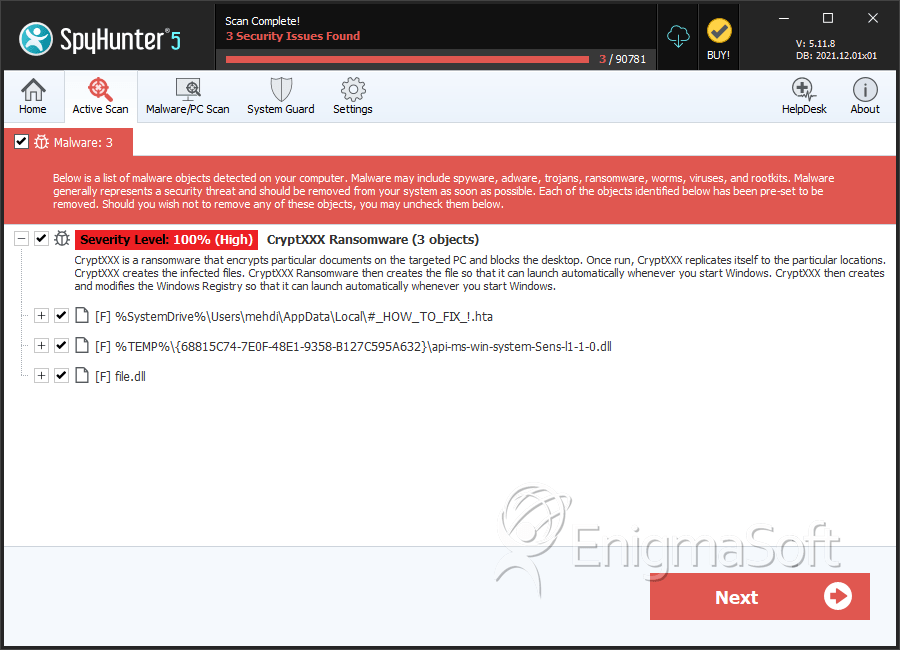
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | #_HOW_TO_FIX_!.hta | c1f3e911e6956e0162f876713b105e2f | 120 |
| 2. | #_HOW_TO_FIX_!.hta | 918f18716ec0e1aa45663729e466af26 | 49 |
| 3. | #_HOW_TO_FIX_!.hta | 392584ba2249f34ae158a516c9cebe0b | 47 |
| 4. | #_HOW_TO_FIX_!.hta | 44625edeb1d88d449a254b8cae49dc4a | 7 |
| 5. | #_HOW_TO_FIX_!.hta | 7463581a2018a2a5d15c7640e4125ead | 3 |
| 6. | file.dll | cf892c22f1b8cbdd33c11cc9050d483b | 2 |
| 7. | api-ms-win-system-Sens-l1-1-0.dll | 22288a76cfa7348ced6db347b2085f18 | 1 |
| 8. | file.dll | e46c7530f475e07bef1a87df3c14f9d6 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.