LOCKFILE Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 2 |
| First Seen: | March 1, 2022 |
| OS(es) Affected: | Windows |
The LOCKFILE Ransomware appears to be mostly targeting Russian-speaking users. The threat operates as expected for a ransomware threat - first, it infiltrated the targeted system, then it scans the present files on the machine, before encrypting nearly all of them with an uncrackable cryptographic algorithm. The LOCKFILE Ransomware is a threat from the Xorist Ransomware family.
Each file locked in this manner also will have '.LOCKFILE' added to its original name as a new file extension. To make sure that victims see its instructions, LOCKFILE shows ransom-demanding messages as two pop-up windows and a 'ДЕБЛОКИРОВКА ФАЙЛОВ.txt' file. All three are in Russian entirely.
Table of Contents
Demands Overview
Victims who do not have the Cyrillic font package installed on their systems may experience errors while viewing the ransom note. A common occurrence is for the note to display gibberish and incomprehensible symbols. A rough translation of the notes, reveals that the cybercriminals give their victims 24 hours to establish communication. After that period is over, all encrypted files will supposedly be deleted and will no longer be recoverable. Victims also can experience loss of data if they input the wrong decryption code more than five times. Apparently, the only way to reach out to the attackers is via their email address at 'unlockmen@excite.com.'
The note in its original language is:
'Внимание! На вашем компьютере,обнаружено нелицензионное
программное обеспечение.Доступ к вашим файлам запрещен !
Чтобы восстановить свои файлы и получить к ним доступ,
свяжитесь с нашим отделом безопасности UNLOCKMEN@EXCITE.COM
Идентификатор 86548764 (130)
Ваш компьютер поставлен на таймер самоуничтожения 24 часа , по истечении этого времени вся информация будет безвозвратно стёрта. У вас есть 5 попыток ввода кода. При превышении этого количества, все данные необратимо удаляться. Будьте внимательны при вводе кода !
Заранее благодарим за оплату ! Мы ценим ваш вклад в развитие инновационно-технического прогресса.'
SpyHunter Detects & Remove LOCKFILE Ransomware
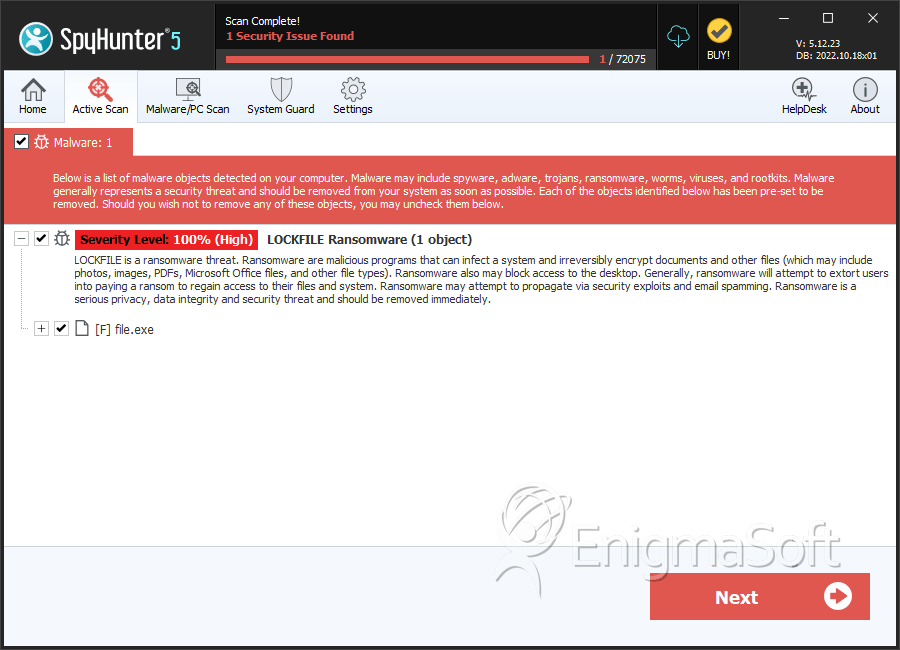
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | bf315c9c064b887ee3276e1342d43637d8c0e067260946db45942f39b970d7ce | 52e1fed4c521294c5de95bba958909c1 | 2 |
