MC Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | April 27, 2018 |
| Last Seen: | April 29, 2018 |
| OS(es) Affected: | Windows |
The MC Ransomware is also referred to as the Minecraft Ransomware because it requires the victims to play the popular video game Minecraft to remove the MC Ransomware lock screen from their computers. The MC Ransomware has many elements in common with the PUBG Ransomware, a ransomware threat first observed in early April 2018. The MC Ransomware's purpose is to force computer users to play Minecraft, a popular video game published by Mojang and Microsoft. The MC Ransomware does not encrypt the victims' data, despite the fact that it claims to do so. The MC Ransomware displays a ransomware window, a sort of lock screen that will remain on the victims' computers until the victims load Minecraft onto their computers.
Table of Contents
How the MC Ransomware Attack Works
The MC Ransomware was first observed on April 18, 2018. PC security researchers have been studying a copy of the MC Ransomware that does not include an encryption component. However, it is possible that newer versions of the MC Ransomware will be capable of encrypting the victim's files. Most of these threats function by taking the victims' files hostage. To do so, threats like the MC Ransomware will use the AES encryption, or other advanced forms of encryption, to take the victim's files hostage, making them inaccessible to anyone that does not have the decryption key. These threats will target the user-generated files in their attacks, which may include the following file types:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
These attacks will avoid encrypting the Windows system files and applications since they require the victims' computers to remain functional so that the victims can read a ransom note or pay a ransom using their Web browser. The MC Ransomware and similar threats are delivered using spam email messages with corrupted file attachments, which may take the form of DOC, DOCX, or PDF files with compromised, embedded macros that download and install threats like the MC Ransomware when they are opened. Social engineering techniques may be used to convince the victim to download the damaged file attachment.
What Happens When the MC Ransomware is Installed on a PC
After the MC Ransomware being installed, the MC Ransomware displays a program window with the title 'MC Ransomware // made by NATroutter (NATroutter.net || BeaverSquad.net),' which includes an image of a building created in Minecraft and the message 'Status: Waiting for Minecraft.' This program window will remain on the victim's computer until the victim loads Minecraft. Although the MC Ransomware seems harmless, it would be trivial for the con artists to modify the MC Ransomware so that it demands a large amount of money rather than needing the victim to play a video game. Furthermore, it is not unlikely that updated versions of the MC Ransomware that use effective encryption techniques may be released to carry out attacks on victims. In fact, there are already various threatening programs active already that carry out these attacks on their victims. Because of this, it is crucial to take precautions to prevent these attacks.
SpyHunter Detects & Remove MC Ransomware
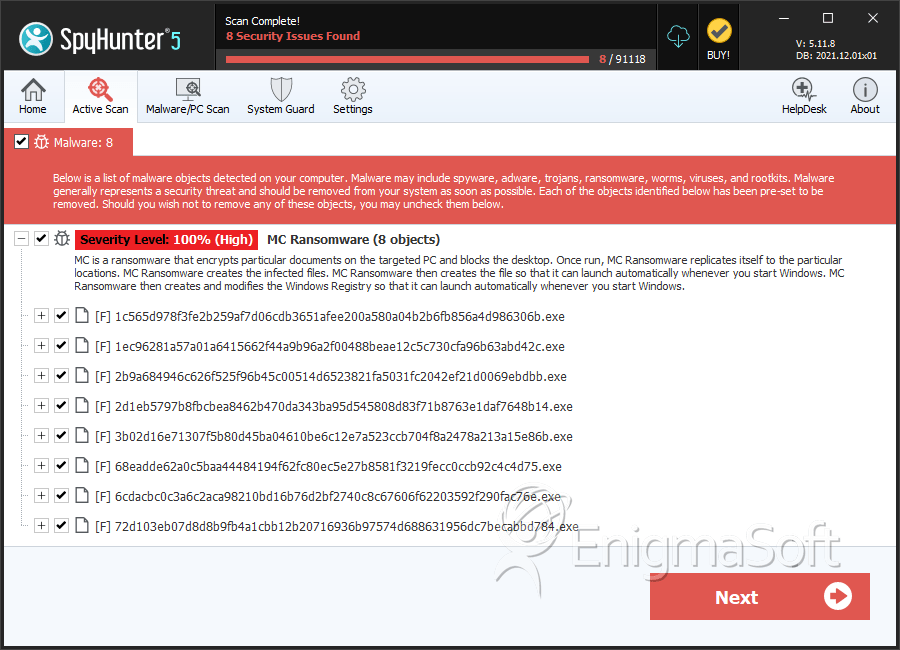
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 1c565d978f3fe2b259af7d06cdb3651afee200a580a04b2b6fb856a4d986306b.exe | 9f964893e51c95cb83ac2ff8287dd84e | 0 |
| 2. | 1ec96281a57a01a6415662f44a9b96a2f00488beae12c5c730cfa96b63abd42c.exe | 79a4eb4f496a236aae76d711b73ab2d8 | 0 |
| 3. | 2b9a684946c626f525f96b45c00514d6523821fa5031fc2042ef21d0069ebdbb.exe | 4753075e5c1f696327c9bc357827613f | 0 |
| 4. | 2d1eb5797b8fbcbea8462b470da343ba95d545808d83f71b8763e1daf7648b14.exe | cd2c72de1f36265124292031b20859df | 0 |
| 5. | 3b02d16e71307f5b80d45ba04610be6c12e7a523ccb704f8a2478a213a15e86b.exe | 8c8f54175f37f008d0aa8e7a8b8003b4 | 0 |
| 6. | 68eadde62a0c5baa44484194f62fc80ec5e27b8581f3219fecc0ccb92c4c4d75.exe | f72d5d5106d60376963dc7fcbb29e1e8 | 0 |
| 7. | 6cdacbc0c3a6c2aca98210bd16b76d2bf2740c8c67606f62203592f290fac76e.exe | 36a341d6a7b9be36066762f3532df573 | 0 |
| 8. | 72d103eb07d8d8b9fb4a1cbb12b20716936b97574d688631956dc7becabbd784.exe | dac78ca4ceb78391d08578c3d166da48 | 0 |
| 9. | 74d74e704173dc7c7253b107a0ce6316c14828b56d96d0bb7e2de2b06136c218.exe | 502ae241a3c3f48023c76c1bdcb68299 | 0 |
| 10. | 92311f839fbc21568323a3ec53c9c16d6febcf593c301c3263e453c62c1a4913.exe | 9689a763ceee30174d657a51584c469f | 0 |
| 11. | cc44cb3a4726ca2c3572344e85252b5b9536b4b1707880a859cf7592b19aa6a1.exe | 9387aa1b1442303b4b2fc3339a79ea58 | 0 |
| 12. | d39fec34e1ab238bbe2dbd7e692aef68a56adc119ef1dab4e6c2a64ccd7ecf2e.exe | def32d9aac376d36e93f59bdcc8aa8ae | 0 |
| 13. | e5d8e5e967ca27c012e15f8a675feddeaa189176cb0e237f99fdbbb9a4bad6c3.exe | 4297dec3ddaa8fdbf0f2351bc8b445bd | 0 |
| 14. | ee0b3410d48e07a0a1c5dbfab52620166712207e51e323a52d98b07b43d9d84a.exe | 4c1995ca87b5ec708891964024fe51cf | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.