LockeR Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 3,023 |
| First Seen: | May 28, 2015 |
| Last Seen: | September 6, 2024 |
| OS(es) Affected: | Windows |
The LockeR Ransomware is an encryption ransomware Trojan that is installed by con artists taking advantage of unsecured remote desktop accounts or through spam email message specifically. The LockeR Ransomware seems to be an independent ransomware Trojan rather than belonging to a larger family of threats. The LockeR Ransomware attacks seem to prioritize Web servers and businesses rather than individuals. The LockeR Ransomware attack's main purpose is to encrypt the victim's files by using a strong encryption algorithm.
Table of Contents
The Ransom Demanded by the LockeR Ransomware may be Very High
The LockeR Ransomware uses a strong encryption algorithm to make victims' files inaccessible, looking for the user-generated files such as those with the following file extensions specifically:
.3gp, .7z, .apk, .avi, .bmp, .cdr, .cer, .chm, .conf, .css, .csv, .dat, .db, .dbf, .djvu, .dbx, .docm, ,doc, .epub, .docx .fb2, .flv, .gif, .gz, .iso .ibooks, .jpeg, .jpg, .key, .mdb, .md2, .mdf, .mht, .mobi, .mhtm, .mkv, .mov, .mp3, .mp4, .mpg .mpeg, .pict, .pdf, .pps, .pkg, .png, .ppt .pptx, .ppsx, .psd, .rar, .rtf, .scr, .swf, .sav, .tiff, .tif, .tbl, .torrent, .txt, .vsd, .wmv, .xls, .xlsx, .xps, .xml, .ckp, .zip, .java, .py, .asm, .c, .cpp, .cs, .js, .php, .dacpac, .rbw, .rb, .mrg, .dcx, .db3, .sql, .sqlite3, .sqlite, .sqlitedb, .psd, .psp, .pdb, .dxf, .dwg, .drw, .casb, .ccp, .cal, .cmx, .cr2.
Ransomware Trojans like the LockeR Ransomware demand extraordinarily-high ransoms because their targets tend to be corporations rather than individuals. It is not uncommon for the LockeR Ransomware to demand a ransom of tens of thousands of dollars. The LockeR Ransomware payment is demanded in Bitcoins, which the victims must transfer to the con artists using TOR. The LockeR Ransomware delivers a text file to make its ransom demands as part of the attack. A file with the name [How_To_Decrypt_Files].txt, is placed on the infected computer's desktop, and it reads as follows:
'What happened to my files ?
All of your important files were encrypted using a combination of RSA-2048 and AES-256.
What does this mean ?
This means that your files were modified in a way that makes working with them impossible, unless you have the keys to decrypt them.
Is it possible to recover my files ?
Yes, it possible to get your files back, you'll need a special program (decryptor) and the private key of the key pair used to encrypt them.
How can I get the decryptor and the private key ?
You can buy both of them in any of the links below. Just visit one of them and follow the instructions.
[links to customized payment pages on the TOR network]
If you cannot access the site from any of the addresses above, you can follow the instructions below to access the site using the Tor Browser.
Download the Tor Browser Bundle here: h[tt]ps://www.torproject.org.
Execute the file you downloaded to extract the Tor Browser into a folder on your computer.
Then simply open the folder and click on "Start Tor Browser".
Copy and paste the onion address into the address bar: h[tt]p://lockerrwhuaf2jjx.onion/[unique ID]/'
Dealing with the LockeR Ransomware Infection
Computer users are counseled by security experts to refrain from paying the LockeR Ransomware ransom. The payment of the ransom does not mean that the affected files will be restored and it is not uncommon for the people responsible for these attacks to compromise the victims' files and then never respond to the ransom payment. Furthermore, paying the LockeR Ransomware ransom allows the people responsible for the LockeR Ransomware to continue financing their threats and creating new threat variants. Instead of paying the LockeR Ransomware ransom, computer users should take steps to protect their files by using a fully updated anti-malware application. A combination of file backups and a good anti-malware program can ensure that most computer users are well-protected from threats like the LockeR Ransomware.
SpyHunter Detects & Remove LockeR Ransomware
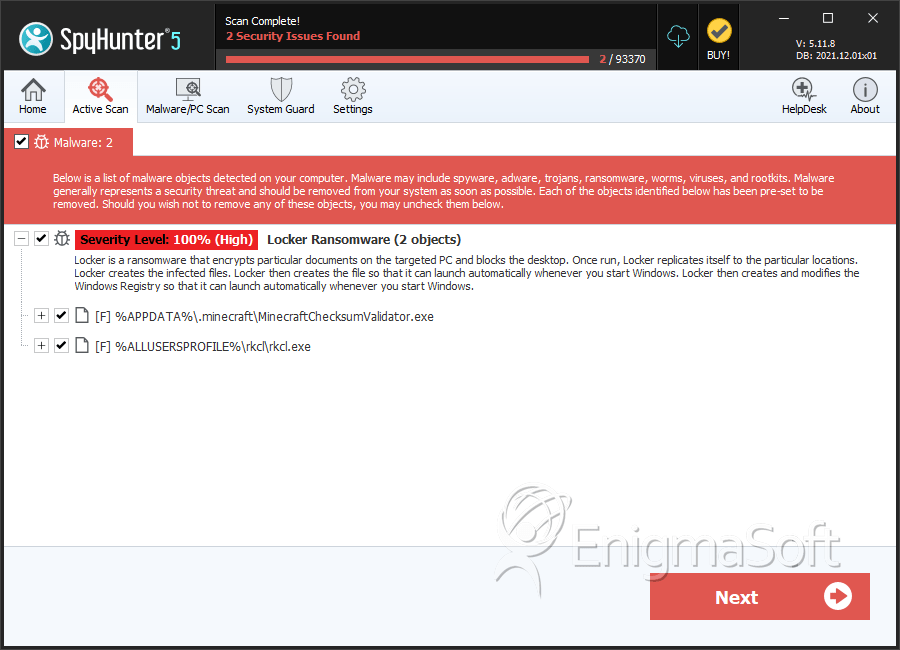
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | MinecraftChecksumValidator.exe | dbd136e27b9fdfc1e656ef2e2d96dd30 | 2,494 |
| 2. | MinecraftChecksumValidator.exe | b242a61cb751db5f99e5fc77270c1e07 | 30 |
| 3. | rkcl.exe | 4c135a6fca99ecc6396e695226ba20da | 1 |
| 4. | MinecraftChecksumValidator.exe | d111766f7aec4b00d6bb6e05a17cfef6 | 1 |
| 5. | MinecraftChecksumValidator.exe | 83ee68ce17e5ce5e9f63713006634610 | 1 |
