LockerGoga Ransomware
 While security researchers have expected ransomware attacks to slow down in 2019, recent ransomware outbreaks remind us that we must remain ever vigilant. One such outbreak that made headlines involved a ransomware known as LockerGoga. The ransomware targeted Norwegian manufacturing company Norsk Hydro, one of the world's top aluminum producers, forcing it to halt operations in multiple factories. This severely hindered the company's production and caused its stocks to fall by 0.8 percent. It is also suspected that a variant of LockerGoga was used to target French engineering company Altran Technologies earlier in January.
While security researchers have expected ransomware attacks to slow down in 2019, recent ransomware outbreaks remind us that we must remain ever vigilant. One such outbreak that made headlines involved a ransomware known as LockerGoga. The ransomware targeted Norwegian manufacturing company Norsk Hydro, one of the world's top aluminum producers, forcing it to halt operations in multiple factories. This severely hindered the company's production and caused its stocks to fall by 0.8 percent. It is also suspected that a variant of LockerGoga was used to target French engineering company Altran Technologies earlier in January.
Ransomware is a type of malware that encrypts the files of a computer system to extort a ransom from its target. There are multiple families of ransomware and an even higher number of variants within each of those families. Each of them uses a different set of tools and libraries to infect and encrypt a system. The ransomware in question, LockerGoga, was developed using C++ and implements the Crypto++ library for its encryption operations and the Boost library to manage system processes.
It is not yet known what vector the malware uses to infect a system. In the case of Altra Technologies, forensics suggest that the infection occurred through a phishing attack. It is also possible that the targeted network was already compromised through other hacking methods, creating a backdoor to drop the malware's payload. The executable also has a signed certificate issued by Sectigo. As of now, these certificates have been revoked.
Once in the system, LockerGoga uses a renamed version of the system administration tool PsEXEC to execute the payload. It is unknown how the malware spreads within a network; however, researchers believe that it spreads by using stolen remote desktop protocol (RDP). This would mean that the malware can spread from an infected terminal to others within the network.
When LockerGoga's code is executed, it will issue a command in the command line to relocate it to the TEMP folder and renames itself with a random number. The ransomware will then run two additional commands that use the Boost library to create a master process that enumerates files in the system and multiple child processes tasked with the encryption of data. The user will then be presented with a ransom note containing instructions on how to contact and pay the bad actor to decrypt the system.
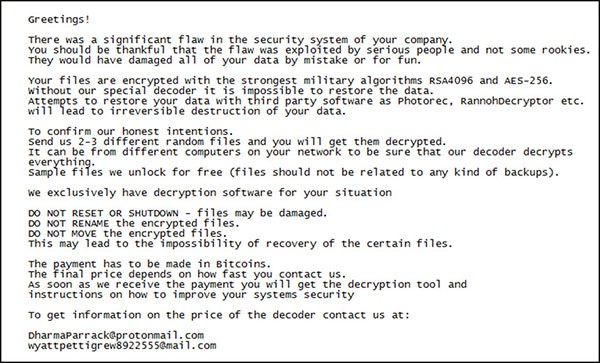
Figure 1. LockerGoga Ransom Note
After the encryption process is done, the encrypted files will have ".locked" extension appended to them. LockerGoga targets the following file extensions in a system:
.doc, .dot, .pot, .ppsx, .pptx, .posx, .potx, .sldx, .pdf, .db, .sql, .cs, .ts, .js, .py, .docb, .dotx, .docx, .xlt, .xltx, .xlsb, .xlw, .ppt, .pps, .wkb, .xlm, .xml, .xls, .xlsx.
While LockerGoga targets these particular extensions, it can encrypt any file in a hard drive. LockerGoga will also block outside network connections by disabling any Wi-Fi or Ethernet adaptors on the system. Specific variants of the ransomware, such as the one used at Norsk Hydro, will also log out all users and change their passwords to "HuHuHUHoHo283283@dJD".
A variation of the LockerGoga ransom note is as follows:
Greetings!
There was a significant flaw in the security system of your company.
You should be thankful that the flaw was exploited by serious people and not some rookies.
They would have damaged all of your data by mistake or for fun.
Your files are encrypted with the strongest military algorithms RSA4096 and AES-256.
Without our special decoder it is impossible to restore your data.
Attempts to restore your data with third party software as Photorec, RannohDecryptor etc. will lead to irreversible destruction of your data.
To confirm our honest intentions.
Send us 2-3 different random files and you will get them decrypted.
It can be from different computers on your network to be sure that our decoder decrypts everything.
Sample files we unlock for free (files should not be related to any kind of backups).
We exclusively have decryption software for your situation
DO NOT RESET OR SHUTDOWN - files may be damaged.
DO NOT RENAME the encrypted files.
DO NOT MOVE the encrypted files.
This may lead to the impossibility of recovery of the certain files.
To get information on the price of the decoder contact us at:
AbbsChevis@protonmail.com
IjuqodiSunovib98@o2.pl
The payment has to be made in Bitcoins.
The final price depends on how fast you contact us.
As soon as we receive the payment you will get the decryption tool and
instructions on how to improve your systems security
While some variants of LockerGoga seek to make a profit at their victim's expense, later variants seem only interested in disrupting operations by permanently "bricking" the system. This is done by encrypting the Boot Manager on windows systems which would render the machine inoperable and unable to display ransom notes with instructions for decryption.
Figure 2. Newer variants of LockerGoga can encrypt Windows Boot Manager and render the computer inoperable.

As in every case involving ransomware, it is not recommended for companies and individuals to pay up the ransom since it incentivizes cybercriminals to keep conducting these malware campaigns. Furthermore, there is no assurance that the perpetrators will decrypt the system. Having up-to-date back-ups of all your data along with good cybersecurity policies is the best way to combat ransomware incidents.
File System Details
| # | File Name |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|
| 1. | %APPDATA%\Local\Temp\tgytutrc8.exe |

