Karma Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 2 |
| First Seen: | November 15, 2016 |
| Last Seen: | December 8, 2020 |
| OS(es) Affected: | Windows |
The Karma Ransomware is a Trojan equipped with an encryption engine that it uses to lock your data and demand money to release the correct key and decryption software. The Karma Ransomware Trojan is pushed to users via software bundling and corrupted advertisements. We have received reports that the Karma Ransomware may be delivered to users as a program named Windows-Tuneup, which users are lead to believe is a system optimizer. Researchers reveal that the campaign to release the Karma Ransomware is related to the Windows-tuneup.com site and users are advised to be extra careful when downloading software from unfamiliar pages.
Table of Contents
Software Bundling and Corrupted Ads Serve the Karma Ransomware to Users
In-depth code analysis of the Karma Ransomware showed that the Trojan is developed by a programmed under the alias of SAFFRON-WOLF. There are not many cases where the authors of Ransomware leave their signature in their products as we have seen with the XRat Ransomware. The Karma Ransomware does not introduce new features on the Ransomware market and functions very similarly to many other Trojans like the '.GSupport3 File Extension' Ransomware and the Gingerbread Ransomware. However, the executable used by the Karma Ransomware come with a valid digital signature, which means its developer may have his hands on several misappropriated digital certificates for legitimate software.
The Karma Ransomware is Aimed at Broad Demographic Groups
The Karma Ransomware is using an AES-256 encryption algorithm to facilitate the encryption process, and the private key is sent to its 'Command and Control' servers. It is a common practice among encryption Trojan makers to store a temporary copy of the encryption key. The Karma Ransomware appears to be aimed at various types of users since it targets nearly six hundred file formats. Many of the file formats that the Karma Ransomware is supposed to encrypt are associated with software building kits, image and video manipulators, database managers and video games. The maker of the Karma Ransomware did not implement the usage of a custom file marker. Therefore, encrypted data containers look normal but the content of the file is altered and inaccessible. The ransom message is packed as '# DECRYPT MY FILES #.html,' which victims can find on their desktops and reads:
'KARMA
###################################
Is the content of the files that you looked for not readable?
It is normal because the data in your files have been encrypted.
Great!!!
You have turned to be a part of a big community #karma Ransomware.
Continue reading because this is the only way out.
###################################
!!! If you are reading this message it means the software
!!! "karma Ransomware" has been removed from your computer.
###################################
What is encryption?
Encryption is a reversible modification of information for security reasons but providing full access to it for authorized users.
To become an authorized user and keep the modification absolutely reversible (in other words to have a possibility to decrypt your files) you should have an individual private key.
But not only it.
It is required also to have the special decryption software (in your case "karma Decryptor" software) for safe and complete decryption of all your files and data.
###################################
Everything is clear for me but what should I do?
The first step is reading these instructions to the end.
Your files have been encrypted with the "karma Ransomware" software; the instructions ("# DECRYPT MY FILES #.html") on the desktop with your encrypted files is not a virus, it will help you.'
Users are Supposed to Pay the Ransom via a TOR-Hosted Portal
The author of the Karma Ransomware welcomes users to make a payment in Bitcoins using a portal hosted on the TOR Network. The amount of the ransom varies depending on the volume of data that is locked. Keep in mind that the Karma Ransomware can encrypt files on removable drives that were attached to your PC at the time of infection. However, paying the ransom should not be your first choice, and you could use backups and archives to restore your data. Services like Google Drive, Yandex Drive, and Dropbox can help you secure your files against attacks by the Karma Ransomware. You will need a reliable anti-malware tool to remove the Karma Ransomware Trojan securely.
SpyHunter Detects & Remove Karma Ransomware
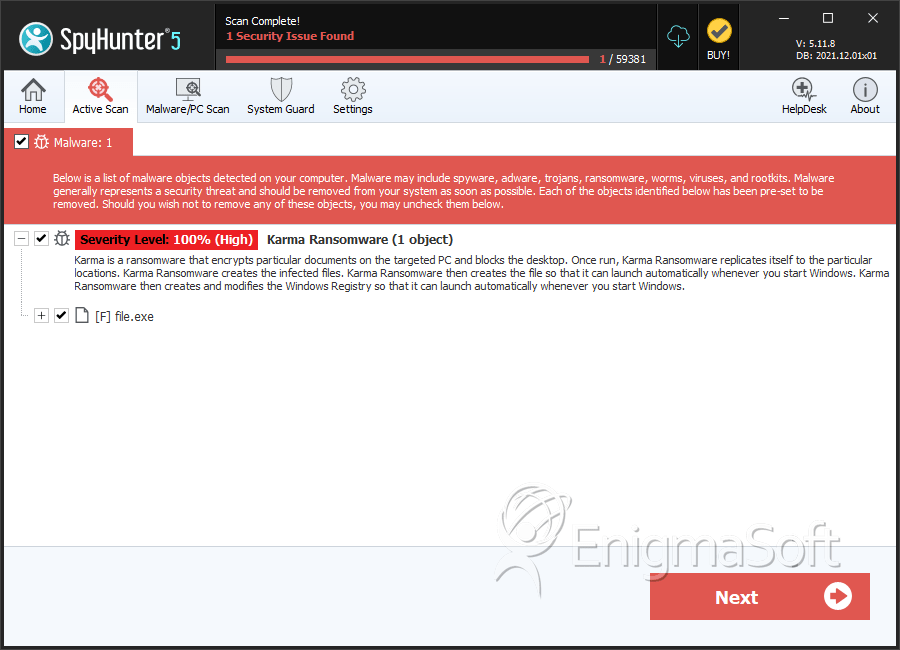
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | c0650bf3bcf21924c481051d2b487204 | 0 |
| 2. | file.exe | 1cb51c130e6f75f11c095b122e008bbc | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.