JCry Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 7 |
| First Seen: | March 11, 2019 |
| Last Seen: | April 25, 2024 |
| OS(es) Affected: | Windows |
The JCry Ransomware is an encryption ransomware Trojan that seems to have been created for a purpose beyond monetization, with ideological goals in mind. The JCry Ransomware is being used to spread messages in favor of the Palestinian people along with carrying out an encryption attack. To this aim, the JCry Ransomware's intended victims are mainly located in Israel. The JCry Ransomware is being distributed under the hashtag '#OpJerusalem.'
Table of Contents
How the JCry Ransomware Trojan can Infect a Computer
Most encryption ransomware Trojans are distributed using spam email messages and social engineering. However, the JCry Ransomware's distribution methods seem to be more sophisticated than average. The criminals connected to the JCry Ransomware have compromised a popular Web plugin through a vulnerability in its security. Using this vulnerability, the criminals have managed to modify its DNS settings to allow it to display links to corrupted websites being used to distribute the JCry Ransomware through damaged scripts. If the victim's computer is running an operating system other than Windows, the victim's Web browser is redirected to an HTML Web page simply displaying the following text:
'Jerusalem is the capital of Palestine
#OpJerusalem'
If the victim's computer runs Windows, however, the JCry Ransomware is meant to be installed on the victim's computer to follow through with its attack. Some versions of the JCry Ransomware distribution method that have been observed are not effective in carrying out the infection currently, but this is certain to change.
Some Details about the JCry Ransomware Attack
If the JCry Ransomware is installed on the victim's computer, the JCry Ransomware will use a high effectual encryption algorithm to encrypt the user-generated files, which may include the following file types:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
The JCry Ransomwaremarks the files it targets with the file extension '.jcry.' The JCry Ransomware delivers its ransom note in the form of an HTML file named JCRY_Note.html, which demands a ransom payment of 500 USD. However, the criminals responsible for the JCry Ransomware attack have no way of knowing who has paid, signifying that the victims that make a payment cannot expect to have their data restored. Generally, computer users should avoid paying these ransoms since the criminals cannot be trusted to keep their promise to restore any data, but in this case, it is obvious especially that they have no intention of doing so. As with most encryption ransomware Trojans, the best protection against the JCry Ransomware is to have file backups stored on the cloud and a security program that can block the JCry Ransomware's distribution before it can be installed.
SpyHunter Detects & Remove JCry Ransomware
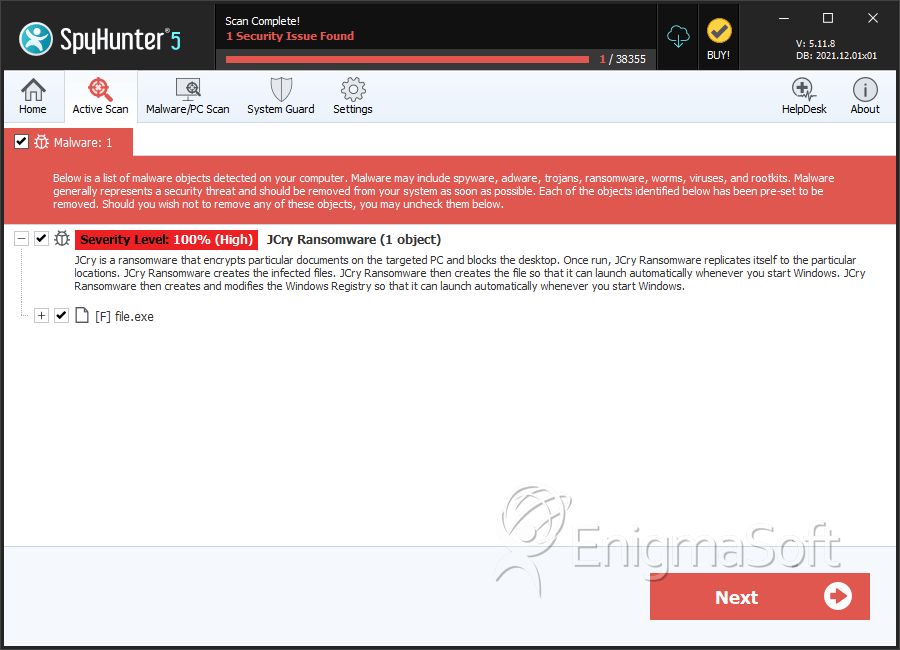
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 5b640be895c03f0d7f4e8ab7a1d82947 | 5b640be895c03f0d7f4e8ab7a1d82947 | 3 |
| 2. | file.exe | 6b4ed5d3fdfefa2a14635c177ea2c30d | 2 |
