Maktub Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | March 22, 2016 |
| OS(es) Affected: | Windows |
The Maktub Ransomware is a ransomware Trojan that is used to take its victims' files hostage in exchange for ransom. The Maktub Ransomware, also known as the Maktub Locker, encrypts the victim's files and changes their extension to .IAALIXR in an attack that is very similar to a wide variety of threats that have appeared in the first months of 2016. The Maktub Ransomware is most likely a variant of TeslaCrypt, which was recently released in its version 3.0. If the Maktub Ransomware has been used to encrypt your files, PC security researchers recommend removing the Maktub Ransomware immediately with the help of a reliable security program and restoring all encrypted files from a backup.
Table of Contents
What a Threat Like the Maktub Ransomware Does With Your Files
Attacks like the Maktub Ransomware are not difficult to predict. The Maktub Ransomware and its variants may be delivered by including them as corrupted email attachments. When victims click on these email attachments, the Maktub Ransomware is installed on the victim's computer. As part of its attack, the Maktub Ransomware searches for files on the victim's computer that match its configuration files. The Maktub Ransomware searches for specific extensions, allowing the Maktub Ransomware to encrypt files on the victim's computer while still permitting the victim's computer to remain functional enough to display the ransom note and give the victim the option of paying to decrypt the affected files. The following are examples of file formats that the Maktub Ransomware and similar threats search for and encrypt:
.7z; .rar; .m4a; .wma; .avi; .wmv; .csv; .d3dbsp; .sc2save; .sie; .sum; .ibank; .t13; .t12; .qdf; .gdb; .tax; .pkpass; .bc6; .bc7; .bkp; .qic; .bkf; .sidn; .sidd; .mddata; .itl; .itdb; .icxs; .hvpl; .hplg; .hkdb; .mdbackup; .syncdb; .gho; .cas; .svg; .map; .wmo; .itm; .sb; .fos; .mcgame; .vdf; .ztmp; .sis; .sid; .ncf; .menu; .layout; .dmp; .blob; .esm; .001; .vtf; .dazip; .fpk; .mlx; .kf; .iwd; .vpk; .tor; .psk; .rim; .w3x; .fsh; .ntl; .arch00; .lvl; .snx; .cfr; .ff; .vpp_pc; .lrf; .m2; .mcmeta; .vfs0; .mpqge; .kdb; .db0; .DayZProfile; .rofl; .hkx; .bar; .upk; .das; .iwi; .litemod; .asset; .forge; .ltx; .bsa; .apk; .re4; .sav; .lbf; .slm; .bik; .epk; .rgss3a; .pak; .big; .unity3d; .wotreplay; .xxx; .desc; .py; .m3u; .flv; .js; .css; .rb; .png; .jpeg; .txt; .p7c; .p7b; .p12; .pfx; .pem; .crt; .cer; .der; .x3f; .srw; .pef; .ptx; .r3d; .rw2; .rwl; .raw; .raf; .orf; .nrw; .mrwref; .mef; .erf; .kdc; .dcr; .cr2; .crw; .bay; .sr2; .srf; .arw; .3fr; .dng; .jpeg; .jpg; .cdr; .indd; .ai; .eps; .pdf; .pdd; .psd; .dbfv; .mdf; .wb2; .rtf; .wpd; .dxg; .xf; .dwg; .pst; .accdb; .mdb; .pptm; .pptx; .ppt; .xlk; .xlsb; .xlsm; .xlsx; .xls; .wps; .docm; .docx; .doc; .odb; .odc; .odm; .odp; .ods; .odt.
When the Maktub Ransomware finds files with the above extensions (with new extensions added to the list in each update), the Maktub Ransomware uses AES encryption to encrypt the files and change their extensions. The Maktub Ransomware also delivers ransom notes that contain information on how to pay the ransom and supposedly regain access to the encrypted files. The following is an example of a ransom note that has been associated with the Maktub Ransomware:
Your documents, photos, databases and other important files have been encrypted with strongest encryption and unique key, generated for this computer. Private decryption key is stored on a secret Internet server and nobody can decrypt your files until you pay and obtain the private key. The server will eliminate the key after a time period specified in this window.
Open http://bs7aygotd2rnjl4o.onion.link or
http://bs7aygotd2rnjl4o.torstorm.org or
http://bs7aygotd2rnjl4o.tor2web.org
in your browser. They are public gates to the secret server.
If you have problems with gates, use direct connection:
1) Download TOR Browser from http://torproject.org
2) In the Tor Browser open the http://bs7aygotd2rnjl4o.onion
You should avoid paying the ransom that is demanded by this threat. There is no guarantee that these people will deliver the decryption key once the ransom is paid. The best protection against these threats is to backup all files on an external device or the cloud. This way, victims can restore the encrypted files and recover from attack. There is currently no way to decrypt the files encrypted by this threat without access to the decryption key.
SpyHunter Detects & Remove Maktub Ransomware
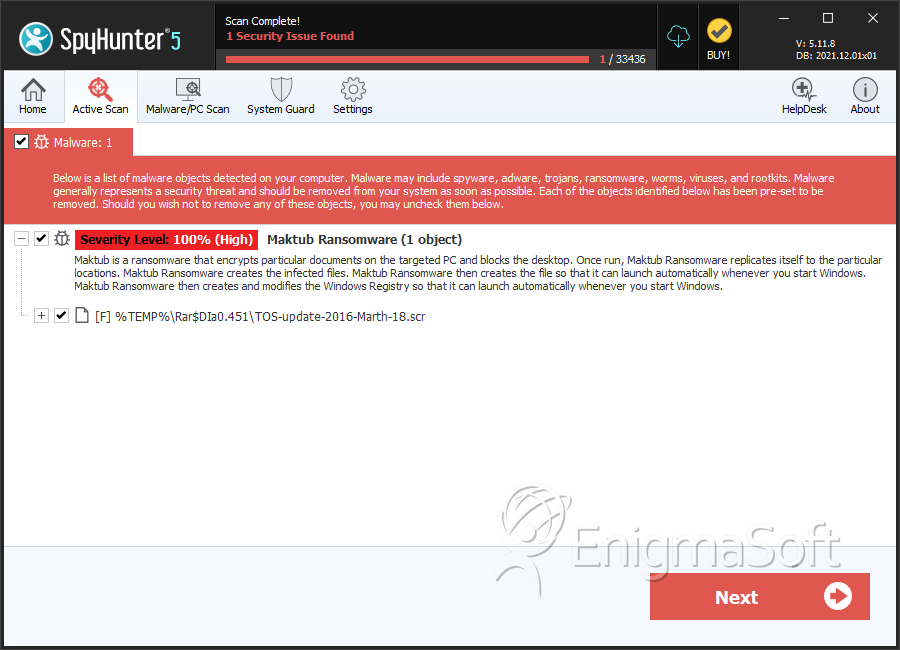
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | TOS-update-2016-Marth-18.scr | 74add6536cdcfb8b77d10a1e7be6b9ef | 1 |

