Jaff Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 24 |
| First Seen: | May 12, 2017 |
| Last Seen: | May 30, 2023 |
| OS(es) Affected: | Windows |
The Jaff Ransomware is a file encoder Trojan that was reported by infected users in the second week of May 2017. Cyber scrutiny researchers alert that the main distribution method employed by the Jaff Ransomware's authors is spam emails that carry a corrupted DOCX file. A Microsoft Word document is sent out to users, which include an invitation to the user that suggests enabling the editing and macro functionalities in the word processor to load the file properly. Needless to say, if you go after the instructions, the installation of the Jaff Ransomware will be completed in seconds. We have received reports that the corrupted document may feature the following names:
- Copy_[RANDOM NUMBERS]
- Document_[RANDOM NUMBERS]
- File_[RANDOM NUMBERS]
- PDF_[RANDOM NUMBERS]
- Scan_[RANDOM NUMBERS]
The carrier email message may suggest that the attached document offers more information on an ongoing project, billing details, and photos sent from your friends on Facebook and Instagram. Web surfers should not open spam emails that invite them to open a suspicious document, and they should double-check with their friends if they have sent them a package with images. The Jaff Ransomware is classified as a mid-tier crypto-threat, which is programmed to encode 421 types of data containers. Analysis of the distribution network and cases that involve the Jaff Ransomware show that it is aimed at regular users based in North America and Western Europe primarily. Samples of the Trojan have been found to use the following executable on infected devices:
- Rcfcngzxx.exe
- jaffdecryptor.exe
- pitupi20.exe
- 924c84415.exe
The Jaff Ransomware is programmed to run in the system background and can run on the latest versions of Windows, as well as the old Windows XP. Objects that are encoded by the Trojan feature a change in their filenames and include the '.jaff' extension. For example, 'Monomorium pharaonis - Pharoh Ant.pptx' is renamed to 'Monomorium pharaonis - Pharoh Ant.pptx.jaff' and the file lacks a thumbnail. Windows Explorer might show the encoded data as generic white icons and refuse to open the file due to corruption. The threat creates the following directories where the ransom notifications are hosted:
- C:\ProgramData\Rondo\
- C:\ProgramData\Rondo\WallpapeR.bmp\
- C:\ProgramData\Rondo\backup.om\
Infected users may notice that the following files are loaded on the screen after the encryption procedure is completed:
- ReadMe.bm
- ReadMe.html
- ReadMe.txt
- WallpapeR.bmp
We have seen the Jaff Ransomware launch the default Internet client to load 'ReadMe.html' and show the following message:
'jaff decryptor system
Files are encrypted!
To decrypt flies you need to obtain the private key.
The only copy of the private key, which will allow you to decrypt your files, is located on a secret server in the Internet
You must install Tor Browser: https://www.torproject.org/download/download-easy.html.en
After instalation, run the Tor Browser and enter address: [REDACTED]
Follow the instruction on the web-site.
Your decrypt ID: [10 RANDOM DIGITS]'
The threat suggests users download the TOR Browser and open the payment portal on the TOR anonymization network. We have seen the operators of the 'Crypt32@mail.ru' Ransomware and the Sage 2.0 Ransomware use TOR-based payment portals for anti-trackback purposes. Cyber security analysts that worked on samples of the Jaff Ransomware report that it is impossible to decode the affected data since the threat uses the secure AES-256 cryptographic algorithm and the decryption key is not saved on the compromised system. At the time of writing, the ransom fee is set to 2 Bitcoins, which is priced at 3630 USD/3337 EUR on markets like Blockchain.info. We do not recommend users deliver payment since the 'jaff decryptor system' might be a hoax. You might be able to recover from the attack with Jaff Ransomware by running a complete system scan using a trusted anti-malware tool and loading backup images.
Table of Contents
SpyHunter Detects & Remove Jaff Ransomware
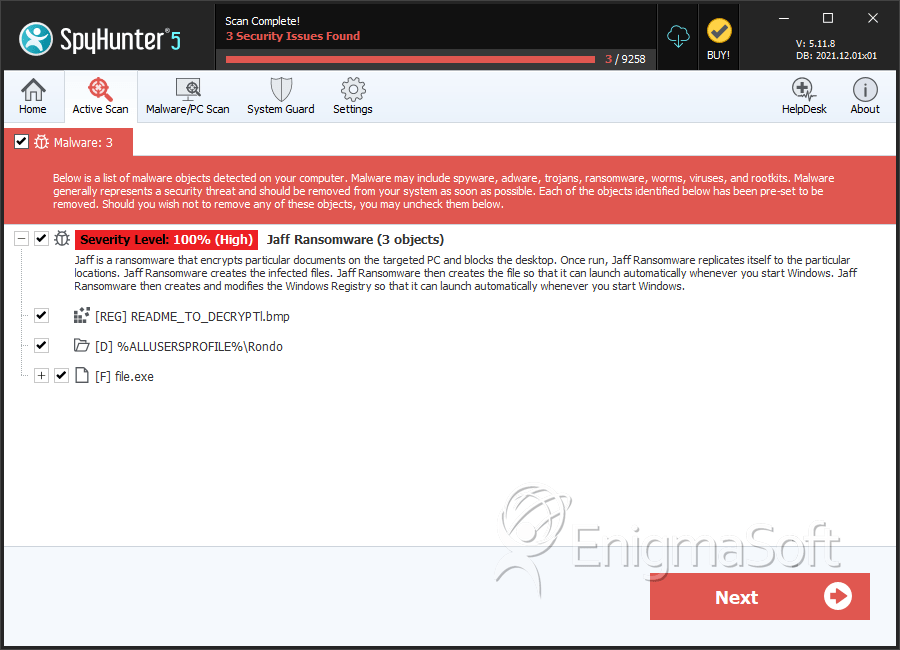
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 942c6a039724ed5326c3c247bfce3461 | 0 |
| 2. | file.exe | 63ff8e84e4aea1217eb0490757a49ae7 | 0 |
| 3. | file.exe | bf0455ac54931da70445d71ad9ebfe2d | 0 |
| 4. | file.exe | 56185d85038547ec352a0f39396a37a7 | 0 |
| 5. | file.exe | 0a03c3bdae435d282508a3870bb825e7 | 0 |
Registry Details
Directories
Jaff Ransomware may create the following directory or directories:
| %ALLUSERSPROFILE%\Rondo |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.