JiangLocker Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 4 |
| First Seen: | October 11, 2022 |
| Last Seen: | March 1, 2023 |
| OS(es) Affected: | Windows |
The JiangLocker Ransomware belongs to a class of malware threats designed specifically to target the data on breached devices. Through the use of a sufficiently strong cryptographic algorithm, these threats encrypt the data of their victims and render numerous file types - documents, archives, databases, PDFs, images, photos, audio and video files, completely inaccessible. The goal of the threat actors is to then use the locked files as leverage to extort money from the impacted users or corporate entities.
When JiangLocker Ransomware encrypts a file, it also marks it by appending '.jiang' to that file's original name. To ensure that its victims see the ransom note detailing the instructions of the cybercriminals, JiangLocker delivers a ransom-demanding message in three different ways. The threat will change the current desktop background of the infected device, create a file named 'read.ini,' and open a new pop-up window. The ransom notes found in the file and the pop-up window are identical.
The message shown as a desktop background warns victims that the only way to recover their files is to pay 0.5 Bitcoin (BTC) to the attackers. At the current exchange rate of the cryptocurrency, the demanded ransom amounts to more than $10,000. The money is supposed to be transmitted to the provided crypto-wallet address. The ransom notes found in the file and the pop-up window are identical. They mainly reiterate the same information but include more details about how victims can obtain Bitcoins.
The full text of the pop-up and file ransom notes is:
'What Happened to My Computer?
Your important files are encrypted.
Many of your documents, photos, videos, databases and other files are no longer accessible because they have been encrypted. Maybe you are
busy looking for a way to recover your files, but do not waste your time. Nobody can recover your files without our decryption service.Can I Recover My Files?
Sure. We guarantee that you can recover all your files safely and easily. But you have not so enough time.
If you want to decrypt all your files, you need to pay.How Do I Pay?
Payment is accepted in Bitcoin only. For more information, click .
Please check the current price of Bitcoin and buy some bitcoins. For more information, click .
And send the correct amount to the address specified in this window.
After your payment, click button.
Once the payment is checked, you can start decrypting your files immediately. it may take a few hours.We strongly recommend you to not remove this software, and disable your anti-virus for a while, until you pay and the payment gets processed. If your anti-virus gets updated and removes this software automatically, it will not be able to recover your files even if you pay!
To pay us, you have to use Bitcoin currency. You can easily buy Bitcoins at following sites:
hxxps://cex.io/
hxxps://www.binance.com/
hxxps://www.coinbase.com/After then, if you already have Bitcoins, pay our Bitcoin address.
Then, press the "Check Payment & Decrypt all Files" button. We will automatically decrypt your files, after bitcoin transfer.
Send 0.05 BTC to;
1PdLyXQb2LpApw3e8DLLRu6vWyWLibaXtJ'
The desktop background message is:
'!! ATTENTION !!
YOUR FILES HAVE BEEN ENCRYPTED!
All of your documents, photos, databases and other important files have been encrypted with RSA encryption.
You will not be able to recover your files without the private key which has been saved on our server.
An antivirus can not recover your files.
View the file "Decryption Notes" on your Desktop to fix this.
Send 0.05 BTC To: 1PdLyXQb2LpApw3e8DLLRu6vWyWLibaXtJ'
SpyHunter Detects & Remove JiangLocker Ransomware
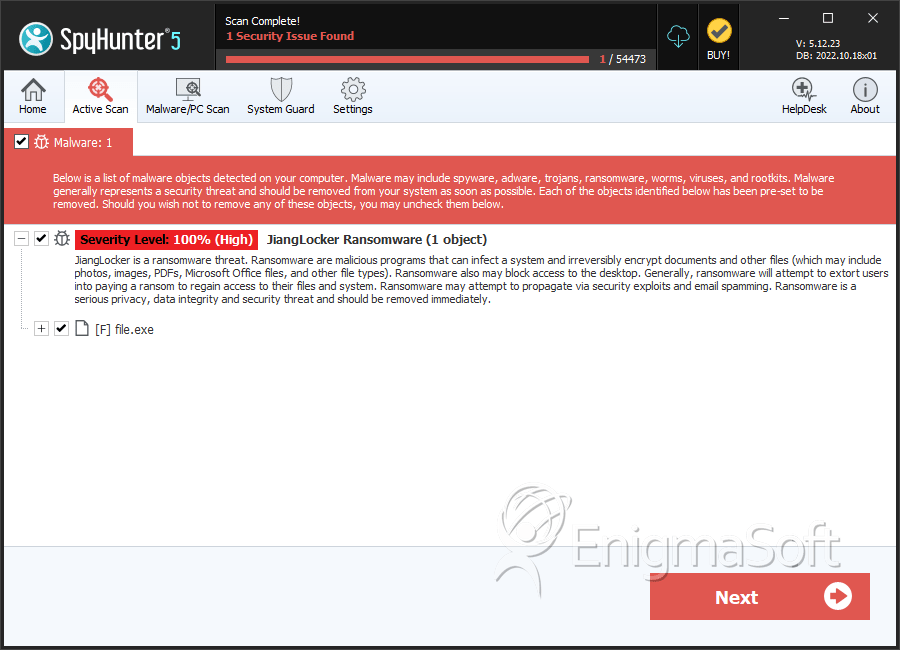
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | e60d3660ab7c20d15532426796c74a00 | 2 |

